Chapter 7. Networked Hosts and Network Configuration
This chapter covers the following A+ 220-1001 exam objectives:
• 2.5 – Summarize the properties and purposes of services provided by networked hosts.
• 2.6 – Explain common network configuration concepts.
Let’s get a little bit deeper into networking. In this chapter we’ll dig into the services provided by computer servers. I’m referring to commonly known servers such as web servers, file servers, and e-mail servers; but also, servers that provide less-known underlying services, such as DHCP servers and authentication servers. In the second portion we’ll discuss the foundation for these services, especially TCP/IP configurations: IP addressing, dynamic IP assignment, name to IP resolution, and networking technologies such as VPNs and VLANs.
2.5 – Summarize the properties and purposes of services provided by networked hosts.
ExamAlert
Objective 2.5 concentrates on the following concepts: server roles (web, file, print, DHCP, DNS, proxy, mail, authentication, syslog), Internet appliances, and legacy/embedded systems.
If it’s not stored locally, then we look to servers to provide the data we need. In this objective we’ll discuss the various server roles that you should know for the exam: web servers which provide websites and e-commerce; file servers that provide access to data files of all kinds; e-mail servers that provide for a central administration and storage point for e-mail messages; and print servers that provide the ability to print to remote printers. Getting a bit more technical, we’ll cover some of the essential servers on a mid-sized to large computer network including: DHCP, DNS, proxy, syslog, and authentication servers. At the end, we’ll briefly discuss Internet appliances and legacy/embedded systems.
Server Roles
Servers take care of centralizing data, allowing access to the network, making connections to printers, controlling the flow of e-mail, and much more. Whatever the role, the concept of the server is to do this in a centralized fashion, reducing the burden on client computers. Regardless of whether the server is in the organization’s LAN or in the cloud, they will have the same purpose.
File Servers
File servers store, transfer, migrate, synchronize, and archive files. Any computer can act as a file server of sorts. All you need to do is create a share on your local system and point remote computers to that share, either by browsing or through a mapped network drive. On a typical Windows client computer, however, those shares will be limited in the amount of simultaneous connections allowed (usually 20 maximum). So, for larger network environments, we need a real server of some sort. Examples of actual server software include Microsoft Windows Server, macOS Server, and the various types of Linux server versions (for example, Red Hat or CentOS), not to mention Unix. As with most servers, the file server can be a physical box, or a virtual machine, and can be located within your LAN or on the cloud.
Note
You could also build a network-attached storage (NAS) server. That’s a basic box that often contains 2 or more hard drives and connects directly to the network. It will usually run some variant of Linux. We’ll discuss NAS more in Chapter 10, “RAM and Storage.”
Web Servers
The web server is the one that houses the website of an organization. Examples of web servers include Microsoft’s Internet Information Services (IIS) which is part of Windows Server, Apache HTTP Server (Linux), and lighttpd (FreeBSD). Small and mid-sized companies will often host their websites with an external provider. Larger companies might choose to host their websites on web servers physically located in their data center, though many also choose to use the cloud. An organization’s choice is usually dictated by the amount of resources and manpower that they possess.
Print Servers
Print servers are basic servers that take control of multiple printers on the network. All caching of information, spooling, printer pooling, sharing, and permissions is controlled centrally by the print server. While a Windows client computer (or other client) could act as a print server, and you can also purchase a basic print server device that plugs into your network, enterprise-level print servers will run software such as Windows Server, so that they can handle lots of simultaneous print requests from client computers.
Mail Servers
Mail servers (or e-mail servers) are part of the message server family. When we refer to a message server, we mean any server that deals with e-mail, faxing, texting, chatting, and so on. But for the purposes of the A+ exams, we concentrate strictly on the e-mail server. The most common of these is Microsoft Exchange. An Exchange Server might run POP3, SMTP, and IMAP, and allow for Outlook connections via a web browser. That’s a lot of protocols running. So, it’s not surprising to hear some Exchange admins confess that running an e-mail server can be difficult at times. For the A+ exams you should know how to connect a client to an e-mail server such as Microsoft Exchange. This is done by using appropriate e-mail client software (such as Outlook) and knowing the server name, protocols and ports used, the username and password, and whether there is additional security involved. For more about e-mail client configuration, see Chapter 4, “Smartphones, Tablets, and Other Mobile Devices, Part 2.”
Proxy Servers
A proxy server is used primarily as a go-between for the client and the website accessed. It is commonly used to cache information so that another user accessing the same web page won’t have to get it from the Internet, because it already exists on the proxy server, which increases general performance and efficiency. For a client computer to use a proxy server, the web browser needs to be configured properly. (We’ll show this in Chapter 29, “Windows Networking and Application Installation”.) In addition, the proxy server can analyze data as it passes through and filter it accordingly—this is referred to as content-filtering. You can also have proxies for FTP, SMTP, and other protocols. There are also proxies that reside on the Internet, designed to hide users’ IP addresses, allowing users to browse the web anonymously. Quite often, organizations will block these types of connections.
To protect a web server, an organization might implement a reverse proxy. This device is placed within the area of the network where the web server resides. Requests from clients on the Internet are forwarded by the reverse proxy to the web server so that the clients will be unaware of the identity of the web server. Reverse proxies can also be used for encryption of web sessions, and load balancing: where client requests can be distributed to multiple web servers.
Authentication Servers
An authentication server acts as a central repository of user accounts and computer accounts on the network. All users log on to this server. The most common example of this would be a Windows Server system that has been promoted to a domain controller (meaning it runs Active Directory). This type of server validates the users that attempt to log on. Authentication servers utilize some kind of authentication protocol such as the Lightweight Directory Access Protocol (LDAP), or Kerberos, or both. The Windows domain controller is an example of an authentication server that uses LDAP.
DHCP Servers
Some servers do have less tangible duties—but not any less important. For example, the DHCP server is in charge of handing out IP addresses to clients. But don’t underestimate this function; if an organization has a couple thousand computers that rely on obtaining IP addresses from a DHCP server, it becomes one of the most important servers on the network. If it fails, computers will have great difficulty doing anything on the network. DHCP server functionality is built into Windows and Linux servers, SOHO routers, and many other devices. Whenever a device or computer obtains an IP address automatically, chances are that a DHCP server was involved.
DNS Servers
A domain name system (DNS) server takes care of resolving domain names to IP addresses. For example:
davidlprowse.com = 216.97.236.245
Try running the ping command in the Command Prompt and ping a domain name of your choice. For example:
ping example.com
The results should display the IP address of that domain—this is a basic example of DNS being performed. DNS servers also take care of reverse DNS; when IP addresses are resolved to domain name.
In smaller networks, this server is at the ISP. However, larger networks might decide to run a DNS server internally. In fact, it becomes a necessity if the company has a domain controller, because the domain relies on DNS name resolutions for just about everything that needs to be accessed. DNS functionality is built into most server operating systems such as Windows Server.
Syslog Servers
Syslog is a protocol that can take logged event information from a router or other network device and send that to a logging server—also known as a Syslog server. The Syslog server uses special software to store these logs in real time and is designed in a way that is easy for administrators to read, analyze, and save the information, which might consist of status, events, diagnostics, entry attempts, and so on. Best of all, the administrator can do all this from his or her workstation, without having to log into each network device separately. Examples of Syslog software include Kiwi Syslog Server, PRTG, and Syslog Watcher.
ExamAlert
Know the differences between file servers, web servers, print servers, e-mail servers, proxy servers, authentication servers, DHCP servers, DNS servers, and Syslog servers. You might also want to tie in these concepts to the ports that the servers use, which can be found in Chapter 5, “Ports, Protocols, and Network Devices,”
So, there’s a little primer on servers. The server is the home of the systems administrator/network administrator. A lot of you reading this are probably very interested in servers. The Core 1 (220-1001) A+ exam focuses more on the client side of things, but you should attempt to learn as much as you can about the various servers we just discussed. Ultimately, you will be working on them!
Internet Appliances
There are a variety of security devices that can be used to block unauthorized access, including firewalls, UTMs, IDS and IPS solutions, and endpoint management servers. These are all examples of Internet appliances—or, more accurately, Internet security appliances.
The network firewall is first and foremost; almost every organization has one protecting its network. These are usually rack-mountable devices that connect to the LAN on one side and to the Internet on the other (and possibly to a DMZ or other secondary network using a third connection). Their primary function is to close ports (such as HTTP port 80) so that unwanted intrusion can be prevented. A typical firewall implementation closes all inbound ports so that external users are blocked from access to the LAN of an organization. However, in some cases, you will find that a port on a firewall was opened previously to allow communication by a service or application that is no longer in use. If that happens, you need to disable (or close) that port or delete the rule that was created for that type of communication. These rules are also known as access control lists (ACLs).
A firewall can be part of a unified threat management (UTM) gateway solution as well. UTM is the evolution of the firewall, incorporating the features of the firewall along with antivirus, antispam, content filtering, and intrusion prevention for the entire network. It might also incorporate data loss prevention (DLP) by way of content inspection. The idea behind UTM is that it can take the place of several units doing separate tasks and consolidate them into one easily administered system. The drawback to this is that it can act as a single point of failure. So many organizations will consider secondary UTM units or fallback firewalls.
Note
You might not hear the term UTM used as often today, but it’s still on the A+ objectives so know it!
The A+ objectives also require that you understand two other terms, IDS and IPS, and that you know the difference between them. An intrusion detection system (IDS) can determine whether an unauthorized person has attempted to access the network and then alert the systems administrator of its findings. In this case, an admin is alerted to the problem, but the unauthorized user might actually gain access to the network; the damage might be done before the admin has a chance to rectify the situation. Building on this concept, an intrusion prevention system (IPS) will not only detect unauthorized access to the network, it will attempt to thwart it, making the admin’s job somewhat easier. IDS and IPS solutions are available as security appliances for the entire network and, in this case, are also referred to as network-based IDS (NIDS) and network-based IPS (NIPS), respectively. They are often incorporated into UTM devices, most commonly NIPS. However, IDS and IPS solutions are also available for individual hosts. In this case, they are referred to as host-based IDS (HIDS) and host-based IPS (HIPS).
Finally, know the term endpoint management server. That type of server is one element of an endpoint management solution. Endpoint management (or endpoint security management) is a policy-based approach to network security. It requires endpoint devices (meaning PCs, laptops, mobile devices) to meet particular criteria before they can be granted access to network resources. Endpoint management servers are servers that centrally control the discovery of endpoint devices, and the deployment and updating of those devices’ security software and features. Companies such as Check Point and Sophos offer endpoint management solutions. Among other tasks, the endpoint management server can handle the updating of endpoint protection platforms. These platforms should also be installed to all endpoints, and should be updated across the board in a synchronous fashion. Examples of endpoint protection platforms are McAfee, Norton (Symantec), and Kaspersky. These are generally all-in one solutions that have antivirus, anti-spyware, personal firewalls, spam protection, and so on. They might simply be referred to as anti-malware suites.
ExamAlert
Know the differences between the following: firewall, UTM, IDS and IPS, and endpoint management server.
Embedded/Legacy Systems
Embedded systems are devices that have an integrated CPU and RAM which can process information internally without the need for a controlling system. They are commonly found in: home appliances, office automation, thin clients, security systems, telecommunications, automotive, medical, assembly systems, and much more.
One place where you will find embedded systems is in heating, ventilation, and air conditioning (HVAC). Taking it to the next level, larger infrastructures will often use a Supervisory Control and Data Acquisition System (SCADA). These are found in electrical power grids, water treatment plants, gas/oil pipelines, hydroelectric systems, sewage systems, traffic systems, building controls, and so on. Compared to typical home offices and small offices, SCADA solutions must be heavily secured because they are often used in protected environments an infrastructures. Teams of engineers are employed to design and secure these SCADA solutions.
Some buildings might require legacy systems to control their older HVAC, plumbing, and other technologies. Some of these legacy systems might be single board computers such as the PC/104 embedded system which will typically run at 33 MHz and have 16 to 32 MB of RAM. Note that the last sentence read MHz and MB—instead of GHz and GB—that should help to define the term legacy! These boards can go bad over time and have to be replaced. Or, a particular technology might be controlled by a legacy thin client computer with an embedded operating system—and no hard drive. These are also generally single board designs where a failure means a total board or unit replacement. If you are in charge of this type of technology, be ready to scour the Internet and locate quality distributors so that you can get quality replacements at a decent price.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. While looking at the details of a server in your provider’s control panel you notice that it says “Apache” in the HTTP summary. What kind of server is this?
![]() A. File server
A. File server
![]() B. Web server
B. Web server
![]() C. E-mail server
C. E-mail server
![]() D. Authentication server
D. Authentication server
2. Which type of server acts as a go-between for clients and websites?
![]() A. Proxy server
A. Proxy server
![]() B. Print server
B. Print server
![]() C. Syslog server
C. Syslog server
![]() D. DHCP server
D. DHCP server
3. Which type of server runs Microsoft Exchange?
![]() A. File server
A. File server
![]() B. Authentication server
B. Authentication server
![]() C. E-mail server
C. E-mail server
![]() D. Web server
D. Web server
![]() E. SCADA
E. SCADA
Cram Quiz Answers
1. B. Apache is a type of web server that runs on Linux. It is also known as Apache HTTP Server. File servers are used to store and transfer files but not websites. E-mail servers deal with the sending and receiving of electronic mail via POP3, IMAP, and HTTP. Authentication servers verify the identity of users logging in and computers on the network.
2. A. A proxy server is a caching server used to store commonly accessed websites by clients. It can be incorporated into a web server but often it runs as a stand-alone server. A print server manages network printers and their spooling of print jobs, priorities, and so on. A Syslog server gathers logging data from network devices and allows for the easy analysis of those logs from a client workstation. A DHCP server hands out IP addresses (and other TCP/IP information) to client computers.
3. C. Microsoft Exchange is a type of e-mail server software. While you could run multiple services on a single server—for example, you could run the web server and e-mail server on the same machine—it isn’t recommended. Unless you have a small office, all servers (such as file servers, authentication servers, e-mail servers, DHCP servers, and so on) should be separate entities. SCADA is not a server—it stands for Supervisory Control and Data Acquisition System, a type of system used to control larger organizations’ infrastructures such as heating/cooling, electricity, and so on.
2.6 – Explain common network configuration concepts
ExamAlert
Objective 2.6 focuses on the following concepts: IP addressing (static, dynamic, APIPA, link local), DNS, DHCP, IPv4, IPv6, subnet mask, gateway, VPN, VLAN, and NAT.
In this objective we’ll discuss the core of networking for most computers: IP addressing. Without IP addresses our computers can’t communicate—so it’s vital that you know IP addressing frontwards and backwards. We’ll also touch on some network configurations that use IP but in a more secure way, such as VPNs and VLANs. This could be considered one of the most important sections in the book, and it’s packed with information. It’s time to network!
Configuring IPv4
Configuring IP works the same way in most versions of Windows. First, we navigate to the Internet Protocol (TCP/IP) Properties window, which I will often refer to as the IP Properties dialog box. To do this, go to Control Panel > Network and Internet > Network and Sharing Center, and then select the Change Adapter Settings link. Then right-click the Ethernet icon (or Local Area Connection icon) and select Properties. Finally, highlight Internet Protocol Version 4 and then click the Properties button.
Note
Navigation may differ slightly depending on the version of Windows and the way it is configured. Be ready for alterations over time, and be ready to use the search tool to simplify the process (or the Run prompt whenever possible!)
The first item to be configured is the IP address, which is the unique assigned number of your computer on the network. IPv4 IP addresses consist of four octets, with each octet’s value ranging between 0 and 255. Each number is separated by a dot (for example, 192.168.0.100). The binary equivalent of 0–255 would be 00000000 through 11111111. For example, 192 is equal to 11000000 in binary. Because each octet contains 8 bits and there are four octets, the IP address collectively is a 32-bit number but is normally expressed in dotted-decimal notation.
There are two main types of addresses: dynamic and static. Dynamically assigned addresses are more common for a client computer; this is when the computer seeks out a DHCP server so that it can get its IP information automatically. Figure 7.1 shows a radio button labeled Obtain an IP Address Automatically. When you select this, the rest of the information becomes grayed out and the computer attempts to get that IP information from a DHCP server (such as a SOHO router or Windows Server). That DHCP server will have a range of IP addresses that was configured by an administrator—also known as a DHCP scope. The administrator might also configure DHCP reservations, which are IP addresses within the DHCP scope that are permanently reserved for special computers which need to use DHCP, but don’t want the IP address to change over time (which can happen periodically in DHCP environments).
For client computers, DHCP is common; in fact, it’s the default configuration for Windows. On the other hand, static addresses are generated when we configure the IP information manually. Figure 7.1 shows an example of statically configured IP settings. In the figure, we configured the computer to use the address 192.168.0.100, but the IP address differs from machine to machine depending on several factors. Remember that the address should be unique for each computer on the network.
ExamAlert
Know the difference between static and dynamic IP addresses.
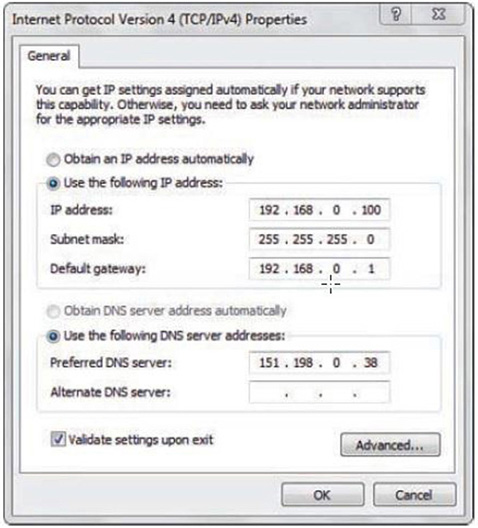
Figure 7.1 IP Properties dialog box in Windows
IP addresses can also be self-assigned by the computer. In Windows, this is known as automatic private IP addressing (APIPA), and it occurs when a computer cannot contact a DHCP server to obtain an IP address. When APIPA self-assigns an address, it will be on the 169.254.0.0 network. Addresses on this network are also known as link-local addresses.
IP addresses are divided into two sections: the network portion, which is the number of the network the computer is on, and the host portion, which is the individual number of the computer. The subnet mask defines which portion of the IP address is the network number and which portion is the individual host number. In this case, the subnet mask is 255.255.255.0. The 255s indicate the network portion of the IP address. So, 192.168.0 is the network this computer is a member of. The zeros (in this case, there is only one of them) indicate the host number, so 100 is the individual number of this computer. Quite often the subnet mask will be configured automatically by Windows after you type the IP address.
The gateway address is the IP address of the host that enables access to the Internet or to other networks. The IP address of the gateway should always be on the same network as the computer(s) connecting to it. In Figure 7.1, we know it is because the first three octets are 192.168.0. If a computer is not configured with a default gateway address, it cannot connect to the Internet.
ExamAlert
To use the gateway, computers must be on the same network number as the gateway device.
The DNS server address is the IP address of the host that takes care of domain name translation to IP. When you use your browser to connect to a website, you might type something like www.davidlprowse.com. What you need to remember, however, is that computers actually communicate by IP address, not by name. So, the DNS server takes care of translating the name davidlprowse.com to its corresponding IP address and forwarding that information back to your computer. When your computer knows the IP address of the website, it can start a session with the website and transmit and receive files. Notice in Figure 7.1 that the DNS server address is on a completely different network than our computer. This is typical; in this case, the DNS server is run by the Internet service provider (ISP) that provides me with my Internet connection. However, DNS servers can also be run internally by a company; this happens more often with larger companies.
You will also note a checkbox labeled Validate settings upon exit. If you set up a static IP address on a computer, you should select this checkbox. This way, Windows will check whether the configuration works properly and will let you know when any basic errors arise. Who knows, the IP configuration might have an incorrect DNS server, gateway address, or IP network number.
ExamAlert
Know where and how to configure client-side DNS and DHCP settings.
If your IP Properties dialog box is set to Obtain an IP address automatically, you will see the Alternate Configuration tab. This allows you to have a secondary IP configuration. Let’s say there was a scenario in which you used a laptop at work and got your IP address from a DHCP server, but you also go on the road. The alternate configuration would kick in automatically when you are away from the office and allow you access to the Internet or to virtual private networks, depending on how you configure it. The alternate configuration can be on a wholly different IP network than the main configuration.
Speaking of secondary IPs, every computer running TCP/IP has an additional address known as a loopback address. By default, this is 127.0.0.1 and can be used to test TCP/IP on the local machine regardless of whether the system is plugged into the network. Try running a ping 127.0.0.1 or a ping loopback -4 in the Command Prompt to test your system internally. Remember—replies are good!
Configuring IPv6
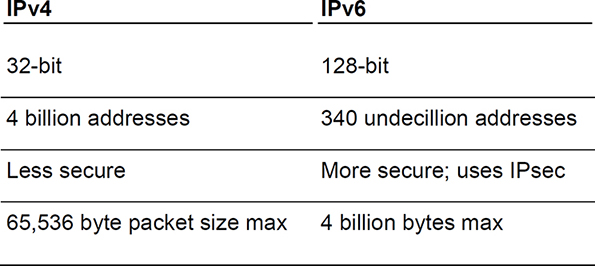
Though acceptance has been slow over the years, IPv6 is the next generation of IP addressing. Used on the Internet and on some LANs and WANs, it is designed to meet the inadequacies of IPv4. One of the main reasons for the development of IPv6 was the rapidly approaching global shortage of IPv4 addresses. Where IPv4 (a 32-bit system) can have approximately 4 billion total theoretical addresses, IPv6 (128-bit) can have a total of 340 undecillion theoretical addresses—a far greater total. Various limitations of the system will drastically reduce that number, but the remaining result is still orders of magnitude above and beyond the IPv4 system. However, IPv6 is also known for security. One feature of IPv6 security is IPsec, which authenticates and encrypts data packets that are sent over IP networks. IPsec is a fundamental piece of the IPv6 puzzle and if used properly, it can offer much more secure communications than IPv4. IPv6 also supports larger packet sizes, which are known as jumbograms. Table 7.1 summarizes some of the differences between IPv4 and IPv6.
Table 7.1 IPv4 Versus IPv6
IPv6 addresses are 128-bit hexadecimal numbers that are divided into eight groups of four numbers each. The most commonly used type is the unicast address, which defines a single IP address on a single interface (such as a network adapter). Windows auto-configures a unicast address when IPv6 is installed. The address will start with FE80, FE90, FEA0, or FEB0. Collectively, this range is shown as FE80::/10 and it comprises all of the link-local addresses for IPv6. These link-local addresses are often based on the MAC address of the network adapter. Every Windows computer with IPv6 installed also receives a loopback address that is ::1. The IPv6 address ::1 is the equivalent to IPv4’s loopback address of 127.0.0.1. To test it, type ping ::1 or ping loopback -6 in the Command Prompt.
ExamAlert
Know the loopback addresses for IPv6 and IPv4.
Here’s an example of an IPv6 address:
2001:7120:0000:8001:0000:0000:0000:1F10
IPv6 addresses are broken down into three sections: the global routing prefix (in this case, 2001:7120:0000); a subnet that is 8001; and the individual interface ID, shown as 0000:0000:0000:1F10.
This is the full address, but you will more commonly see truncated addresses. There are two ways to truncate, or shorten, an IPv6 address. The first is to remove leading zeros. Any group of 4 zeros can be truncated to a single zero; basically zero is always zero, so the additional zeros are not necessary. Also, one consecutive group of zeros can be truncated as a double colon (::). The example shows 12 consecutive zeros that can be truncated simply to a double colon. (A double colon can be used only once in an address.) The following is the end result of both of these abbreviations:
2001:7120:0:8001::1F10
ExamAlert
Understand how IPv6 addresses can be truncated.
Though it is not common, IPv6 addresses can be assigned statically as well; this can be done within the Internet Protocol Version 6 Properties dialog box, which can be accessed from Local Area Connection Properties (IPv6 is listed near to IPv4).
VLANs
A virtual LAN (VLAN) is implemented primarily to segment the network. But it can also be used to reduce data collisions, organize the network, potentially boost performance, and possibly, increase security. A device such as a switch will often control the VLAN. A VLAN compartmentalizes the network and can isolate traffic. VLANs can be set up in a physical manner; an example of this would be the port-based VLAN, where switch ports are grouped and configured to act as individual VLANs. To do this you would need a managed switch—one that you can log into and configure for VLAN use.
There are also logical types of VLANs, such as protocol-based VLANs. A VLAN can be set up in such a way where each VLAN is on a different IP network number: for example, 192.168.0.0, 192.168.1.0, 192.168.2.0, and so on. Or, you could take it to the next level and incorporate a separate technology called IP subnetting. This is when you divide the network into two or more sub-networks by changing the subnet mask that is used: for example, from 255.255.0.0 to 255.255.240.0. Some administrators prefer IP subnetting over VLANs, and some use them together: for example, a group of physical port-based VLANs each of which is on a different IP subnetwork.
Note
VLANs and subnetting go a bit beyond what a typical A+ technician will be asked to perform, but you should know the basic definitions for these. To learn more about subnetting see my blog post here: https://dprocomputer.com/blog/?p=1185.
VPNs
Let’s say you want to connect to your network, but you are at a remote location. Enter the VPN. Virtual private networks (VPNs) were developed so that telecommuters, salespeople, and others could connect to the office from a remote location. If set up properly, the remote logon connection is seamless and appears as if you are actually at the LAN in the office. You log on just as you would if you were at your desk at headquarters. VPNs give the user access to all the resources that they get when logging on locally. VPNs take advantage of the infrastructure of the Internet and fast connections (such as cable, fiber, DSL, and so on). A VPN connection can be identified by an additional network connection in the Notification Area, as an additional network connection when using the ipconfig command, or as a pop-up window that comes up during the logon process. Connections to VPNs can be initiated by navigating to the Network and Sharing Center and selecting the Set Up a New Connection or Network link. From there, you would opt for Connect to a Workplace and then select VPN. There are also third-party offerings from companies such as Cisco, Check Point, and so on. Either way, you would need to know the IP address or name of the VPN server you are connecting to as well as a username and password to get in. Alternate IP configurations are sometimes used with VPN connections, so that the main IP configuration is not disturbed, especially if it is configured statically. We’ll show how to setup a VPN connection in Chapter 29, “Windows Networking & Application Installation.”
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of these addresses needs to be configured to enable a computer access to the Internet or to other networks?
![]() A. Subnet mask
A. Subnet mask
![]() B. Gateway address
B. Gateway address
![]() C. DNS address
C. DNS address
![]() D. MAC address
D. MAC address
2. Which technology assigns addresses on the 169.254.0.0 network number?
![]() A. DHCP
A. DHCP
![]() B. Static IP
B. Static IP
![]() C. APIPA
C. APIPA
![]() D. Class B
D. Class B
3. You want to test the local loopback IPv6 address. Which address would you use?
![]() A. 127.0.0.1
A. 127.0.0.1
![]() B. ::1
B. ::1
![]() C. FE80::/10
C. FE80::/10
![]() D. ::0
D. ::0
4. You have been tasked with compartmentalizing the network. Which of the following technologies should you use?
![]() A. APIPA
A. APIPA
![]() B. VPN
B. VPN
![]() C. VLAN
C. VLAN
![]() D. IPv6
D. IPv6
Cram Quiz Answers
1. B. The gateway address must be configured to enable a computer access to the Internet through the gateway device. By default, the subnet mask defines the IP address’s network and host portions. The DNS server takes care of name resolution. The MAC address is the address that is burned into the network adapter; it is configured at the manufacturer.
2. C. If you see an address with 169.254 as the first two octets, then it is Automatic Private IP Addressing (APIPA). This is also the link-local range for IPv4. The Dynamic Host Configuration Protocol (DHCP) assigns IP addresses automatically to clients but by default does not use the 169.254 network number. Static IP addresses are configured manually by the user in the IP Properties window. Class B is a range of IP networks from 128 through 191.
3. B. You would use the ::1 address. That is the local loopback address for IPv6. 127.0.0.1 is the local loopback for IPv4. FE80::/10 is the range of unicast auto-configured addresses. ::0 is not valid but looks similar to how multiple zeros can be truncated with a double colon.
4. C. You would create a virtual LAN (VLAN). Another valid option would be to implement IP subnetting. APIPA (also known as link-local) is an IP technology that auto-assigns addresses on the 169.254 network. A virtual private network (VPN) allows remote clients to connect to a network over the Internet using a secure tunnel. IPv6 in of itself does not compartmentalize the network. However, an IPv6 network that has been subnetted would be acceptable.