Chapter 5. Ports, Protocols, and Network Devices
This chapter covers the following A+ 220-1001 exam objectives:
• 2.1 – Compare and contrast TCP and UDP ports, protocols, and their purposes.
• 2.2 – Compare and contrast common networking hardware devices.
We’re back. Welcome to Domain 2: Networking. Knowing how to build computers and configure mobile devices is all well and good—but they have to communicate with each other, or very little gets done. That means you as the technician should have a good understanding of networking connections between computers on the local area network (LAN) and over the Internet. These next four chapters will set the foundation for your networking knowledge.
Let’s talk. This first networking chapter discusses the TCP/IP ports and protocols that you should know for the exams; for example, the Domain Name System (DNS) on port 53. We’ll also get into the most common networking devices such as switches, routers, wireless access points, and plenty more. It’s these protocols and network devices that are at the core of network communications between computers.
2.1 – Compare and contrast TCP and UDP ports, protocols, and their purposes.
In this objective we’ll discuss the differences between TCP and UDP, why you would use each, and which protocols use them. Then we’ll get into the individual protocols such as FTP, HTTP, RDP, and many more. It’s imperative that you know this section—for the exam, and for the real world. That doesn’t just mean knowing the acronyms and port numbers, it means understanding how the protocols work in real-world scenarios with real hardware and software. We’ll try to incorporate these “use cases” as often as possible.
ExamAlert
Objective 2.1 concentrates on the following concepts: ports and protocols such as FTP, SSH, Telnet, SMTP, DNS, HTTP, POP3, IMAP, HTTPS, RDP, NetBIOS/NetBT, SMB/CIFS, SLP, AFP, DHCP, LDAP, and SNMP. It also covers the differences between TCP and UDP.
TCP vs. UDP
Network sessions on an IP network are normally either TCP or UDP. Let’s briefly discuss these two.
Transmission Control Protocol (TCP) sessions are known as connection-oriented sessions. This means that every packet that is sent is checked for delivery. If the receiving computer doesn’t receive a packet, it cannot assemble the message and will ask the sending computer to transmit the packet again.
TCP establishes network connections with a 3-way handshake; a process that includes three steps:
1. SYN: The client computer attempts to initiate a session to a server with a synchronize packet of information (SYN packet).
2. SYN + ACK: The server responds to the client request by sending a synchronization/acknowledgement packet (SYN-ACK packet).
3. ACK: The client sends an acknowledgement packet (ACK packet) to the server.
Once the server receives that ACK packet, it acknowledges the session, and the network connection is established. This is also known as a TCP socket connection. With TCP, the synchronization, acknowledgement, and sequencing of packets, guarantees delivery. Not a single packet is left behind! Not only that, but TCP uses a method known as flow control, which means that the sender does not overwhelm a server by sending too many packets, too quickly.
User Datagram Protocol (UDP) sessions are known as connectionless sessions. One example of UDP usage is with streaming media sessions. In these cases, if a packet is dropped, it is not asked for again. Let’s say you were listening to some streaming music and you heard a break in the song or a blip of some kind. That indicates some missing packets, but you wouldn’t want those packets back because by the time you get them, you would be listening to a totally different part of the music stream! Because of the nature of UDP, it does not use a handshake process or flow control, unlike TCP. It’s expected that you might lose packets in UDP streams, but not when making TCP connections.
Both TCP and UDP utilize protocols and ports to make connections. Let’s further discuss these protocols and ports now.
Ports and Protocols
There are many ports and protocols that computers will use to transmit information. The protocol used is based on the type of data to be transmitted, and the application being used. We’ll begin with HTTP and HTTPS.
HTTP vs HTTPS
For two computers to communicate, they must both use the same protocol. For an application to send or receive data, it must use a particular protocol designed for that application and open up a port on the network adapter to make a connection to another computer.
For example, let’s say you want to visit a website. You type the name of that website into the address bar of a web browser and one of two protocols will be initiated: HTTP, or HTTPS. Take a look at Table 5.1.
Table 5.1 Comparing HTTP and HTTPS
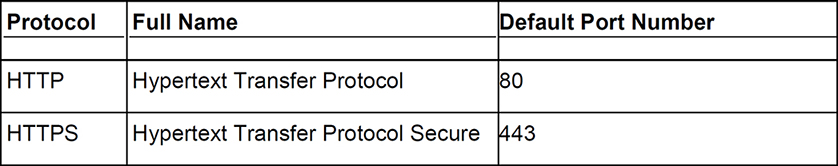
HTTP and HTTPS both use TCP as their connection mechanism. HTTP was used for decades, but that practice has been reduced drastically in favor of the more secure HTTPS. For security reasons, most websites that you connect to today will use HTTPS. Primarily, HTTPS is designed to keep a user’s information private and to prevent tampering and eavesdropping. Try connecting to some of your favorite websites and identify which protocol is being used. Most of them should be HTTPS, and those that are not should be avoided.
Let’s say you connected to one of my websites by typing dprocomputer.com. When you do so, it will automatically be changed to https://dprocomputer.com/blog or something similar (which is known as a redirect). The important part is that it is using HTTPS for security. That is the protocol that makes the connection to the dprocomputer.com web server. The HTTPS protocol selects an unused port on your computer (known as an outbound port) to send and receive data to and from dprocomputer.com. On the other end, dprocomputer.com’s web server has a specific port open at all times ready to accept sessions. In most cases the web server’s port is 443, which corresponds to the HTTPS protocol. This is known as an inbound port. Figure 5.1 illustrates this.
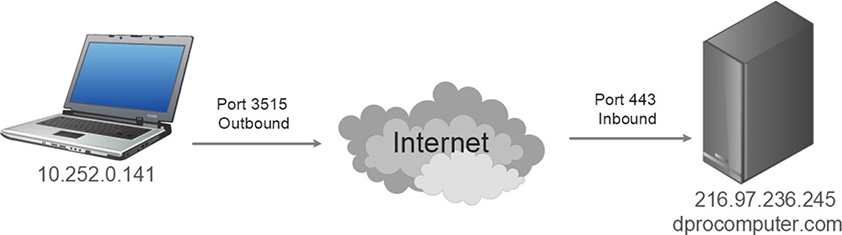
Figure 5.1 HTTPS in Action
The local computer on the left in Figure 5.1 has been given the IP address 10.252.0.141. This is a private, internal address. It uses port 3515 to go out to the Internet and start a session with dprocomputer.com. For security purposes, this is a dynamically assigned port and will be different every time you connect to another web server, but it will normally be somewhere in the thousands. The session is accepted by dprocomputer.com’s web server, using the public IP address 216.97.236.245, using inbound port 443. Conversely, if you want to run your own web server at home and sell widgets and such, that web server would need to have port 443, or the less secure port 80, open to the public at all times. If it were ever closed, you would lose sales! Computers that connect to your web server would use dynamically assigned ports.
HTTPS is used by the majority of websites today. It is recommended because of the secure connection it makes. It does this by connecting via a secure protocol such as SSL or TLS and using an encrypted certificate. We’ll discuss this process more in Chapters 31-35 that focus on security.
ExamAlert
Use HTTPS for web servers whenever possible – usually on port 443.
Note
You might have noticed that I omitted the “www” in the web server address. WWW stands for world wide web and is often not necessary today. If a website uses it, it will often convert the name automatically.
E-mail Protocols
For people who share written communications with each other, e-mail protocols are a must. E-mail is sometimes accomplished using a web browser (HTTPS) or within an app that works in the same manner. This is great for the home user and for small businesses. However, for larger organizations using desktop computers, or if you simply need to connect directly to specific e-mail servers, you’ll have to configure e-mail protocols. When setting up an e-mail client, you might need to know the protocols and ports involved. E-mail can be sent and received, so you will have to configure an outbound and an inbound server—which could be one and the same. Generally, the outbound server will be SMTP, and the inbound server will be either POP3 or IMAP.
• SMTP: Simple Mail Transfer Protocol (SMTP) sends e-mail. When you send e-mail from the e-mail client, it goes to an SMTP server and is then sent off to its destination. The e-mail server could be at an ISP or could be supplied by the organization you work for, either in-house or on the cloud. A good way to remember this acronym is by using the mnemonic device Send Mail To People. The original default port for SMTP was 25, but in order to make use of a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encrypted session you would use either 587 or 465. Which port will depend on the type of encryption used, and which protocol your ISP, or your administrator, or you, have selected.
• POP3: Post Office Protocol Version 3 (POP3) is very common, and is used by e-mail clients to retrieve incoming e-mail from a mail server. The original POP3 server port was 110, but for secure transmissions, the default port is 995.
• IMAP: Internet Message Access Protocol (IMAP) is an e-mail protocol that enables messages to remain on the e-mail server so they can be retrieved from any location. IMAP also supports folders, so users can organize their messages as desired. IMAP e-mail servers used port 143 for many years but for secure transmissions they use 993 by default.
On the client side, we must specify the server name and the correct ports for both the sending and receiving of e-mail. The protocols and ports must match exactly to the configuration of the e-mail server(s). E-mail clients include Outlook, Thunderbird, and a host of others. You can also use the Gmail application to connect to separate accounts using these protocols.
On the server side, there are several options available; for example Microsoft Exchange, which can handle SMTP, POP3, and/or IMAP, as well as HTTPS connections from web browsers and from mobile devices by using Exchange ActiveSync, part of Exchange Online. Configuration of e-mail servers goes beyond the scope of the A+ exams.
FTP, SSH, and Telnet
If you need to communicate with an external host to send and receive files and/or run commands on the external host, then you might be interested in FTP or SSH. Telnet on the other hand is deprecated, insecure, and should be avoided.
• FTP: The File Transfer Protocol allows computers to transfer files back and forth. When you connect to an FTP server, that FTP server will have port 21 open. Some type of FTP client software is necessary to connect to the FTP server; this could be done in the command-line within the FTP shell or by using a GUI-based application (such as FileZilla). However, default FTP is not considered secure today. Instead, organizations will usually prefer SFTP (discussed in the next bullet), or FTP Secure (FTPS) which uses SSL/TLS and utilizes port 989 and 990.
• SSH: Secure Shell enables data to be exchanged between computers on a secured channel. This protocol offers a more secure replacement to FTP and Telnet. The Secure Shell server housing the data you want to access would have port 22 open. There are several other protocols that use SSH as a way of making a secure connection. One of these is the commonly used Secure FTP (SFTP). As mentioned, regular FTP can be insecure. SFTP combats this by providing file access over a reliable data stream, generated and protected by SSH.
• Telnet: Short for Telecommunication network, this provides remote access to other hosts using the command-line interface (CLI). It uses port 23 but is an insecure and somewhat deprecated protocol. However, because some companies might still use it to access routers and other hosts, and to test and manage network connectivity, you might see a question about it on the exam. Generally, it is disabled, if it even exists in the OS. If you are wondering if it is enabled in Windows you can do a quick check for it in the Services console window (Run > services.msc). If it is not listed then it is not enabled. It can be enabled or disabled here: Control Panel > Programs and Features > Turn Windows features on or off.
DHCP
The Dynamic Host Configuration Protocol (DHCP) is used to automatically assign IP addresses to hosts. These hosts could be computers, printers, servers, routers, and so on. In most SOHO networks, a router will use DHCP to assign IP addresses to the client computers. However, your ISP will also use DHCP to assign an IP address to you; usually your router gets this. The DHCP service makes life easier for the network administrator by automatically assigning IP addresses, subnet masks, gateway addresses, DNS servers, and so on, from a central location. If you get your address from a DHCP server, you are getting your address assigned dynamically, and it could change periodically. Computers that do obtain IP addresses from a DHCP server have the advantage of automatically getting new addressing when they are moved to a different network segment. However, some computers require a static address, one that is assigned by the network administrator manually. It is better in many situations for servers and printers to use static addresses so you know exactly what the address is and so it won’t change.
By default, a DHCP server needs to have inbound port 67 open, and a DHCP client uses port 68 to connect out to that DHCP server. By the way, DHCP is also referred to as bootp—short for Bootstrap Protocol.
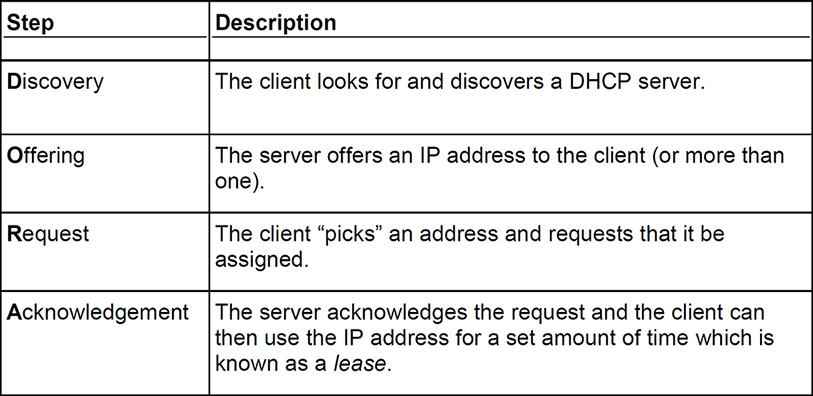
DHCP servers use a four-step process to assign IP addresses to clients—it is most commonly known as DORA. Table 5.2 briefly describes each of these steps. The first letter of each step forms the acronym DORA.
Table 5.2 DHCP 4-Step Process—DORA
Note
The DORA process happens in a flash. And sometimes, only half of the process is necessary. For example, if a client computer temporarily uses a static address and then goes back to a dynamic address. The original dynamic address is remembered by the computer, and so the computer simply requests that same IP address, and so only the request and acknowledgement steps are required.
DNS
The Domain Name System (DNS) is the group of servers on the Internet that translates domain names to IP addresses. For example, a domain name such as dprocomputer.com might translate to the IP address 216.97.236.245. When you connect to a website by name, the DNS server takes care of resolving the name to the IP address so that your computer and the web server can communicate via IP. To find out the DNS server that your Windows computer talks to, type the command ipconfig /allin the command-line.
A DNS server has inbound port 53 open by default. We’ll discuss DNS servers more in Chapter 7, “Networked Hosts and Network Configuration.”
LDAP and RDP
The Lightweight Directory Access Protocol (LDAP) is used to access and maintain distributed directories of information (such as the kind involved with Microsoft domains). Microsoft refers to this as Active Directory, and also directory services or domain services. It includes the user accounts, computer accounts, groups, and the authentication and permissions involved with those accounts. To have this in a domain, at least one Windows Server must be promoted to a Domain Controller. When you do this, LDAP is installed and runs on inbound port 389. A more secure version of LDAP (Secure LDAP) can also be installed and configured. This runs on port 636.
To facilitate connections to remote computers and allow full remote control, Microsoft uses the Remote Desktop Connection program, which is based off the Remote Desktop Protocol (RDP). This works in three ways. First, users can be given limited access to a remote computer’s applications (such as Word or Excel). Second, administrators can be given full access to a computer so that they can troubleshoot problems from another location. Third, another part of the program known as Remote Assistance allows users to invite a technician to view their desktops in the hopes that the technician can fix any encountered problems. These invitations can be made via e-mail. The RDP port, 3389, is also used by Remote Desktop Services/Microsoft Terminal Services, which is the server-based companion of Remote Desktop. Figure 5.2 shows the results of a netstat command that was run on a Windows Server that was upgraded to a domain controller. You can see that inbound port 389 is open—indicating LDAP is running and that it is indeed a domain controller—as well as port 3389 which allows for remote control of the server, which is exactly what I am doing in the figure.
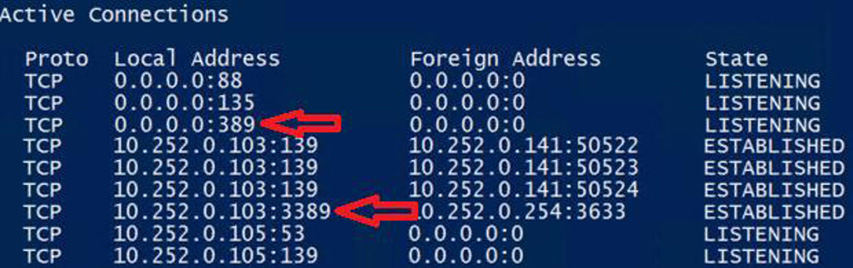
Figure 5.2 LDAP and RDP Ports on a Windows Server
More Protocols and Ports
There are a few more protocols that you should know for the exam including SMB/CIFS, NetBIOS/NetBT, AFP, SNMP and SLP.
• SMB: The Server Message Block (SMB) protocol provides access to shared items such as files and printers. These are actual packets that authenticate remote computers through what are known as interprocess communication (IPC) mechanisms. They can communicate directly over TCP using port 445 or by working with the NetBIOS/NetBT protocol using a port between 137 and 139. In the past, SMB was also referred to as the Common Internet File System (CIFS) protocol.
• AFP: Apple Filing Protocol (AFP) offers file services for Mac computers running macOS and OS X allowing for the transfer of files across the network. It uses port 548 for establishing the communication between two systems. Mac computers can also make use of SMB (and other protocols) for making connections to other systems.
• SNMP: Simple Network Management Protocol (SNMP) is used as the standard for managing and monitoring devices on your network. It manages routers, switches, UPS devices, and computers and is often incorporated in software known as a network management system (NMS). The NMS is the main software that controls everything SNMP-based; it is installed on a computer known as a manager. The devices to be monitored are known as managed devices. The NMS installs a small piece of software known as an agent that allows the NMS to monitor those managed devices and alert the SNMP manager software—and ultimately the administrator. If there is an alert to be sent to an administrator, it is known as a “trap”. SNMP by default uses port 161 and SNMP traps use port 162.
• SLP: The Service Location Protocol is a service discovery protocol that allows computers and other devices to find services in a local area network without prior configuration. It uses port 427 by default as its listening port.
Wow, that was a mouthful of acronyms. Study them and their port numbers!!! Use Table 5.3 to help. You will note that there are secure versions of some of the protocols which use a different port number. You will also find whether a protocol rides on TCP, or UDP, or both. I listed the protocol name in the first column, but the table is sorted by port number for easier reference.
Table 5.3 Protocol and Port Listing
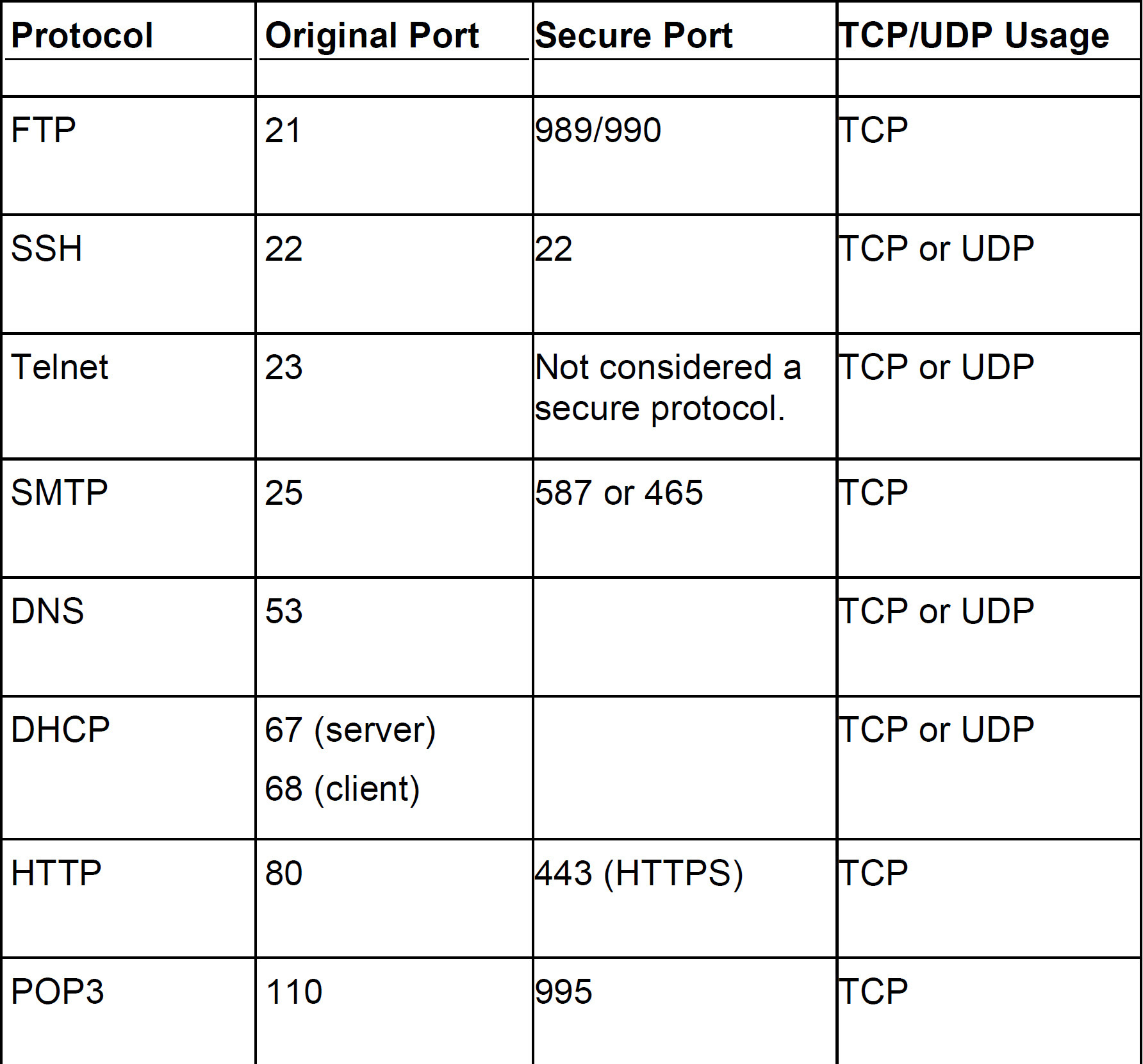
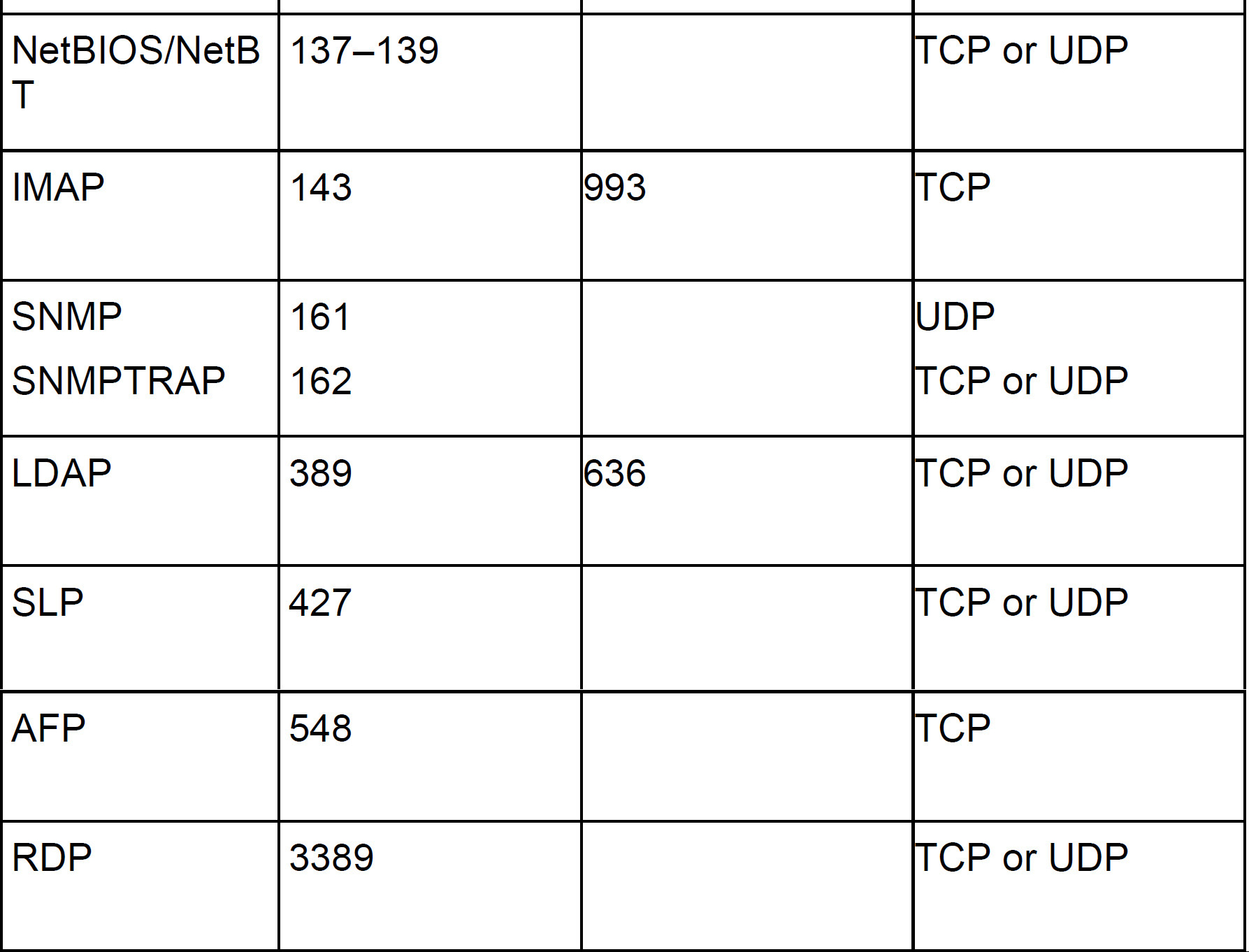
ExamAlert
I know there’s a lot, but know your protocols and their functions for the exam! Write’em down or make flash cards to commit them to memory.
Note
There are 65536 ports, you only need to know a handful of them, but if you want to find out more, check out the complete list provided by the IANA :
https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xml
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which protocol uses port 22?
![]() A. FTP
A. FTP
![]() B. TELNET
B. TELNET
![]() C. SSH
C. SSH
![]() D. HTTPS
D. HTTPS
2. Which of these would be used for streaming media?
![]() A. TCP
A. TCP
![]() B. RDP
B. RDP
![]() C. UDP
C. UDP
![]() D. DHCP
D. DHCP
3. Which ports are used by the IMAP protocol?
![]() A. 53 and 68
A. 53 and 68
![]() B. 80 and 443
B. 80 and 443
![]() C. 110 and 995
C. 110 and 995
![]() D. 143 and 993
D. 143 and 993
4. A user can receive e-mail but cannot send any. Which protocol is not configured properly?
![]() A. POP3
A. POP3
![]() B. FTP
B. FTP
![]() C. SMTP
C. SMTP
![]() D. SNMP
D. SNMP
Cram Quiz Answers
1. C. SSH (Secure Shell) uses port 22, FTP uses port 21, Telnet uses port 23, and HTTPS uses port 443.
2. C. User Datagram Protocol (UDP) is used for streaming media. It is connectionless, whereas TCP is connection-oriented and not a good choice for streaming media. RDP is the Remote Desktop Protocol used to make connections to other computers. DHCP is the Dynamic Host Configuration Protocol used to assign IP addresses to clients automatically.
3. D. The Internet Message Access Protocol (IMAP) uses port 143 by default and port 993 as a secure default. DNS uses port 53. DHCP uses port 68. HTTP uses port 80. HTTPS uses port 443. POP3 uses port 110 and 995 as a secure default. Know those ports!
4. C. The Simple Mail Transfer Protocol (SMTP) is probably not configured properly. It deals with sending mail. POP3 receives mail. FTP sends files to remote computers. SNMP is used to manage networks.
2.2 – Compare and contrast common networking hardware devices.
ExamAlert
Objective 2.2 focuses on the following concepts: routers, switches, access points, cloud-based network controllers, firewalls, network interface cards (NICs), repeaters, hubs, cable/DSL modems, bridges, patch panels, Power over Ethernet (PoE), and Ethernet over Power.
In this objective we’ll discuss the most common network hardware devices you’ll be dealing with including routers, switches, wireless access points, and many more.
As a computer technician you will be required to be able to connect to and configure network hardware. To allow communication between computers, we need to put some other devices in place. For example, switches, and access points connect computers on the LAN. Routers and firewalls enable connectivity to other networks and protect those connection points. The A+ exams cover only the basics about networking, but it is still a lot of material to cover so let’s get to it!
Switches
A switch is a central connecting device that all computers connect to in a wired fashion (a design known as a star topology). A switch sends the signal (frames of data) to the correct computer instead of broadcasting it out to every port (the way an older hub would). It does this by identifying the media access control (MAC) address of each computer. The MAC address is the physical address that is programmed into the network adapter; for example 00-0C-29-C6-XX-XX. (In Windows, run a quick ipconfig /all to find out your MAC address.) By identifying each computer’s MAC address, the switch can effectively make every port on the switch an individual entity. To further accomplish this, switches employ a matrix of copper wiring—everything is interconnected between the ports.
Switches are intelligent, and they use this intelligence to pass information to the correct port. This means that each computer has its own bandwidth (for example, 1000 Mbps). In today’s networks, the switch is commonly found in 1000 Mbps (1 Gbps) and 10 Gbps networks. You might also see older 100 Mbps connections though those should usually be upgraded to take advantage of today’s hardware and software.
Switches work within the Ethernet standard, which is the most common networking standard used today; it was ratified by the IEEE and is documented in the 802.3 set of standards. For example, a typical Ethernet network running at 1000 Mbps and using twisted-pair cable is classified as 802.3ab. 10 Gbps Ethernet over twisted-pair cable is 802.3an.
Understand the difference between a managed and an unmanaged switch. Managed switches can be configured when accessed from a browser or SSH or similar configuration tool. For example, you can: change the device’s IP address; turn on Spanning Tree Protocol (STP) to avoid network looping; enable system logging (syslog); and monitor the switch and other devices with SNMP. On the other hand, unmanaged switches don’t have these capabilities, they simply connect devices and computers together for transmission of data over the Ethernet network. Unmanaged switches are an inexpensive method of adding computers to your network.
A switch connects computers together in a wired fashion. From a design standpoint this is known as a star topology, with the switch in the “center” of it all. It is also the basis for a local area network (LAN). But what if you want to connect two LANs together? For example, two LANs that are in different cities? Enter the router.
Routers
A router is used to connect two or more networks to form an internetwork. They are used in LANs and WANs and on the Internet. This device routes data from one location to another, usually by way of IP address and IP network numbers. Routers are intelligent and even have their own operating systems. The router enables connections with individual high-speed interconnection points. A common example would be an all-in-one device or multifunction network device that might be used in a home or small office. These devices route signals for all the computers on the LAN out to the Internet. Larger organizations use more advanced routers that can make connections to multiple various networks as well as the Internet.
Wireless Access Points
A wireless access point (WAP)—or simply access point—enables data communications over the air when your computer is equipped with a wireless networking adapter. The WAP and the wireless networking adapter transmit data over radio waves either on the 2.4 GHz or 5 GHz frequencies. Wireless access points are everywhere you look: hotels, restaurants, shopping centers, you name it. It brings mobility to a new level.
WAPs are also included in most multifunction network devices, known as SOHO routers or simply routers. This enables wireless computers to not only communicate with each other but to access the Internet. Although hubs and switches deal with wired networks, the WAP deals with wireless connections. It is also based on Ethernet but now we are talking about the IEEE 802.11 group of standards that define wireless LANs (WLANs), simply referred to as Wi-Fi. Wireless access points act as a central connecting point for Wi-Fi-equipped computers. Like the switch, a WAP identifies each computer by its MAC address.
Firewalls
A firewall is any hardware appliance or software application that protects a computer from unwanted intrusion. In the networking world, we are more concerned with hardware-based devices that protect an entire group of computers (such as a LAN). When it comes to small offices and home offices, firewall functionality is usually built into the router. In larger organizations, it is a separate device. Or it could be part of a more complex, all-in-one solution. The firewall stops unwanted connections from the outside and can block basic networking attacks. We’ll discuss firewalls more in Chapter 31, “Physical and Logical Security,” and Chapter 35, “Data Destruction and SOHO Security.”
Network Interface Cards
A network interface card (NIC, pronounced like “nick”), also known as a network adapter, is a physical device that can be added to a computer or networking device that has an open and compatible slot. For example, a computer with an open PCI Express slot (x1 or x4) can be used with a NIC. This allows for connectivity to a computer network. Most PCs and laptops have these built into the motherboard—these are known as integrated NICs. However, workstations and servers often require a more powerful, and separate network interface card, or more than one. Quite often, a server will use special network cards that have 2, 4, or more RJ45 ports to allow for increased data throughput as well as higher availability. We’ll discuss the NIC more in Chapter 11, “Motherboards and Add-on Cards.”
ExamAlert
For the exam and for the IT field, the last five items we discussed are probably the most important of this section: switches, routers, access points, firewalls, and network interface cards.
Cloud-based Network Controllers
A network controller is software (or a device and software) that provides for centralized management, configuration, and monitoring of a computer network—be it physical or virtual. It is often programmable and can automate its tasks to help you to manage your network infrastructure. A cloud-based network controller is simply one that you access over the Internet at your cloud provider: Microsoft, Amazon, Google, IBM, and so on. Or, it’s one that is jointly managed by your organization and the cloud provider. That will all depend on the type of service you are paying for and have contracted for.
Repeaters
A repeater or extender is a device used to lengthen the signal farther than it was designed to go originally. For example, a standard wired LAN connection from a switch can transmit data 328 feet (100 meters), but a repeater could increase that distance by as much as two times. There are repeaters for wireless access points as well that can increase the range of your overall wireless network.
Hubs
The hub is the original connecting device for computers on the LAN. It creates a simple shared physical connection that all computers use to send data. It’s a basic device that has multiple ports, usually in intervals of four. Internally, the hub actually has only one main circuit that all the ports connect to (as opposed to a switch that has a matrix of circuits). It regenerates and passes on the electrical signals initiated by computers. This device broadcasts data out to all computers. The computer that it is meant for accepts the data; the rest drop the information. Because of this broadcasting and sharing, this device allows only two computers to communicate with each other at any given time. In the days of 10-Mbps and 100-Mbps networks, it was common to have a hub. It’s still listed on the A+ objectives, but in most instances today, the hub has given way to the switch.
Note
One thing you have to watch out for with a switch is something known as a flood attack. This type of attack can consume all the memory in the switch and cause it to fail-open, which means that it will fail to work as a switch, but will still work as a hub. This reduces the network throughput down to 10% or less and can also be a security concern. Update your switches and monitor them!
Cable/DSL Modems
Essentially, a cable or DSL modem is a device that allows a computer (or SOHO network) to access the Internet. Cable Internet and Digital Subscriber Line (DSL) Internet connections use separate devices to connect. For example, a person with a cable Internet connection will use a device that has an RG-6 port for the provider’s incoming coaxial cable. A DSL modem, on the other hand, will have an RJ11 port that makes use of a person’s telephone line. Both, however, use an RJ45 port which connects to the consumer’s computer or SOHO router by way of a twisted-pair patch cable.
Note
The term modem is a combination of the words modulate and demodulate. It originated with the dial-up modem that uses a standard telephone phone line. We’ll discuss dial-up more in Chapter 8, “Network Types and Networking Tools.” While it is arguable whether cable and DSL Internet devices are actually “modems”, the plain truth is that the term is commonly used—even by manufacturers.
Bridges
The bridge is a device that can either connect two LANs together or separate them into two sections. There are wired bridges and wireless bridges; today they are used to increase the size of networks.
Patch Panels
A patch panel is a physical hardware device that acts as a termination point for all of the network cables in a building. It is often located in a wiring closet, server room, or data center, depending on the size of the organization. It consists of multiple RJ45 ports on the front which connect to switches by way of twisted pair patch cables, and 110 IDC termination points on the back for connecting all of the individual wires in twisted pair cables. Those cables lead out to the various computer ports in the building. While it isn’t necessary to have a patch panel, it makes for easier patching of ports and is more reliable. A typical physical data path from a user to a server is: Computer > RJ45 jack > twisted pair cable > patch panel > switch(s) > server.
Power over Ethernet
Power over Ethernet (PoE) is an Ethernet standard that allows for the passing of electrical power in addition to data over Ethernet cabling. It is described in the IEEE 802.3af-2003, 802.3at-2009, and 802.3bt standards. It can deliver between 15.4 and 100 watts maximum to a variety of devices, as long as the sending and receiving devices are both PoE compliant. The exact amount of wattage will depend on the standard, but 15 to 30 watts is common.
This is an excellent solution for devices that require specific placement but where no electrical connection can be made (for example, outdoor video cameras or WAPs that need to be mounted to the ceiling). In these cases, all that needs to be run is a twisted-pair network cable, which takes care of power and data. No electrical connection is necessary.
The technology is broken down into the two devices:
• The power sourcing equipment (PSE), which could be a switch or other similar device.
• The powered device (PD), which as we mentioned could be an IP-based camera (or WAP) and also an IP phone, IPTV device, router, mini network switch, industrial device, lighting controller, and more.
For organizations with a group of remote devices, a 24- or 48-port PoE-enabled switch is the way to go. For a smaller organization that only has one or two remote devices that need to be powered, the PoE injector is a decent, cheaper PSE solution. This device is installed where the main network switch is and plugs into one of the switch’s ports. It is also powered normally from an AC outlet. But the injector has a second RJ45 port used to connect out to the remote device. This port sends Ethernet data as well as power over the Ethernet connection. This way, the organization can get power and data to a PoE-compliant access point, IP camera, or other device that needs to be located in an area where it would be difficult (not to mention expensive) to add an electrical outlet. However, the correct type of cabling must be used that can handle the amperage required. Generally, this is Category 5 twisted pair cabling and higher.
Ethernet over Power
Crossing the lines again, here we have Ethernet over power, which is effectively the converse of what we just discussed with PoE. In this case we are sending data over electrical lines. This is one variant of a concept known as power-line communication (PLC) which includes options for Ethernet, broadband, telecommunications, and more. In the home or office, it is usually implemented over standard 120 V AC electrical lines. To do this we add a modulated carrier signal to the wiring system. A powerline network uses power adapters for the AC outlets and Ethernet patch cables that connect from the adapters to whatever is needed, for example a compliant router. This technology can be a good solution where it is very difficult to run twisted pair cables, but 120 V AC electrical lines already exist.
ExamAlert
Know your network devices and try to imagine actual ways that you might incorporate them into your home or office.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following is most often used to connect a group of computers in a LAN? (Select all that apply.)
![]() A. Router
A. Router
![]() B. Switch
B. Switch
![]() C. Bridge
C. Bridge
![]() D. WAP
D. WAP
2. What device protects a network from unwanted intrusion?
![]() A. Switch
A. Switch
![]() B. Router
B. Router
![]() C. Access point
C. Access point
![]() D. Firewall
D. Firewall
3. Which of the following network devices moves frames of data between a source and destination based on their MAC addresses?
![]() A. Hub
A. Hub
![]() B. Switch
B. Switch
![]() C. Router
C. Router
![]() D. Modem
D. Modem
4. Which of the following network devices allows a remote device to obtain Ethernet data as well as electrical power?
![]() A. PD
A. PD
![]() B. PoE injector
B. PoE injector
![]() C. Repeater
C. Repeater
![]() D. Router
D. Router
5. Which of the following devices can be configured when accessed from a browser or SSH or similar configuration tool?
![]() A. Managed switch
A. Managed switch
![]() B. Unmanaged switch
B. Unmanaged switch
![]() C. Patch panel
C. Patch panel
![]() D. Network interface card
D. Network interface card
Cram Quiz Answers
1. B and D. Computers in a LAN are connected by a central connecting device; the most common of which are the switch and the wireless access point (WAP). Hubs can also be used, but those are deprecated devices; they are the predecessor of the switch. A router is designed to connect two networks together. Now, you might say, “Wait! My router at home has four ports on the back for computers to talk to each other.” Well, that is actually the switch portion of a SOHO “router”. The actual router functionality is in the connection between the two networks—the switched LAN and the Internet. A bridge is used to connect two LANs or separate a single LAN into two sections.
2. D. A firewall is a hardware appliance or software application that protects one or more computers from unwanted intrusion. A switch is a device that connects multiple computers together on a LAN. A router is used to connect two or more networks. An access point (or wireless access point) allows Wi-Fi-enabled computers and devices to communicate on the LAN wirelessly.
3. B. A switch sends frames of data between computers by identifying the systems by their MAC addresses. A hub broadcasts data out to all computers. The computer that it is meant for accepts the data; the rest drop the information. Routers enable connections with individual high-speed interconnection points and route signals for all the computers on the LAN out to the Internet. A modem is a device that allows a computer to access the Internet by changing the digital signals of the computer to analog signals used by a typical land-based phone line.
4. B. A PoE injector sends Ethernet data and power over a single twisted-pair cable to a remote device. PD stands for “powered device,” the PoE-compliant remote device that is receiving the power. A repeater extends the distance of a network connection. While a PoE injector can act as a repeater, not all repeaters are PoE injectors. A router makes connections from one network to another or from the LAN to the Internet.
5. A. Managed switches can be configured when accessed from a browser or SSH or similar configuration tool. For example, you can: change the device’s IP address; configure ports; and monitor the switch and other devices with SNMP. On the other hand, unmanaged switches don’t have these capabilities, they simply connect devices and computers together for transmission of data over the Ethernet network. A patch panel is a physical hardware device that acts as a termination point for all of the network cables in a building. A network interface card (NIC) allows for connectivity to a computer network. It is a physical device that can be added to a computer or networking device that has an open and compatible slot.
Another chapter done! Memorize those protocols and port numbers, take a quick breather, and move on!