Chapter 35. Data Destruction and SOHO Security
This chapter covers the following A+ 220-1002 exam objectives:
• 2.9 – Given a scenario, implement appropriate data destruction and disposal methods.
• 2.10 – Given a scenario, configure security on SOHO wireless and wired networks.
Hey! This is the last chapter on security. Or is it? We should always be thinking in terms of security, as you will see while we progress through the rest of the book. But as far as Domain 2.0 “Security” goes, this is the last chapter.
Here we’ll cover how to properly repurpose, recycle, dispose of and destroy hard drives. And by the way, we’ll be focusing on internal hard drives, but some of the methods herein can be applied to other devices that store data: USB flash drives, memory sticks, and so on. Be ready to protect all data, wherever it exists! Then we’ll discuss some SOHO router security including physical and logical security measures. There’s lots to do, so let’s go already!
2.9 – Given a scenario, implement appropriate data destruction and disposal methods.
ExamAlert
Objective 2.9 focuses on: physical destruction (shredder, drill/hammer, electromagnetic (degaussing), incineration, certificate of destruction); and recycling or repurposing best practices (low-level format vs. standard format, overwrite, drive wipe).
Hard drives that contain an organization’s data can be a security threat. When a hard drive is removed from a computer, it needs to be either stored, repurposed within the company, recycled for use by another entity, or disposed of in a proper manner. Sanitizing the hard drive is a common way of removing data, but it’s not the only way. The manner in which data is removed might vary depending on its proposed final destination. Proper data removal goes far beyond file deletion or the formatting of digital media. The problem with high-level formats done within the operating system is the data remanence (or the residue) that is left behind; with the help of third-party software, that residue can be used to re-create files. So, we have to plan how the drive will be repurposed and use some quality tools to make sure any data has been removed properly.
Warning!!
The tools and procedures described in the following sections will either remove all data on a drive or render a hard drive unusable! Proceed with extreme caution and at your own risk. Consider using virtual machines for testing.
Formatting Drives
Recall that we talked about formatting back in Chapter 24, “Operating System Installation.” We mentioned that Windows can perform a quick format and a full format, both of which are known as high-level formats, but have different results. A quick format in Windows simply removes access to the files, but a full format writes zeros to the entire partition (zeroing out the drive). So, for repurposing a drive, the full format is the better option. It is a form of overwriting.
However, there is also the low-level format term in the CompTIA A+ objectives. Also known as a physical format, the low-level format is something that is done to mechanical drives by the manufacturer. Modern hard drives are low-level formatted at the factory and it is a technique that should only be done once to a drive under normal circumstances; it physically creates the tracks and sectors on a hard disk drive. Older hard drives (from the 1980s and 1990s) could be low-level formatted from the BIOS in an effort to extend the lifespan of the drive, but it can be damaging to the drive. Today, the term “low-level format” or “LLF” has taken on a little more meaning for some people. Commands such as dd (which can zero out the drive), or hdparm, and programs such as GParted, and some other third-party tools are considered by some to be LLF tools. But, the reality is that they either zero out the drive or simply remove and create partitions, they are not really low-level formatting the drive. However, some of these tools can be more effective than a basic Windows format.
Regardless, all of these processes have to be performed from outside of the partition and file system that is to be formatted or overwritten. So, for example, to re-write a Windows system partition, you could boot the computer to a live Linux flash drive (running Ubuntu or other distro) and run the command or program required on the target Windows system partition.
Overwriting Drives
Let’s talk about deleting versus overwriting for a moment. If you delete a file on a hard drive, the OS will not be able to access it anymore. However, in most systems, the file remains until it is overwritten, either by another file or through another process. So, deleting data is not nearly enough to secure a drive that will be repurposed or recycled. Overwriting is a better option. This can be done with programs that write various data to the drive, but a common method is to zero out the drive. This means that you write binary zeros over every sector, and all the data, that is on the drive.
You can zero out a drive in Windows in a few ways. First with the full format option in the GUI that we mentioned previously. Second, with the format command in the Command Prompt. For example, the following command will format the E: drive as NTFS and will zero out every sector of the drive in two passes, meaning that it will run the process twice. You have to be in elevated mode in the Command Prompt to perform this procedure.
format E: /fs:NTFS /p:2
You can increase the number of passes by changing the parameter p:2 to whatever number you wish. Some companies require x number of passes, perhaps three. It all depends on the organization you are working for, and the policies that have been put in place. But remember, the more passes, the more time it will take, and the more stress that will be put on the hard drive.
Note
For more information about the format command and all of its parameters, type format /? and/or see the following link:
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/format
The third option is to use diskpart, but this utility will wipe the entire drive including any existing partitions, leaving you with unallocated space. To do this, enter the diskpart utility (again in elevated mode), list the disks (with the list disk command), then select the disk you want to zero out (for example, select disk 1), then type clean all. (You will have to type the name of the volume to proceed.) To use the drive again, it will have to be initialized, partitioned and formatted.
For all three of these options, the process can be very lengthy. It depends on the size of the drive, the speed of the drive, and the amount of data on it. To test these commands quickly, use a virtual machine with a small secondary virtual drive, say around 8 GB. Remember, you have to be outside of the partition or drive that you want to zero out. So, if you want to zero out the E: partition, do it from C:, and so on.
We can also zero out the drive in Linux and macOS. We mentioned that it can be done graphically with the GParted application (which has to be installed first), but you can also do it in Terminal with the dd command. For example:
sudo dd if=/dev/zero of=/dev/sdb1
Replace “sdb1” with whatever drive and partition you want to zero out. This particular command will zero out the first partition of the drive sdb (a second drive in the system). There are no warnings and the process can take a long time. To watch the progress of the procedure, use the status=progress parameter. Afterwards you will have to re-format the partition to the file system of your choice. Be very careful not to zero out the system partition. Use with extreme caution!
So, zeroing out the drive can be a potentially secure way of overwriting all of the data so that the drive can be repurposed within an organization. But what if the drive is to be recycled for use by another organization, or what if you wanted to sell a personal computer? You might want to go further. And if your organization has highly sensitive data, or personally identifiable information (PII) then a higher standard should be employed.
For example, the United States Department of Defense (DoD) 5220.22-M standard specifies sanitizing the drive. One implementation of this standard is to perform three passes: First, overwriting the entire drive with binary zeroes; Second, overwriting the entire drive with binary ones; and third, overwriting the entire drive with a random bit pattern, and verifying that final overwrite, logging that verification.
However, newer standards, such as NIST 800-88 (published in 2014), are more secure. 800-88 is actually broken down into three categories: clear, purge, and destroy.
Clear
This is the removal of data with a certain amount of assurance that it cannot be reconstructed. However, the data is actually recoverable with special techniques. In this case, the media is repurposed and used within the company again. Zeroing out the drive, and using bit-erasure software are examples of clearing. However, this method is not recommended for sensitive data.
Purge
Purging, or wiping the data of a drive is recommended for sensitive data and drives that will leave the organization. It can be done in two ways: with the Secure Erase option (or similar technique) or by degaussing the drive.
Secure Erase is a command that can be run from the firmware of an ATA drive (accessed from the UEFI/BIOS or elsewhere). Or, you can use tools from Seagate (SeaTools), Western Digital (SSD Dashboard), or Samsung (Magician). Third-party tools such as Blancco Drive Eraser are also available. If you use any of these tools, the drive will still function. The question is this: Will the tools meet the standards and policies set forth by your organization? Always follow your organization’s guidelines, and if there are no guidelines, or you are not sure, then purge the drive to the best of your ability, document the procedure, and store the drive in a secure location.
Note
Third-party tools such as DBAN can also wipe a drive, but they are designed for personal use, and do not meet the requirements of NIST or DoD standards, and so are not recommended for drives with sensitive data.
It is also possible to degauss a hard disk drive, which will render the data unreadable, and in most cases will render the drive unusable, which is why some people will refer to it as a method of “destruction”. Machines such as electromagnetic degaussers and permanent magnet degaussers can be used to permanently purge information from a disk. The process re-arranges the magnetic field of the disk so that the data is destroyed. This process is necessary for disks that cannot be accessed from a computer—if the drive can’t be accessed, then zeroing out methods cannot be performed. If a drive is designated to leave the organization, and the drive is damaged, this process might be used first before physical destruction. Some IT destruction companies will always degauss first before physical destruction. Keep in mind that degaussing is primarily used on magnetic-based drives.
Destroy
This is when the storage media is physically destroyed. This could be done in a very basic way by using a hammer or similar tool, or by drilling holes through the platters. But for drives with sensitive data, a more robust destruction technique should be employed. Electromagnetic degaussing is one option, but as we mentioned, that will often be used in conjunction with a complete physical destruction process such as, incineration, or the more common hard drive shredding (also known as pulverization). At this point—if there is anything left of the drive—the media can be disposed of in accordance with municipal guidelines. Some organizations require a certificate of destruction to show that a drive has indeed been destroyed; in fact the certificate is often required because of data privacy laws. This is obtained from the third-party that performs the drive destruction. A typical organization does not have the equipment necessary to perform proper destruction. That’s why an outside vendor will be contracted to do the work—those vendors have the mechanical degaussers and hard drive shredders designed specifically to meet NIST and DoD standards. Some of these vendors will come onsite to perform the process of destruction in front of the appropriate company personnel. Then the personnel sign off on the procedure. It’s not recommended that hard drives be mailed or otherwise transported to the vendor, but if they are, properly insured and tracked postal options or couriers would be required, and the entire process should be documented utilizing a chain of custody or similar process.
ExamAlert
Know the differences between clearing, purging, and destruction.
The type of data removal used will be dictated by the data stored on the drive. If there is no PII or other sensitive information, it might simply be cleared. But in many cases, organizations will specify purging of data if the drive is to leave the building and be re-used. In cases where a drive previously contained confidential or top-secret data, the drive will usually be destroyed. Again, always follow the policies that have been developed by your organization. If they are unclear, ask for additional interpretation from the appropriate personnel.
Note
The actual NIST SP 800-88 document can be obtained at this link:
https://csrc.nist.gov/publications/detail/sp/800-88/rev-1/final
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. A hard drive needs to be disposed of in a way so that no one can access the data. Which method should be used?
![]() A. Degaussing
A. Degaussing
![]() B. Clearing
B. Clearing
![]() C. Diskpart
C. Diskpart
![]() D. Destruction
D. Destruction
2. A drive is to be repurposed within your company. You have been tasked with zeroing out the drive three times from within Windows. Which of the following methods will accomplish this?
![]() A. Degaussing
A. Degaussing
![]() B. format C: /fs:fat32 /p:3
B. format C: /fs:fat32 /p:3
![]() C. diskpart > select disk 1 > clean all
C. diskpart > select disk 1 > clean all
![]() D. dd if=/dev/zero of=/dev/sda1
D. dd if=/dev/zero of=/dev/sda1
3. You have been tasked with purging a hard drive so that it can be recycled to a sister company. Which of the following should you perform before sending the hard drive out?
![]() A. Clear the drive
A. Clear the drive
![]() B. Degauss the drive
B. Degauss the drive
![]() C. Run Secure Erase
C. Run Secure Erase
![]() D. Pulverize the drive
D. Pulverize the drive
Cram Quiz Answers
1. D. You should destroy the hard drive. Before physical destruction, sanitize it, and/or degauss it. Clearing is the removal of data from a drive that is to be repurposed and used again within the organization. Diskpart can be used to clear the drive, it is not appropriate for hard drive disposal.
2. B. The only option listed that will zero out the drive three times (from Windows) is format C: /fs:fat32 /p:3. In this procedure we formatted the drive as FAT32, and ran the process three times (p:3). Degaussing a hard disk drive will render the data unreadable and, in most cases, will make the drive unusable. By default, the diskpart process listed and the dd process listed will only zero out the drive once. They would have to be run with an additional parameter, or run manually two more times to meet the criteria. Also, dd is run from Linux, not from Windows, so that is another reason that answer is incorrect. But be very careful: note that the drive listed in the dd command is sda1. That will most likely be the system drive; if the command is run on that drive, the OS will be erased, which is what you want in this case—just remember to use caution when erasing drives. Double check what you are doing before you run any commands.
3. C. At the bare minimum, run the Secure Erase program (or comparable program) to sanitize the drive. The rest of the answers are not examples of sanitizing or purging. Clearing the drive by formatting or zeroing out does not meet the requirements for sending the drive out to another company as standardized by NIST and the DoD. Degaussing the drive will render it useless. Pulverizing the drive (shredding it) will destroy it and will also render it unusable.
2.10 – Given a scenario, configure security on SOHO wireless and wired networks.
ExamAlert
Objective 2.10 concentrates on: wireless-specific configurations (changing default SSID, setting encryption, disabling SSID broadcast, antenna and access point placement, radio power levels, and WPS); change default usernames and passwords; enable MAC filtering; assign static IP addresses; firewall settings; port forwarding/mapping; disabling ports; content filtering/parental controls; update firmware; physical security.
In Chapter 6, “SOHO Networks and Wireless Protocols”, we discussed the setup of a small office/home office (SOHO) network. But without securing the network, we may as well just call up a hacker and ask that person to invade the network. The core of the SOHO network is the SOHO router. This device actually acts as a switch, router, firewall, and wireless access point. For the rest of this section, we’ll talk about how to secure this device and we’ll refer to it simply as a router. Before you make any security configurations, it is highly recommended that you update the firmware, and don’t forget to save the configuration when you are done!
Note
Remember that you can access online emulators for several different kinds of routers. It’s good to run through these configurations on your own router or an emulator of some sort.
Changing Default Passwords
The first thing we should do to secure the router is to change the password. Most routers come with a blank password. Connect to the router by opening up your favorite browser (your favorite should be the most secure one), typing the IP address of the router (for example, 192.168.0.1 or 192.168.1.1), and logging in. If the router has the option to create another admin account (or at least change the name), do it, and keep the original administrator account as the backup. But no matter what the router, you will definitely be able to change the password—and you should change it! Make it something complex, based on the rules we discussed in Chapter 33, “Windows Security Settings and Best Practices.” Save the settings (which will log you out) and then log in with the new password to make sure it took effect.
ExamAlert
Remember to change the admin password first before anything else!
Many routers also have a user password. Change this as well but change it to a different password than the admin password.
Wireless-Specific Security Settings
Now we’ll move onto some core radio and broadcasting security concepts including the SSID, encryption, antennas, radio power levels, and WPS.
Changing and Disabling the SSID
The Service Set Identifier (SSID) is used to name a wireless network. Default SSIDs are usually basic; it is wise to change the name of the wireless network before enabling wireless on the router. Names that include uppercase letters, lowercase letters, and numbers will be more challenging for casual wireless passersby to memorize.
After all wireless clients are connected to the network, consider disabling the SSID. Though it is not a perfect solution, it will mask part of the SSID broadcast, making it impossible to see with normal wireless locating software. Figure 35.1 shows a modified SSID named Neptune8Network and that it is not enabled. By the way, given the channel and mode listed, what frequency is this router transmitting on? Answer in a little bit.
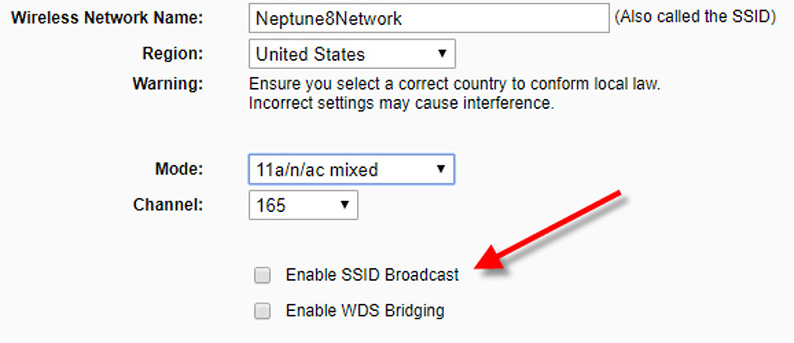
Figure 35.1 Renamed and disabled SSID
When the SSID is disabled, wireless clients won’t be able to scan for it. If you need to connect additional wireless clients, you will either have to enable the SSID broadcast or enter the wireless SSID manually when connecting. For example, to connect manually in Windows, open the Network and Sharing Center and select Set up a new connection or network, or the Connect to a network link in older versions of Windows. Then select Manually connect to a wireless network. (The wireless adapter must be installed with correct drivers to see this link.) You will have to type the SSID (known as Network name), the security type, the encryption type, and the security key to get in the network. We talk more about this type of connection, as well as setting encryption on a SOHO router and on the client in Chapter 32, “Wireless Security, Malware, and Social Engineering.”
Antennas and Radio Power Levels
Strategically place your access point. Usually, the best place for an AP is in the center of the building—if at all possible. This way, equal access can be given to everyone on the perimeter of the organization’s property, and there is the least chance of the signal bleeding over to other organizations. If needed, attempt to reduce the transmission power levels of the antenna, which can reduce the broadcast range of the AP. For example, Figure 35.2 shows the transmission power of an AP set to Low, which for small offices is usually enough. The other options are medium and high, or you might actually get a numerical option on some routers (measured in dBm). Test it by connecting with a laptop or other mobile device and moving to the perimeter of the building. If the lowest setting still allows access from the mobile device—with a decent data transfer rate—then there is no need to increase the power level.
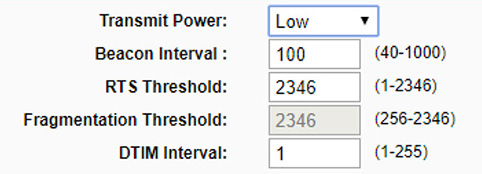
Figure 35.2 Power level of an access point set to Low
Also, to avoid interference in the form of EMI or RFI, keep WAPs away from any electrical panels, cables, devices, motors, or other pieces of equipment that might give off an electromagnetic field. If necessary, shield the device creating the EM field.
An AP’s antennas can be rotated so that they are parallel to each other, or at an angle to each other. For example, if you have two antennas, then 180 degrees is often a good orientation to sweep the area for wireless transmissions. The more antennas the better (usually), especially if they incorporate MIMO technology to combine multiple data streams.
By placing the AP and adjusting the antennas appropriately, and lowering the radio power levels as far as possible, you can further secure your wireless network while still providing decent service to your users.
ExamAlert
Strategically place your access points and know how to adjust radio power levels and AP antennas.
Disabling WPS
Wi-Fi Protected Setup was originally intended to make connecting to a wireless access point easier for the average user. However, anything that is made simpler is often less secure as well. Case in point, WPS is vulnerable to brute-force attacks, which can lead to intrusions on the network. Brute-force attacks are used to guess passwords and codes by trying combinations of letters, numbers, and symbols. The WPS code is usually 8 to 10 digits long, which is not very difficult to crack. So, your best bet is to disable WPS on the router to help secure the network. Figure 35.3 shows WPS as disabled (the Enable box is not checked). You can also see the basic 8-digit PIN code that is used. Sometimes, the WPS configuration is deep within the advanced settings or parameters of an AP.
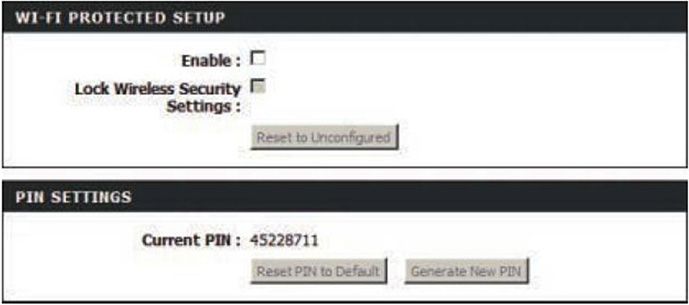
Figure 35.3 Disabled Wi-Fi Protected Setup on a common router
Enabling MAC Filtering
The wireless access point might also have the capability to be configured for MAC filtering (a basic form of network access control), which can filter out which computers can (or cannot) access the wireless network (and wired network). The AP does this by consulting a list of MAC addresses that have been previously entered. For example, take a look at Figure 35.4. If you used the “Allow” option as selected in the figure, then only the network adapters with those corresponding MAC addresses can connect; everyone else cannot join the wireless network.
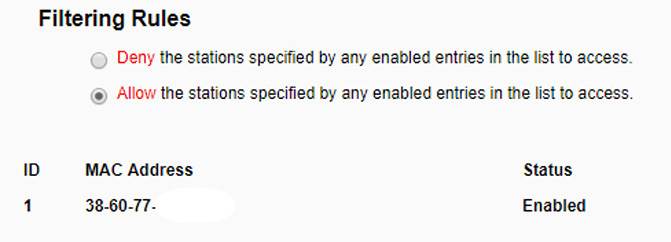
Figure 35.4 MAC Filtering rules on an AP
In some cases, a device might broadcast this MAC table. If this is the case, look for an update for the firmware of the access point and attempt to fine-tune the broadcast range of the device so that it does not leak out to other organizations. Because MAC filtering and a disabled SSID can be fairly easily circumvented using a network sniffer, it is important to also use strong encryption and possibly consider other types of network access control (such as 802.1X) and external authentication methods (such as RADIUS).
ExamAlert
MAC filtering can filter out which computers can (or cannot) access the wireless network (and wired network). Know how to enable MAC filtering.
Assigning Static IP Addresses
A SOHO router can be set to limit the number of dynamic addresses it hands out. If there are not enough to go around, you might find that certain hosts (such as servers or printers) lose connectivity when there are more client computers on the network. First, consider increasing the scope of addresses that the router is configured to hand out to clients. Second, try assigning static IP addresses to the servers and printers—essentially, any hosts that share information or services. If more clients obtaining dynamic addresses are added in the future, the servers and printers will not be affected.
By default, the SOHO router itself uses a static IP on the LAN side, however on the WAN side it is usually set to obtain an IP address from an ISP dynamically, though you can change this to static if you wish. If you have servers that the SOHO router is port forwarding to, and you have clients connecting to those servers from the Internet, then you might consider requesting a bank of static IPs from your ISP, and configure the SOHO router’s WAN port to use one of those static IPs. Or at the very least, use a service such as DynDNS to forward your Internet domain name to your SOHO router’s dynamically assigned IP address. This way, clients will be able to connect by domain name, even if the IP changes over time. If you have clients connecting via a VPN through your SOHO router, using PPTP, L2TP, or OpenVPN, then the use of a static IP is recommended, and perhaps even required.
Disabling Physical Ports & Physical Security
Many routers come with the capability to disable the physical ports on the switch portion of the device. This is a wise precaution. If you disable unused physical ports, a rogue computer can be plugged in to the router physically but won’t have any hopes of accessing the network. This concept is a policy in most organizations. Unused router or switch ports are disabled so that a person can’t connect a laptop to any old RJ45 jack on the premises.
ExamAlert
Disable any physical ports that are not in use!
Consider the physical security of the SOHO router as well. Can anyone in the building put their hands on it? That would be inappropriate, so we need to physically secure the device. That means keeping it in a locked area such as a wiring closet, or if that is not possible, consider placing it above a drop ceiling (mounted properly), or on the ceiling if there is no drop ceiling. This way the device will at least be more difficult to reach; as long as you don’t have a ladder lying around. Being as it is a SOHO router, then chances are that the organization does not have a server room, but if it does, then that is another excellent location.
Note
We discuss various firewall settings and port forwarding in Chapter 6, “SOHO Networks and Wireless Protocols.”
Content Filtering/Parental Controls
Most SOHO routers come with a parental control section where content can be filtered on a very basic level. The “parent” can select the MAC address of a computer, and specify what domain names that computer is allowed to connect to—and when. Figure 35.5 shows an example of this.
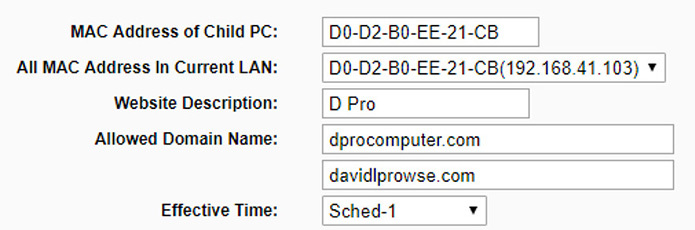
Figure 35.5 Parental Control Entry
In the figure you can see that the MAC address D0-D2-B0-EE-21-CB has access to two domains (dprocomputer.com and davidlprowse.com of course) and that there is an Effective Time using Sched-1, a schedule I pre-configured which allows the “child” to connect from 8am to 4pm on weekdays; scheduling is usually component of parental control.
Because the MAC address of a computer can’t be changed (by a typical user), this configuration follows the computer, even if it gets a new IP address later. That’s also the concept behind MAC filtering, and in fact some Parental Control sections will have a MAC filter built in.
A Final Word on SOHO Routers
To round out this section, make sure that the router’s firmware is up to date. Also, always make sure the built-in firewall is enabled. This firewall is going to be much more important than the Windows firewalls on the individual computers, though both are recommended. Most routers’ firewalls are on by default, but you should always check. If you do any kind of port forwarding, port triggering, DMZ configurations, or remote connections of any kind, make sure the firewall is allowing traffic only through the specific port or ports you require and that everything else is blocked. Check for updates every month or so, and while you are at it, change the administrator password for good measure.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following helps to secure a SOHO router? (Select the three best answers.)
![]() A. Change default passwords
A. Change default passwords
![]() B. Enable SSID
B. Enable SSID
![]() C. Enable MAC filtering
C. Enable MAC filtering
![]() D. Enable WPS
D. Enable WPS
![]() E. Enable WPA2
E. Enable WPA2
2. You want to prevent rogue employees from connecting a laptop to the SOHO router and accessing the network. How can you accomplish this? (Select the two best answers.)
![]() A. Enable MAC filtering
A. Enable MAC filtering
![]() B. Create a DMZ
B. Create a DMZ
![]() C. Configure a complex SSID
C. Configure a complex SSID
![]() D. Disable physical ports
D. Disable physical ports
3. You want to prevent certain users from accessing particular websites. What should you configure on the SOHO router?
![]() A. MAC filtering
A. MAC filtering
![]() B. Disable unused ports
B. Disable unused ports
![]() C. Port forwarding
C. Port forwarding
![]() D. Parental controls
D. Parental controls
![]() E. Power levels
E. Power levels
Cram Quiz Answers
1. A, C, and E. Changing default passwords, enabling MAC filtering, and enabling WPA2 can all increase the security of a SOHO router. Enabling the SSID broadcast makes it visible. Enabling WPS makes it easier to connect to but has security implications.
2. A and D. By enabling MAC filtering, you can create a list of MAC addresses that the SOHO router will accept. Any other computers with different MAC addresses will not be allowed access to the network. This works for wired and wireless connections. You can also disable physical ports on the router; this blocks any physical signal from being sent to those unused ports. A demilitarized zone (DMZ) is used to host servers and acts as a separate area between the LAN and the Internet. A complex SSID is great but won’t matter to a user connecting a laptop physically to the router because the SSID affects only wireless access.
3. D. By enabling parental controls, you can select computers—by MAC address—and select what websites (domains) those computers are allowed to connect to. MAC filtering by itself simply allows or denies computers access to the router based on the MAC address of the computer. Disabling unused ports is a good idea, but will simply stop a computer from accessing the SOHO router if it is connected on that port. Port forwarding is when you configure the router to forward Internet-based IPs and ports to a computer or server that is on the LAN or DMZ. Power levels refers to the broadcasting power of the AP’s radio. The lower the better, as long as people on the perimeter (of the building) can still communicate with the router.