Chapter 33. Windows Security Settings and Best Practices
This chapter covers the following A+ 220-1002 exam objective:
• 2.6 – Compare and contrast the differences of basic Microsoft Windows OS security settings.
• 2.7 – Given a scenario, implement security best practices to secure a workstation.
More security? Yes, three more chapters to be sure including this one, but it doesn’t end there. You should always be thinking with your information security hat on.
This chapter gets into some basic Windows security settings as well as some computer security best practices. Some of these best practices can be used on any OS, but we’ll be focusing on Windows for most of this chapter. Begin.
2.6 – Compare and contrast the differences of basic Microsoft Windows OS security settings.
ExamAlert
Objective 2.6 focuses on: Users and groups; NTFS vs. share permissions; shared files and folders; system files and folders; user authentication; Run as administrator vs. standard user; BitLocker; BitLocker To Go; and EFS.
The main goals of information security are to keep data Confidential, and keep the Integrity of data intact—all while preserving the Availability of data. That is the CIA triad of computer security—consider it whenever you are securing hardware, software, data, and people. In this chapter we’ll contemplate security as it relates to files, folders, users, permissions, and encryption.
Users and Groups
Users are what it’s all about when it comes to Windows security. On a Windows client computer, you can accomplish basic user account creation from within Settings or the Control Panel, but in this section we will be focusing on the more useful Local Users and Groups, which you can access from Computer Management or directly by going to Run, and typing lusrmgr.msc.
There are four main types of user account levels you should know for the exam:
• Administrators have full (or near full) control of an operating system. They are the most powerful accounts in Windows and have access to everything.
• Standard Users (also simply referred to simply as users) are the normal accounts for people who can log on to the network. This user account has access to (owns) data but cannot access the data of any other user and by default cannot perform administrative tasks (such as installing software).
• Guests have limited access to the system. A Guest cannot install software or hardware, cannot change settings or access any data, and cannot change the password. The Guest account is sometimes used for temporary workers or vendors who may need temporary access. The Guest account is disabled by default.
• Power Users are included in Windows for backwards compatibility with older versions of applications.
ExamAlert
Know the Windows user accounts and groups including Administrator, Power user, Guest, and Standard user. Know what they can and cannot do!
All of these are actually groups within Windows client operating systems (such as Windows 10). If you access the Local Users and Groups window, and click on the Groups folder, then you will see these groups and many more; for example, Backup Operators, Remote Desktop Users, and so on. There are, however, individual Administrator and Guest accounts (located in the Users folder) that are built into the system.
You can create users by clicking on the Users folder and then clicking Action > New User, or by right-clicking in the user list work area and selecting New User. This brings up a window as shown in Figure 33.1.
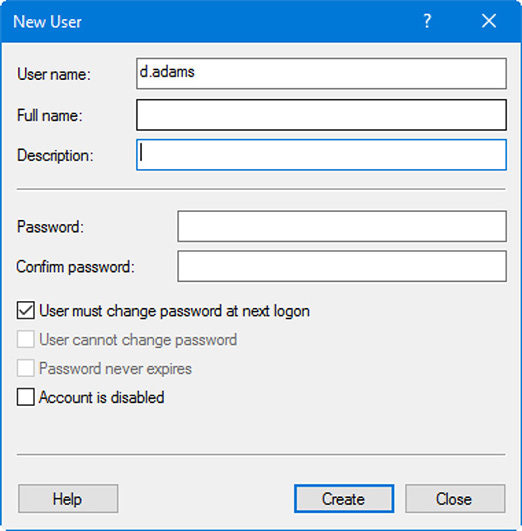
Figure 33.1 New User Window
Try going through the process now. At the bare minimum, you’ll be required to type a user name. You can fill out other information as well including the user’s full name, and a description of the user. By default, the “User must change password at next logon” option is selected, so you don’t have to select a password. In some scenarios the systems administrator supplies the password. If so, then you as the admin would have to type the password (and confirm it), then deselect the first checkbox option, and then select “User cannot change password”. The password will have to comply with any password policy that has been set (length, complexity, etc.…). Keep in mind that this is not the most secure way to do things, but might be necessary in some cases. You’ll also note that there is a checkbox called “Account is disabled”. You can disable an account temporarily from here, but generally you would work with that setting after the account is created (from the account Properties dialog box > Account tab). For example, if a user fails to log on with the correct password after x number of attempts (set in group policy) then the account will become disabled and you as the administrator would have to deselect it if the user is to log on. Conversely, if a person leaves an organization or is terminated, then you should immediately disable the account so that the user cannot log on anymore.
By default, when a user is first created, it is automatically given group membership to the Users group, and performs as a standard user. But, you can add memberships to other groups if you need to, for instance if you needed to have a second administrator. To do this, right-click on the user account and select Properties, then click the Member of tab. The Select Groups window pops up and here you can either type the name of the group you want to make the user a member of, or browse for it as demonstrated in Figure 33.2.
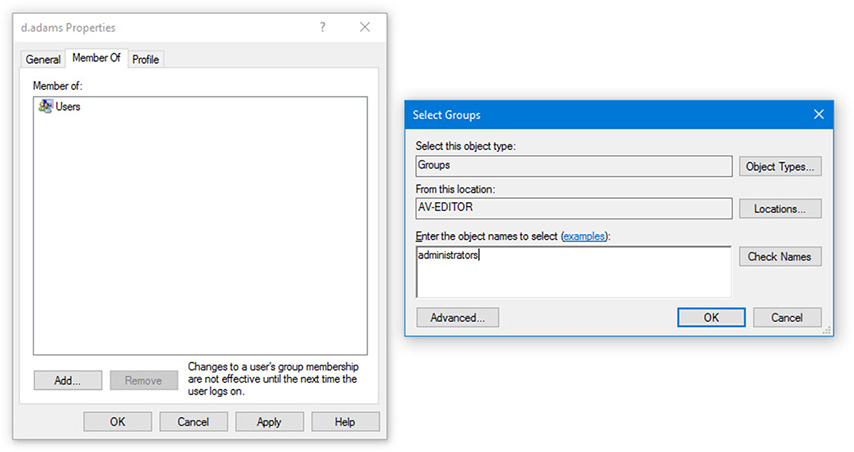
Figure 33.2 Group Membership in Windows
In the figure, the user d.adams is currently a member of the Users group, but I am in the process of adding that user to the administrators group. But be careful who you add as an admin—that person will now get full control!
Note
You can also configure Windows users for single sign-on (SSO) authentication. This generally requires a domain, Microsoft Identity Manager, Azure, or OpenID Connect (often a combination of those). For more information on this, see the following link: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/what-is-single-sign-on.
Permissions
Folders and files can be assigned permissions which allow users a particular level of access to the data. There are two levels of permissions:
• Share permissions can be accessed from the Sharing tab. By default, the Everyone group has read-only access. The other two permissions available to us are Change and Full Control.
• NTFS permissions are accessed from the Security tab. Here we have six default levels of permissions, from Read to Write to Full Control, as shown in Figure 33.3. If you happen to be using both share and NTFS permissions together, the most restrictive of the two will take precedence. So, for example, if a user was given Full Control access in the Share permissions and only Read in the NTFS permissions, the user would ultimately have only the Read permission.

Figure 33.3 Security tab of a folder’s Properties window
ExamAlert
NTFS permissions are modified in the Security tab of the folder’s Properties window.
The weakest of the NTFS permissions is Read and the strongest, of course, is Full Control. Administrators have Full Control by default. However, typical users have only Read, List Folder Contents, and Read & Execute by default. You also note that we have the option to Allow access or Deny access and that this can be done by the user or by their user group, thus the term user-level security. Generally, when you want users to have access to the folder, you add them to the list and select Allow for the appropriate permission. When you don’t want to allow them access, normally you simply don’t add them. But in some cases, an explicit Deny is necessary. This could be because the user is part of a larger group that already has access to a parent folder, but you don’t want the specific user to have access to this particular subfolder.
Permission Inheritance and Propagation
If you create a folder, the default action it takes is to inherit permissions from the parent folder. So any permissions that you set in the parent will be inherited by the subfolder. To view an example of this, locate any folder within an NTFS volume (besides the root folder), right-click it, select Properties, access the Security tab, click the Advanced button. An example of this in Windows 10 is shown in Figure 33.4. (Names and navigation will be slightly different in other versions of Windows.)
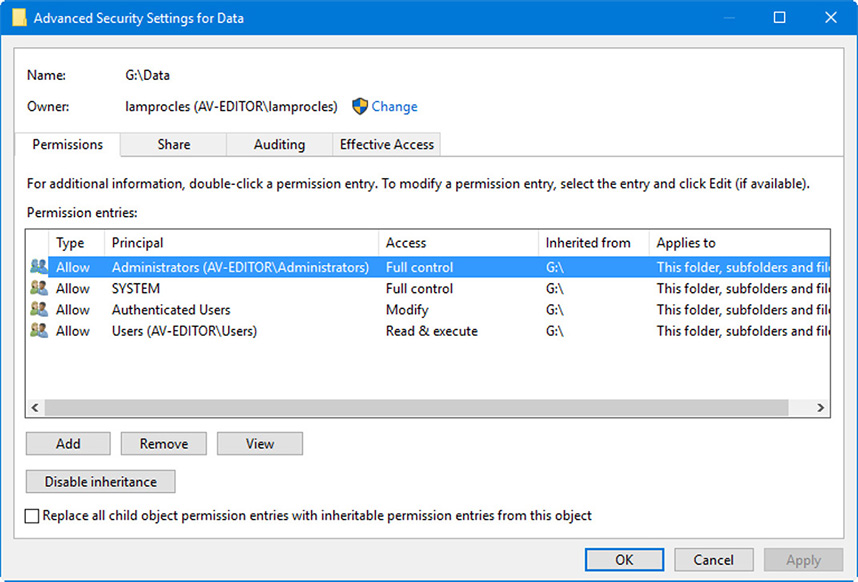
Figure 33.4 Advanced Security Settings window
What this all means is that any permissions added or removed in the parent folder will also be added or removed in the current folder. In addition, those permissions that are inherited cannot be modified in the current folder. To make modifications in this case, click the Disable inheritance box (or deselect the checkbox in earlier versions of Windows). When you do so, you have the option to copy the permissions from the parent to the current folder or remove them entirely. So, by default, the parent is automatically propagating permissions to the subfolder and the subfolder is inheriting its permissions from the parent. You can also propagate permission changes to subfolders that are not inheriting from the current folder. To do so, select the Replace All Child Object Permissions with Inheritable Permissions from this Object checkbox. (Again, names will vary according to the version of Windows.)
This might all seem a bit confusing; you will probably not be asked many exam questions on the subject. Just remember that folders automatically inherit from the parent unless you turn inheriting off—and you can propagate permission entries to subfolders at any time by selecting the Replace option.
Note
One other concept you should know that is not on the objectives is ownership. By default, Windows uses the discretionary access model (DAC) which means that the creator of a file or folder is the owner—and that means that only that person can assign permissions to that file or folder. However, an administrator can change who the owner is simply by clicking the Change link that is shown in Figure 33.4. So, the administrator can take ownership, and subsequently change permissions if he or she needs to.
Moving and Copying Folders and Files
This subject (and the previous one) is actually an advanced Microsoft Windows concept, so we’ll try to keep this simple. Moving and copying folders and files have different results when it comes to permissions. Basically, it breaks down like this:
• When you copy a folder or file on the same volume or to a different volume, it inherits the permissions of the parent folder it was copied to (known as the target directory).
• When you move a folder or file to a different location on the same volume, it retains the original permissions.
• When you move a file to another volume, it inherits the permissions of the parent folder.
Note
Keep in mind that when you move data within a partition, the data isn’t actually relocated; instead, the pointer to the file or folder is modified.
File Security
To start, files can be assigned four different attributes in Windows: Read-Only, Hidden, Compression, and Encryption. To access these, right-click any file and select Properties. On the General tab you will see the Read-Only checkbox; this makes it so no one can save modifications to the file, but a new file can be saved with the changes. The Hidden checkbox makes the file invisible to all users except the user who created the file. Admins can unhide files individually or for the entire system, as I will explain in a moment. When you click the Advanced button, you see Compression, which allows you to convert the file to a smaller size that takes up less space on the drive, and you see Encryption, which scrambles the file content so only the user who created the file can read it. We’ll discuss encryption later in this chapter.
Note
The attrib command in the Command Prompt can modify the Read-Only, Archive, System, and Hidden attributes for files and display the attributes for each file. This older command is still available in Windows but is not used often. For more information about this command, see this link:
https://dprocomputer.com/blog/?p=811
System files and folders are hidden from view by the OS to protect the system. In some cases, you can simply click the Show the Contents of This Folder link, but to permanently configure the system to show hidden files and folders, navigate to the Folder Options window in Windows Explorer/File Explorer. Then select the View tab and, under Hidden Files and Folders, select the Show hidden files, folders and drives radio button. To configure the system to show protected system files, deselect the Hide protected operating system files checkbox, located shortly below Show hidden files and folders. This enables you to view files such as bootmgr, pagefile.sys, and hiberfil.sys.
ExamAlert
To view files such as bootmgr, pagefile.sys, and hiberfil.sys, select the Show hidden files radio button and deselect the Hide protected operating system files checkbox.
Administrative Shares
Folders and files need to be shared so that other users on the local computer and on the network can gain access to them. Windows operating systems use an Access Control Model for securable objects like folders. This model takes care of rights and permissions, usually through discretionary access control lists (DACLs) that contain individual access control entries (ACEs). All the shared folders can be found by navigating to Computer Management > System Tools > Shared Folders > Shares, as shown in Figure 33.5. You can see that I have shared a folder named Data, it is also known as a local share.
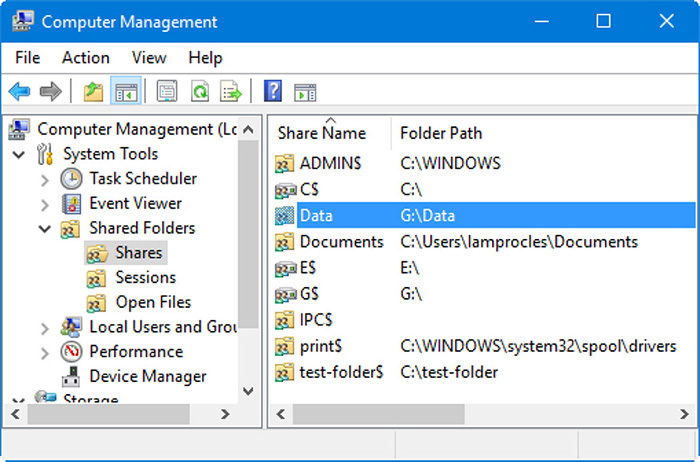
Figure 33.5 Windows Shares
Here we also see the hidden administrative shares that can be identified by the $ on the end of the share name. These shares cannot be seen by standard users when browsing to the computer over the network; they are meant for administrative use. Note that every volume (C: E: and G: for example) has an administrative share. Although it is possible to remove these by editing the Registry, it is not recommended because it might cause other networking issues. You should be aware that only administrators should have access to these shares. Administrative shares can be created by simply adding a $ to the end of the share name when enabling the share. Administrative shares can be accessed only if the user knows the exact network path to the folder and has permissions to access it.
ExamAlert
Hidden administrative shares can be identified by the $ on the end of the share name.
Encrypting File System
Encryption is the process of converting information with the use of a cipher (algorithm), making it unreadable by other users unless they have the correct “key” to the information. Cryptography is the practice of hiding information. In a cryptosystem, information is protected by disguising it.
There are a few different encryption technologies used in Windows. For example, whenever you log on to a Windows network, that authentication is secured with the Kerberos protocol. Another example is when you want to encrypt one or more files or folders. In this case, Windows uses the Encrypting File System (EFS), a component of NTFS. Follow these steps to encrypt a file in Windows:
1. Locate the file, right-click it, and select Properties. This brings up the General tab within the file’s Properties window.
2. At the bottom of the General tab, click the Advanced button. This brings up the Advanced Attributes window.
3. Check the box labeled Encrypt Contents to Secure Data.
4. Click OK for both windows. (When you do so, the system should ask whether you want to encrypt the parent folder and the file or just the file. It’s recommended that the file’s parent folder be encrypted as well.)
To unencrypt the file and return it to normal, simply deselect the checkbox.
Note
You can color code encrypted and compressed NTFS files. This is done in the Folder Options dialog box > View tab > Show encrypted or compressed NTFS files in color. After you select that, a green filename will indicate an encrypted file, and a blue filename indicates a compressed file.
If a file needs to be decrypted and the original user (owner of the key or certificate) isn’t available, an EFS recovery agent will need to be used. In many cases, the default recovery agent is the built-in Administrator account. It is important to note a couple more items: One is that EFS isn’t designed to protect data while it is transferred from one computer to another; the other is that it is not designed to encrypt an entire drive.
Note
File-sharing connections are also encrypted in Windows 7 and higher. You can modify this setting within Network and Sharing Center > Advanced Sharing Settings or in HomeGroup > Advanced Sharing Settings. Either way, 128-bit encryption is recommended.
BitLocker Encryption
To encrypt an entire disk, you need some kind of full disk encryption software. There are several currently available on the market. One developed by Microsoft is called BitLocker, which is available only on select editions of Windows (Pro, Enterprise, and so on). This software can encrypt the entire disk, which, after it’s completed, is transparent to the user. However, there are some requirements for this, including
• A Trusted Platform Module (TPM): A chip residing on the motherboard that actually stores the encrypted keys.
or
• An external USB key to store the encrypted keys.
and
• A hard drive with two volumes, preferably created during the installation of Windows. One volume is for the operating system (most likely C:) that will be encrypted; the other is the active volume that remains unencrypted so that the computer can boot. If a second volume needs to be created, the BitLocker Drive Preparation Tool can be of assistance and can be downloaded from https://www.microsoft.com/en-us/download/details.aspx?id=7806.
ExamAlert
Know the components necessary for BitLocker.
BitLocker software (as well as EFS) is based on the Advanced Encryption Standard (AES) and uses a 128-bit key by default, though it can be increased to 256-bit in the Group Policy Editor. Keep in mind that a drive encrypted with BitLocker usually suffers in performance compared to a nonencrypted drive and could have a shorter shelf life as well. By default, BitLocker is used to encrypt the internal drive of a system. However, you can also encrypt USB drives and other removable devices by using BitLocker To Go.
Note
Need to increase the BitLocker’s AES cipher strength to 256-bit? Open the Local Group Policy Editor and go to: Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption, then enable and configure the policy for your version of Windows.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. You have been tasked with setting up encryption for a Windows computer. You are required to encrypt several shared folders within a partition, so that they can’t be read by other users. What tool should you use?
![]() A. BitLocker
A. BitLocker
![]() B. TPM
B. TPM
![]() C. Administrative share
C. Administrative share
![]() D. EFS
D. EFS
2. One of the users on your network is trying to access files shared on a remote computer. The file’s share permissions allow the user full control but the NTFS permissions allow the user Read access. Which of the following will be the resulting access for the user?
![]() A. Full Control
A. Full Control
![]() B. Modify
B. Modify
![]() C. Read
C. Read
![]() D. Write
D. Write
3. You are the administrator for your network and you set up an administrative share called Data$. Which of the following is necessary in order for another user to access this share? (Select the two best answers.)
![]() A. The user must be part of a HomeGroup.
A. The user must be part of a HomeGroup.
![]() B. The user must have permissions to access the share.
B. The user must have permissions to access the share.
![]() C. The user must know the decryption key.
C. The user must know the decryption key.
![]() D. The user must know the exact network path to the share.
D. The user must know the exact network path to the share.
![]() E. The user must enable File Sharing in the Network and Sharing Center.
E. The user must enable File Sharing in the Network and Sharing Center.
4. Which Windows account would you create for someone who needs to regularly install software, change settings, and take ownership?
![]() A. Power user
A. Power user
![]() B. Standard User
B. Standard User
![]() C. Guest
C. Guest
![]() D. Root
D. Root
![]() E. Administrator
E. Administrator
Cram Quiz Answers
1. D. Use the Encrypting File System (EFS). This is easily done: right-click the folder(s), select Properties, click the Advanced button, and check mark Encrypt contents to secure data. At this point, other users will not be able to read the files contained in those folders. BitLocker is used to encrypt an entire hard drive (or volume), but in the scenario you only need to encrypt several folders. A trusted platform module (TPM) is a chip that is required for using BitLocker, but it is not necessary for EFS. By creating an administrator share, you will effectively hide the contents from typical users, unless they know an admin password. If they do know the password, then they could read the files. Regardless, administrative shares do not encrypt data.
2. C. The user will get only Read access. If you are using both sets of permissions, those most restrictive will take precedence. In this case, NTFS permissions are more restrictive than share permissions.
3. B and D. The user needs to have permissions to the share and must know the exact path to the network share because it is an administrative share. HomeGroup does not play into this scenario. Also, the question does not mention whether the file is encrypted. The user doesn’t need to enable sharing; the person is trying to access a share.
4. E. Administrators have full control of an operating system. Power Users included in Windows for backwards compatibility with older versions, and are seldom used. Standard Users are the normal default accounts for people who can log on to the network. Guests have limited access to the system. A Guest cannot install software or hardware, cannot change settings or access any data, and cannot change the password.
2.7 – Given a scenario, implement security best practices to secure a workstation.
ExamAlert
Objective 2.7 concentrates on: Password best practices; account management; disable autorun; data encryption; patch/update management.
As systems administrators we have to make sure that users can only get access to what they need, and that no one else can masquerade as a legitimate user. User accounts can be secured through a combination of a strong passwords, password policies, restrictions, account lockouts, and in general, good account management; which not only means solid configuration, but also monitoring and auditing of user accounts. While many of the techniques in this chapter are designed for Windows, some of the concepts can be easily incorporated to any operating system.
Usernames and Passwords
The username/password combination is the most common type of authentication for gaining access to computers. The username is known to all parties involved and can be seen as plain text when typed. In some cases, the user has no control over what his username will be; in other cases, his username might be his name or e-mail address (and the username could be selected by the user). For example, you might use a sign-in to access the Windows Store for apps; in this case, it is typical to use your e-mail address as your username. You can see it, it shows up on the screen, and you can be identified by it. The password is either set by the user or created automatically for the user. This password, however, is not something we want anyone else to know or see.
It is common knowledge that a strong password is important for protecting a user account, whether the account is with a bank, at work, or elsewhere. But what is a strong password? Many organizations define a strong password as a password with at least 8 characters, including at least one uppercase letter, one number, and one special character. The best passwords have similar requirements but are 15 characters or more. Many password-checker programs are on the Web for you to get an idea of what is considered “strong”. Table 33.1 shows a strong password and a “best” password.
Table 33.1 Strong and Stronger Passwords
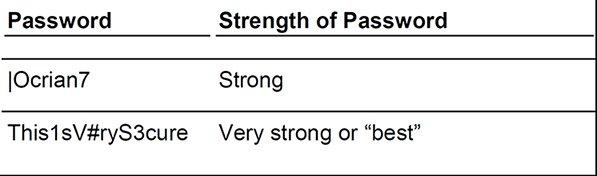
Notice the first password is using the | pipe symbol instead of the letter L. This is a special character that shares the \ backslash key on the keyboard. The second password uses 16 characters, including three capital letters, two numbers, and a partridge in a pear tree, um, I mean one special character ![]() . (Just checking whether you are still with me!) Of course, a partridge wouldn’t help your password security, but the other methods make for an extremely strong password that would take a super computer a long time to crack. Of course, neither of the passwords in the table are any good, because they have been mass printed and are known. They are just examples that should not be used on a system.
. (Just checking whether you are still with me!) Of course, a partridge wouldn’t help your password security, but the other methods make for an extremely strong password that would take a super computer a long time to crack. Of course, neither of the passwords in the table are any good, because they have been mass printed and are known. They are just examples that should not be used on a system.
ExamAlert
Understand what is required for a strong complex password.
Note
As mentioned in Chapter 11, “Motherboards and Add-on Cards,” BIOS/UEFI passwords are also very important, especially the administrative password. The same basic rules we mentioned here apply to BIOS passwords as well.
Password Policies
Changing your password at regular intervals is important as well. The general rule of thumb is to change your password as often as you change your toothbrush. However, because this is a subjective concept (to put it nicely!), many organizations have policies concerning your password. It might need to meet certain requirements, or it might need be changed at regular intervals, among other policies. Figure 33.6 shows an example of the default password policy on a Windows computer. This can be accessed by navigating to Local Security Policy > Security Settings > Account Policies > Password Policy.
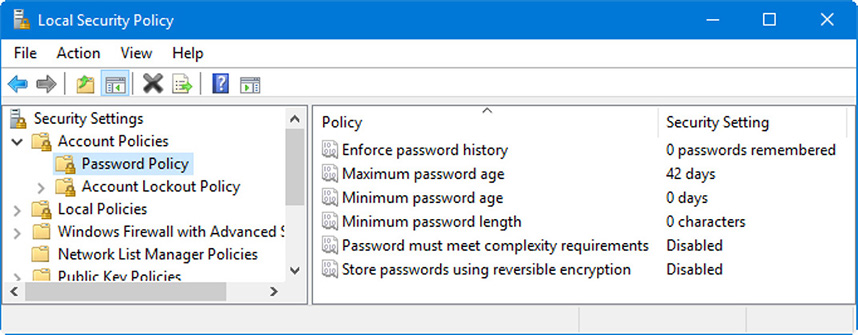
Figure 33.6 Default password policy in Windows
As shown in the figure, there are several items that we can configure (or can be configured by the network administrator centrally if the computer is part of a domain). The four important ones for the exam include
• Enforce password history: When this is defined, users cannot use any of the passwords that are remembered in the history. If you set the history to 3, the last three passwords cannot be used again when it is time to change the password.
• Maximum password age and Minimum password age: These settings define exactly how long a password can be used. The maximum is initially set to 42 days but does not affect the default Administrator account. To enforce an effective password history, the minimum must be higher than zero.
• Minimum password length: This requires that the password must be at least the specified number of characters. For a strong password policy, set this to between 8 and 14.
• Password must meet complexity requirements: This means that passwords must meet three of these four criteria: uppercase characters, lowercase characters, digits between 0 and 9, and nonalphabetic characters (special characters).
Note
For more information on some password best practices, visit: https://www.microsoft.com/en-us/research/publication/password-guidance/
Account Management
Now that we have a secure password and a password policy in place, let’s talk about securing the user accounts for Windows. There are a few things we can do to secure these:
1. Rename and password protect the Administrator account: To configure this account, navigate to Computer Management > System Tools > Local Users and Groups > Users and locate the Administrator account. By right-clicking the account, you see a drop-down menu in which you can rename it and/or give it a password. (Just remember the new username and password!) It’s great to have this additional administrator account on the shelf just in case the primary account fails. If the account is disabled you can enable it if necessary. Right-click the account and select Properties. In the General tab, deselect the Account is disabled checkbox. Alternatively, open the Command Prompt (Admin) and type net user administrator /active:yes. Of course, you have to have administrative privileges to perform these actions.
2. Verify that the Guest account (and other unnecessary accounts) are disabled: This can be done by navigating again to Local Users and Groups > Users, right-clicking the account in question, selecting Properties, and then selecting the checkbox named Account is disabled (it is disabled by default in most versions of Windows). You can also delete accounts (aside from built-in accounts, such as the Guest account); however, companies usually opt to have them disabled so that the company can retain auditing information that is linked to the account.
3. Restrict user permissions: Users are created as standard users by default, but it’s always a good idea to audit the user accounts and make sure that they don’t have any unnecessary group memberships that could give them more power than they require. This is part of the principle of least privilege—the less a user can do, the more secure the system will be.
4. Set logon time and computer restrictions: In a Windows domain, you can allow and disallow certain hours of the day that a user can log on to the network. In the user properties dialog box, go to the Account tab, then click the Logon Hours button. From there you can configure when the user is allowed to log on. For example, in Figure 33.7 Bob can only logon to the domain Monday through Friday from 8am to 6pm. You can also specify individual computers that the user can log on to by clicking the Log On To button. For temporary employees and contractors, it’s a good idea to configure account expiration which is at the bottom of the Account tab page.
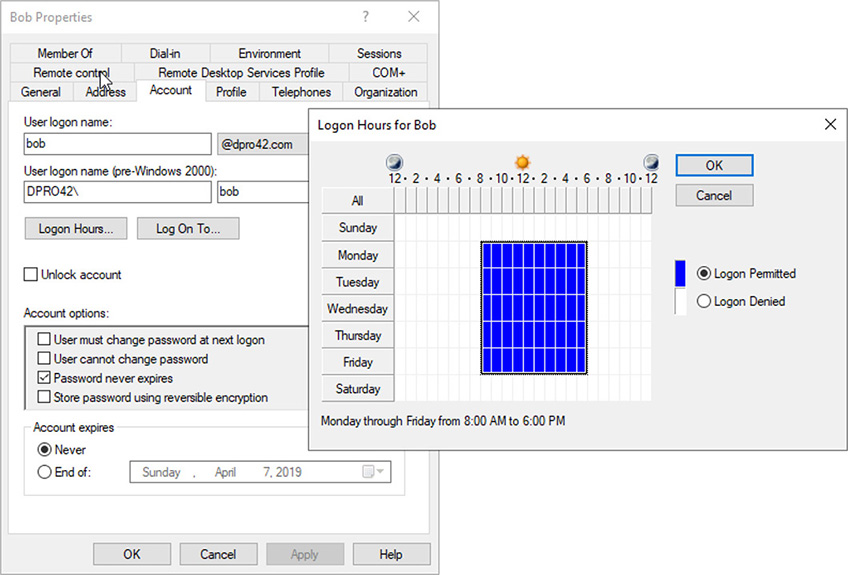
Figure 33.7 Logon Hours Setting
5. Set the Account lockout threshold: If a user attempts to log on to a system and is unsuccessful (after a specified number of attempts), the user will be locked out of the system. The settings and thresholds for this can be configured in the Local Security Settings window. Navigate to Security Settings > Account Policies > Account Lockout Policy. From here, you can set the threshold to a certain number of invalid logons, set how long the user will be locked out, and set how long until the lockout counter is reset. If an account is locked out and you need to unlock it immediately, follow one of the options at the end of step 1.
ExamAlert
Know how to enable/disable accounts, reset passwords, and modify password policy!
Note
Lockouts due to forgotten passwords are common in organizations. Sometimes a user will use several passwords to gain access to various systems, making the problem worse. Several complex passwords can be confusing to users and cause many tech support calls requiring accounts be unlocked. To combat this, use single sign-on (SSO) or federated identity management. Remember, with SSO, a user needs only one password to gain access to two or more systems.
It’s important to note that when logging on to a Microsoft network, the logon process is secured by the Kerberos protocol, which is run by the Active Directory domain controller. This adds a layer of protection for the username and password as they are being authenticated across the network.
Regardless of whether a user is part of a domain or not, when the user takes a break or leaves for lunch, the computer should be locked. This can be done by pressing Windows+L. When doing so, the operating system goes into a locked state, and the only way to unlock the computer is to enter the username and password of the person who is logged in to the computer. The difference between this and logging out is that a locked computer leaves all the session’s applications and files open; logging out closes all open applications and files.
Aside from locking the computer manually, the user can opt to put the computer to sleep after a certain period of time or enable a password-protected screensaver, both of which will force the user to log on when returning to the computer. Sleep settings can be accessed at Settings > Power & Sleep, or in the Power Options dialog box. To set the screen saver to require a password when the system resumes, for example in Windows 10, this can be done at Settings > Personalization (or right-click the desktop and select Personalize). Then go to Lock screen > Screen saver settings. In the dialog box, checkmark On resume, display logon screen.
Disabling AutoPlay/Autorun
If you disable AutoPlay, removable media won’t automatically start its Autorun application (if it has one), and any embedded malware won’t have a chance to infect the system before you scan the media. To disable AutoPlay/Autorun in Windows, complete the following steps:
1. Go to the search field (or Run prompt) and type gpedit.msc. This opens the Local Group Policy Editor. (This is not available in some editions of Windows.)
2. Navigate to Computer Configuration > Administrative Templates > Windows Components > AutoPlay Policies.
3. Double-click the Turn Off Autoplay setting. This displays the Turn Off Autoplay configuration window.
4. Click the Enabled radio button, and then click OK. You are actually enabling the policy named Turn Off Autoplay.
Another way to do this in Windows 10 is to open Settings and then click Devices. Next, select AutoPlay from the left side. Finally, set the AutoPlay slider button to Off.
Note
We discuss data encryption earlier in the chapter and patch management in Chapter 27, “Microsoft Operating System Features and Tools, Part 2.”
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following is the strongest password?
![]() A. |ocrian#
A. |ocrian#
![]() B. Marqu1sD3S0d
B. Marqu1sD3S0d
![]() C. This1sV#ryS3cure
C. This1sV#ryS3cure
![]() D. Thisisverysecure
D. Thisisverysecure
2. Your boss is concerned about people that have been terminated coming back in the building and attempting to log on to the network using passwords that they used in the past. What should you do to help protect against this? (Select the two best answers.)
![]() A. Set up a password length policy
A. Set up a password length policy
![]() B. Configure an account lockout threshold
B. Configure an account lockout threshold
![]() C. Immediately disable the accounts of people who have been terminated
C. Immediately disable the accounts of people who have been terminated
![]() D. Set logon time restrictions
D. Set logon time restrictions
![]() E. Disable the Guest account
E. Disable the Guest account
3. A customer complains that while he was away at lunch, someone used his computer to send e-mails to other co-workers without his knowledge. Which of the following should you recommend?
![]() A. Enable a screensaver.
A. Enable a screensaver.
![]() B. Unplug the network cable before leaving for lunch.
B. Unplug the network cable before leaving for lunch.
![]() C. Use the Windows lock feature.
C. Use the Windows lock feature.
![]() D. Enable the out-of-office message in e-mail when leaving for lunch.
D. Enable the out-of-office message in e-mail when leaving for lunch.
4. Which of the following best describes encryption?
![]() A. Prevents unauthorized users from viewing or reading data
A. Prevents unauthorized users from viewing or reading data
![]() B. Prevents unauthorized users from deleting data
B. Prevents unauthorized users from deleting data
![]() C. Prevents unauthorized users from posing as the original source sending data
C. Prevents unauthorized users from posing as the original source sending data
![]() D. Prevents unauthorized users from decompressing files
D. Prevents unauthorized users from decompressing files
5. How can you prevent applications from automatically executing, and possibly infecting a computer with malware when removable media is inserted?
![]() A. Enable the account lockout threshold policy
A. Enable the account lockout threshold policy
![]() B. Turn on BitLocker
B. Turn on BitLocker
![]() C. Turn off BitLocker To Go
C. Turn off BitLocker To Go
![]() D. Disable AutoPlay
D. Disable AutoPlay
Cram Quiz Answers
1. C. Answer C incorporates case-sensitive letters, numbers, and special characters and is 16 characters long. That makes it the strongest password of the listed answers. |ocrian# has special characters but is missing uppercase letters and numerals—plus it is only 8 characters long. Marqu1sD3S0d does not have any special characters. Thisisverysecure is 16 characters long and has one capital letter but does not have any numerals or special characters.
2. B and C. The best answers are to configure an account lockout threshold and immediately disable the accounts of anyone who has been terminated. A common method is to use the “three strikes and you’re out” rule for account lockout, meaning that a person can attempt to log on three times before the account is locked out. But more importantly, disable (or lock) the accounts of people who have been offboarded or terminated. The other options are all good security options in general, but won’t help much with disgruntled past employees who are attempting to get into the system. Also, some type of authentication system should be in place so that these people cannot get access to the building.
3. C. Tell the customer to lock the computer (by pressing Windows+L or by using the Start menu) before leaving for lunch. As long as there is a strong password, other co-workers should not be able to access the system. Screensavers by themselves do not secure the system, but a user can enable the password-protected screensaver feature (be aware that there is a delay before the screensaver turns on). Unplugging the network cable is not a legitimate answer; plus, it can always be plugged back in. The out-of-office message will reply only to people e-mailing the user; it won’t stop outgoing e-mails.
4. A. Encryption prevents unauthorized users from viewing or reading data. Properly configured permissions prevent unauthorized users from deleting data or attempting to decompress files. A strong logon password prevents unauthorized users from posing as the original source sending data.
5. D. If you disable AutoPlay, removable media won’t automatically start its autorun application (if it has one), and any embedded malware won’t have a chance to infect the system before you scan the media. The account lockout threshold specifies the amount of times a user can attempt to log on to Windows before being logged off. BitLocker and BitLocker To Go are used for encryption, not for blocking removable media from automatically executing files.