Chapter 32. Wireless Security, Malware, and Social Engineering
This chapter covers the following A+ 220-1002 exam objectives:
• 2.3 – Compare and contrast wireless security protocols and authentication methods.
• 2.4 – Given a scenario, detect, remove, and prevent malware using appropriate tools and methods.
• 2.5 – Compare and contrast social engineering, threats, and vulnerabilities.
You can’t get enough security! That’s because nothing is ever 100% secure, as we mentioned. However, we need to temper our vigilance and security aggressiveness by using prioritization. Always be thinking in terms of the most urgent threats and vulnerabilities to your organization, and continue the list of risks from there. Secure these accordingly, starting from the top.
This chapter continues on our security journey by discussing wireless security and authentication, how to prevent malware, and some different social engineering and technical attacks that you should now. It’s a bit of a catch-all chapter due to the number of varying concepts covered, but I’ll try to make it as pleasant as possible, by breaking it up into manageable sections. Let’s go!
2.3 – Compare and contrast wireless security protocols and authentication methods.
ExamAlert
Objective 2.3 concentrates on the following: protocols and encryption (WEP, WPA, WPA2, TKIP, and AES). Authentication (single-factor, multifactor, RADIUS, TACACS).
Wi-Fi connections are used by PCs, laptops, tablets, smartphones, industrial devices, and the list goes on. However, with ease of use comes additional security considerations. The plain truth is that a signal traveling in the air is going to be more insecure than one traversing a cable. So, we need to use proper wireless protocols and encryption protocols. Let’s talk about some of those now.
Wireless & Encryption Protocols
We discussed wireless connectivity and wireless encryption protocols in Chapter 6, “SOHO Networks and Wireless Protocols.” Let’s review those protocols now. Table 32.1 shows the protocols you should know for the exam.
Table 32.1 Wireless Encryption Methods

ExamAlert
Know the differences between WEP, WPA, WPA2, TKIP, and AES.
At the writing of this book (2019) the best option is to go with WPA2 for wireless connectivity, and AES for data encryption over that wireless connection. In fact, it may be your only option depending on the client used. For example, in Windows 10 Pro, if you select WPA2 (personal or enterprise), you will be forced by default to use AES. Figure 32.1 shows an example of this.
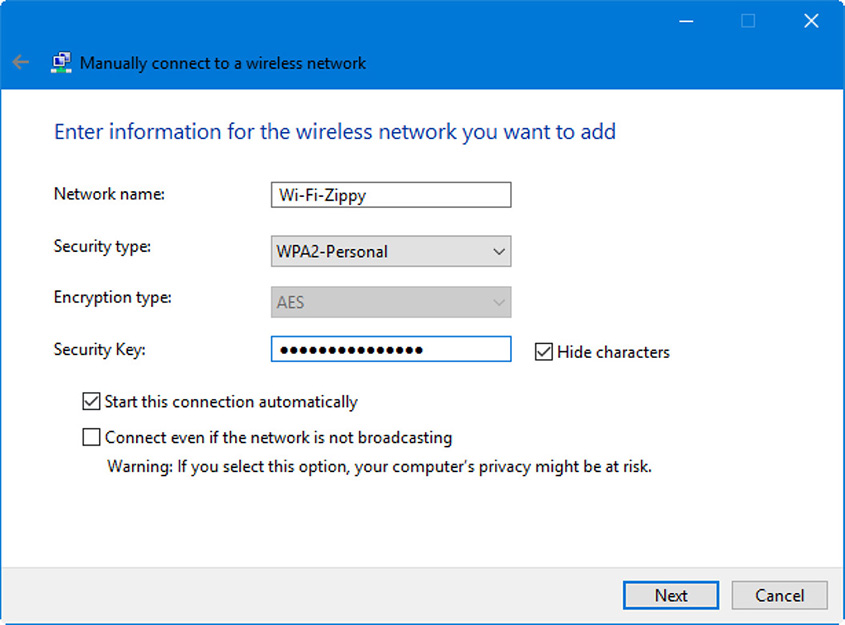
Figure 32.1 Manual Wireless Network Connection in Windows
The Encryption type field is grayed out, and while you could modify that in the Group Policy Editor or in the Registry Editor, it’s usually not wise. What would be wise is to modify the Hide characters setting for the Security Key—by default on some systems the box is not checked and it displays what is typed.
In the figure, our security type is WPA2-Personal. That means that we are connecting to a basic Wi-Fi access point, and that there is a pre-shared key (PSK) that allows access. It is stored on the AP. However, there are other options; some less secure, and some more secure. The no authentication option has no key, no security, but you might use that to temporarily make a network connection and download the required software. Many larger organizations will disable this out so that users and admins cannot connect without encryption. WEP is also listed which is generally not recommended because it can be compromised.
The more secure options include WPA2-Enterprise and 802.1X. WPA2-Enterprise, as the name implies, is designed for larger networks; ones that use an authentication server of some sort. That could be a RADIUS server or a Terminal Access Controller Access-Control System Plus(TACACS+) server. These can be used as centralized authentication platforms for wireless connections and a variety of other authentication purposes, and can be used as an SSO server as well. The more common Remote Authentication Dial-In User Service (RADIUS) provides centralized administration of dial-up, VPN, and wireless authentication and can be used with 802.1X as well. It uses ports 1812 and 1813 by default, and when connecting to a RADIUS server from a wireless client you often need to enter the port (1812) and the IP address of the server. Figure 32.2 shows an example of an access point that has been configured to redirect authentication requests to a RADIUS server using the IP 172.18.0.13 on the default port 1812.
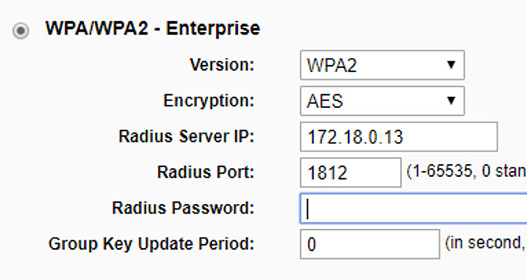
Figure 32.2 WPA2-Enterprise Configuration on an AP
RADIUS can be run on a variety of devices and servers including Windows Server. RADIUS can also be used as a multifactor authentication tool, or as part of an MFA scheme. This can be much more secure when compared to a single-factor authentication scheme such as a typical WPA2-PSK connection.
Note
802.1X is an IEEE standard that defines port-based network access control (PNAC). Not to be confused with 802.11x WLAN standards, 802.1X is an authentication technology used to connect hosts to a LAN or WLAN. 802.1X allows you to apply a security control that ties physical ports to end-device MAC addresses, and prevents additional devices from being connected to the network. It is a good way of implementing port security, better than simply setting up MAC filtering.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following is the strongest form of wireless encryption?
![]() A. WPA
A. WPA
![]() B. WEP
B. WEP
![]() C. AES
C. AES
![]() D. TKIP
D. TKIP
2. You have been tasked with connecting wireless clients to a server that supports SSO and 802.1X Which of the following technologies should you implement? (Select the two best answers.)
![]() A. WPA2-PSK
A. WPA2-PSK
![]() B. WPA2-ENT
B. WPA2-ENT
![]() C. WEP
C. WEP
![]() D. TKIP
D. TKIP
![]() E. RADIUS
E. RADIUS
Cram Quiz Answers
1. C. Advanced Encryption Standard (AES) is the strongest form of wireless encryption (given the listed answers). WPA is a wireless encryption protocol that is not bad, but WPA2 is recommended. WEP and TKIP are deprecated, have been compromised, and should be avoided. Only use WEP, TKIP, or the no authentication option, if you are temporarily connecting a device to a Wi-Fi network in an attempt to update it to a newer protocol, or if you are initiating testing. And even then, use extreme caution!
2. B and E. To take advantage of single sign-on (SSO) and 802.1X, you would need a special authentication device (such as RADIUS) on the server side, and WPA2-Enterprise on the client side (sometimes abbreviated as WPA2-ENT). And what port does RADIUS use by default? Remember?
WPA2-PSK uses a pre-shared key that is stored on the AP, and doesn’t support the other technologies. WEP and TKIP are outdated and should be avoided.
2.4 – Given a scenario, detect, remove, and prevent malware using appropriate tools and methods.
ExamAlert
Objective 2.4 focuses on: malware (ransomware, trojan, keylogger, rootkit, virus, botnet, worm, spyware) and the tools and methods for mitigating malware issues (antivirus, anti-malware, recovery console, backup/restore, rnd user education, software firewalls, DNS configuration).
Malicious software, or malware, is software designed to infiltrate a computer system and possibly damage it without the user’s knowledge or consent. Malware is a broad term used by computer professionals to include viruses, worms, Trojan horses, spyware, rootkits, keyloggers, adware, and other types of undesirable software.
Malicious Software Types
Of course, we don’t want malware to infect our computer systems, but to defend against it, we first need to define it and categorize it. Then we can put preventative measures into place. It’s also important to locate and remove/quarantine malware from a computer system in case it does manifest itself. Table 32.2 summarizes the various malware threats you should know for the exam.
Table 32.2 Malware Types
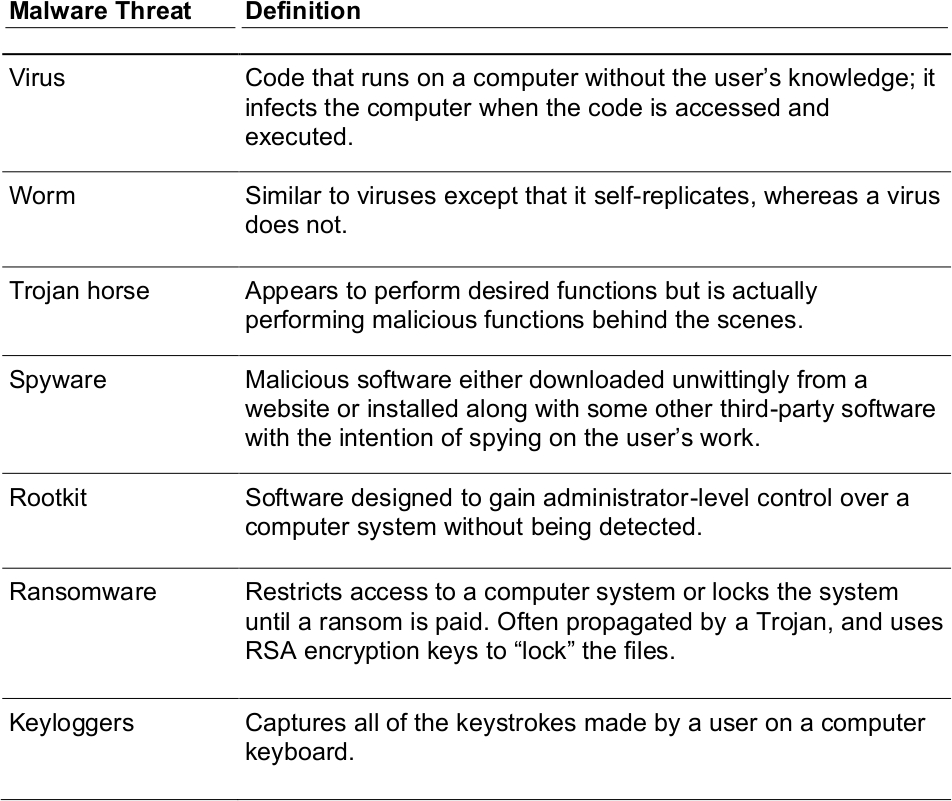
ExamAlert
Know the difference between a virus, worm, Trojan horse, rootkit, ransomware, and the other various malware threats!
Malware can be spread in a variety of ways including removable media, e-mail attachments, downloaded programs, malicious hyperlinks, and the dreaded botnet. A botnet is a group of compromised computers that are controlled by a master computer which directs them to attack particular servers and routers on the Internet. They call it a botnet because it is a network of computers—robots, or bots for short—that work as a collective. Usually, the computer is infected with a Trojan that contains the code to connect the system to the botnet. Unless the anti-malware program detects this, the user has no knowledge of it happening; it all occurs behind the scenes. Take a look at the Looking Glass Threat Map (https://map.lookingglasscyber.com/) to see current botnet attacks around the world. We’ll discuss botnets a little more later in this chapter.
Preventing Malicious Software
Now that we know the types of malware, let’s talk about how to stop them before they happen.
In a nutshell, prevention of malware infection can be performed by using anti-malware programs, updating the OS and apps, scanning the system, policies, and user education. But that’s just in a nutshell. Let’s dive a little deeper.
Preventing Viruses, Worms and Trojans
There is some confusion among people about the difference between viruses, worms and Trojans; even among some hackers and antivirus software developers. That’s because there are literally thousands of strains of malware (possibly much more), and they can be quite difficult to classify. To a certain extent it doesn’t matter. The bottom line is this: for the most part, prevention is the same for viruses, worms and Trojans.
We can do several things to protect a computer system from these. First, every computer should have antivirus (AV) software running on it. Companies that provide antivirus and anti-malware solutions often call them endpoint protection platforms. Second, that software should be updated. If the AV software is bundled with the OS—for example Windows Defender—, then the OS updates will take care of that. If it is third-party then it means that the software will require a current license; this is renewed yearly with most providers. Or if it is free, periodically check if it is still a full version of the software. If it isn’t already set to auto-update, set the AV software to automatically update at periodic intervals (for example, every day or every week). It’s a good idea to schedule regular full scans of the system within the AV software.
As long as the definitions have been updated, antivirus systems will usually locate viruses along with worms and Trojans. However, these systems will usually not locate rootkit activity. Keep in mind that AV software is important, but it is not a cure-all.
Next, we want to make sure that the computer has the latest updates available. This goes for the operating system and applications such as Microsoft Office. Backdoors into operating systems and other applications are not uncommon, and the OS manufacturers often release fixes for these breaches of security. For example, Windows offers the Windows Update program. This should be enabled, and you should either manually check for updates periodically or set the system to check for updates automatically. It might be that your organization has rules governing how Windows Update will function. If so, configure Automatic Updates according to your company’s policy. You can check whether your Windows computer is up to date by going to Control Panel > Windows Update, or Settings > Update & Security > Windows Update.
It’s also important to make sure that a firewall is available, enabled, and updated. A firewall closes all the inbound ports to your computer (or network) in an attempt to block intruders. The Windows Defender Firewall is a built-in feature of Windows, and you might also have a SOHO router with a built-in firewall. By using both, you have two layers of protection from viruses and other attacks. You can access the Windows Defender Firewall by navigating to the Control Panel or going to Run > firewall.cpl. Keep in mind that you might need to set exceptions for programs that need to access the Internet. This can be done by the program or the port used by the protocol and can be configured in the Exceptions tab, enabling specific applications to communicate through the firewall while keeping the rest of the ports closed.
Note
Another good technique when trying to prevent viruses (and just about any malware) is to disable AutoPlay/Autorun for USB-connected devices and optical drives. Plus, remember to disable these devices in the BIOS! We’ll discuss this more in Chapter 33, “Windows Security Settings and Best Practices.”
From a more generalized perspective, preventing malware is done through the use of a concept called defense in depth or layering of security, and by monitoring the system, as well as user education.
Educate users as to how viruses can infect a system. Instruct them on how to screen (or filter) their e-mails and tell them not to open unknown attachments. Show them how to scan removable media before copying files to their computers or set up the computer to scan removable media automatically. Sometimes user education works; sometimes it doesn’t. One way to make user education more effective is to have a technical trainer educate your users instead of doing it yourself. This can provide for a more engaging learning environment. During this training you might opt to define an organization’s acceptable use policy (AUP). This is a document stipulating constraints and practices that a user must agree to before being granted access to a corporate network or the Internet. Sometimes, the AUP can be a bit difficult for the average nontechie to understand. However, the document is usually designed to not only stipulate constraints but to educate the user, so it is in the user’s best interest to learn what policies are within the AUP.
By using these methods, virus infection can be severely reduced. However, if a computer is infected by a virus, you want to know what to do to troubleshoot the problem. We’ll get into that as well as the CompTIA A+ malware removal process in Chapter 37, “Troubleshooting PC Security Issues and Malware Removal.”
Worms and Trojans can be prevented and troubleshot in much the same manner as viruses. There are scanners for Trojans as well (for example, Microsoft’s Malicious Software Removal Tool). In some cases, AV software scans for worms and Trojans in addition to viruses. Both of these tools can easily detect known Trojans, regardless of whether it is the actual attacker’s application or any .exe files that are part of the application and are used at the victim computer. However, if the Trojan or worm is brand new, a hot fix or individual scanner might become available from your anti-malware provider. New Trojans and variants of Trojans are created every day. Until the anti-malware provider finds out about them, they are known as zero-day attacks (covered in more detail later in the chapter). The only way to prevent these is to stick to the fundamentals that we’ve discussed throughout this section.
Preventing and Troubleshooting Spyware
Preventing spyware works in much the same manner as preventing viruses in that spyware prevention includes updating the operating system and using a firewall. Also, because spyware has become much more common, antivirus companies have begun adding antispyware components to their software. Here are a few more things you can do to protect your computer in the hopes of preventing spyware:
• Download and install antispyware protection software. Your system might already have a program (for example, Windows Defender); if not, there are plenty of third-party programs available on the Internet. Be sure to keep the antispyware software updated. If you are using Windows, consider enabling SmartScreen for Microsoft Edge which checks web content and protects from malicious sites and downloads.
• Adjust web browser security settings. Enable a phishing filter if you have one and turn on automatic website checking. This attempts to filter out fraudulent online requests for usernames, passwords, and credit card information, which is also known as web-page spoofing. Enable checking of certificates. If a certificate (a secure encrypted connection on the web) has been revoked or is otherwise invalid, you want to know about it—a message such as “invalid certificate (trusted root CA)” will only be received when the browser is checking for it. If not, you could inadvertently stumble on to a disreputable website. Additional security settings can also help to fend off session hijacking; that is, the act of taking control of a user session after obtaining or generating an authentication ID. Another attack similar to session hijacking is browser redirection. This is when a user’s web browser is automatically redirected to one or more malicious websites. It can be done when a user inadvertently accesses a malicious website from a search; it can be caused by a Trojan that modifies a computer’s DNS entries (for example, DNSChanger); or it can be caused by spyware or a virus that configures a proxy server address within the browser and/or modifies the “hosts” file. Refer to Figure 29.7 in Chapter 29, “Windows Networking & Application Installation,” for an example of a proxy configuration on a Windows client. If this proxy server is not authorized, then it should be removed—after which you should restart the computer and verify that it is still disabled. Trojans such as these (and the ensuing spyware) can be avoided by increasing a browser’s security settings, updating antivirus programs, and by educating users. It can be fixed by scanning the system with antivirus software, removing the proxy server address from the browser’s settings, and deleting and rewriting the hosts file, which is located in %systemroot%\System32\drivers\etc.
ExamAlert
Understand how to disable or remove a proxy server configuration in the web browser.
• Uninstall unnecessary applications and turn off superfluous services (for example, turn off Telnet and FTP if they are not used).
• Educate users on how to surf the Web safely. User education is actually the number one method of preventing malware! Access only sites believed to be safe, and download only programs from reputable websites. Don’t click OK or Agree to close a pop-up window; instead, press Alt+F4 on the keyboard to close that window. Be wary of file-sharing websites and the content stored on those sites. Be careful of e-mails with links to downloadable software that could be malicious.
• Consider technologies that discourage spyware. For example, use a browser that is less susceptible to spyware. Consider running the browser (or the entire OS) within a virtual machine, or recommend a tablet or basic Internet appliances to users who use a computer to access the Internet only.
Preventing Rootkits
A successfully installed rootkit enables unauthorized users to gain access to a system, acting as the root or administrator user. Rootkits are copied to a computer as a binary file; this binary file can be detected by signature-based and heuristic-based antivirus programs. However, after the rootkit is executed, it can be difficult to detect. This is because most rootkits are collections of programs working together that can make many modifications to the system. When subversion of the operating system takes place, the OS can’t be trusted, and it is difficult to tell whether your antivirus programs run properly or any of your other efforts have any effect. Although security software manufacturers attempt to detect running rootkits, they are not always successful.
One good way to identify a rootkit is to use rescue removable media (a USB flash drive or optical disc) to boot the computer. This way, the operating system is not running, which means the rootkit is not running, making it much easier to detect by the external media.
Unfortunately, because of the difficulty involved in removing a rootkit, sometimes the best way to combat rootkits is to wipe the drive, and reinstall all software. Generally, upon detecting a rootkit, a PC technician will do this because it usually is quicker than attempting to fix all the rootkit issues and it can verify that the rootkit has been removed completely—as long as there is a backup for the data.
However, software isn’t the only method of defense and repair when it comes to rootkits. Newer motherboards equipped with a UEFI/BIOS take advantage of Secure Boot technology, which can help to protect the preboot process against rootkit attacks. This way, a rootkit can potentially be stopped before it actually causes any damage.
Backup/Restore and Recovery Environments
A good plan not only includes prevention methods, but also solid backup procedures. Backup as much as you can. This could be done on a file by file basis, using built-in Windows programs such as File History and Backup and Restore (Windows 7) as well as third-party programs; but it can also include the imaging of hard drives, creating a single file that incorporates the entire hard drive and all of its contents. Snapshots can be taken as well to mark a point in time, for example using System Restore. Any system that has important data should have a backup plan. Consider this whenever you build or deploy new systems. We’ll be discussing backup plans more later in the book.
In the case that malware does infect a system, we have to quarantine it, remove it, and recover the system. A great way to do this is to “think outside the box”, and boot the system to some type of recovery environment. This could be a Linux-based repair disc/drive, or we could use the built-in Windows Recovery Environment (RE). For more on this topic, see Chapter 36, “Troubleshooting Microsoft Windows.”
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following types of malware self-replicates?
![]() A. Virus
A. Virus
![]() B. Worm
B. Worm
![]() C. Trojan
C. Trojan
![]() D. Rootkit
D. Rootkit
2. Which of the following types of malware is designed to gain administrative-level control of a system?
![]() A. Ransomware
A. Ransomware
![]() B. Keylogger
B. Keylogger
![]() C. Rootkit
C. Rootkit
![]() D. Spyware
D. Spyware
3. You have been tasked with implementing a virus prevention plan on a group of Windows client computers. Which of the following should you carry out? (Select all that apply.)
![]() A. Update AV software
A. Update AV software
![]() B. Configure File History
B. Configure File History
![]() C. Update Microsoft Office
C. Update Microsoft Office
![]() D. Install a rootkit scanner
D. Install a rootkit scanner
![]() E. Verify that a firewall is installed
E. Verify that a firewall is installed
Cram Quiz Answers
1. B. A worm will self-replicate, whereas a virus will not; otherwise, the two are very much the same. Trojans perform malicious functions behind the scenes and allow remote access to systems. Rootkits are designed to gain administrator (or root) level access to the computer.
2. C. A rootkit is designed to get administrative control of a computer system. The word “root” is synonymous with administrator in many systems (Linux, Unix, etc…)
Ransomware is malware that encrypts a person’s files so that they are not accessible. Keyloggers capture the keystrokes a person makes on a keyboard. They are used to steal passwords and other confidential information. Spyware is malware that is used to watch (and possibly record) what a person is doing on the system and on the Internet.
3. A, C, and E. First off, update everything. Then, verify that AV software and a firewall are installed and updated. Be sure to update the OS and apps as well. Microsoft Office is especially susceptible to malware, so if you run it, you have to keep a close eye on it. Configuring File History or any other backup methods won’t prevent malware from occurring, but it is important to perform, nonetheless. Remember, backup is not prevention. A rootkit scanner won’t scan for viruses, and won’t prevent them; in fact, it won’t prevent rootkits, but it might find them.
2.5 – Compare and contrast social engineering, threats, and vulnerabilities.
ExamAlert
Objective 2.5 concentrates on the following: social engineering (phishing, spear phishing, impersonation, should surfing, tailgating, dumpster diving); DoS and DDoS; zero-day attacks; man-in-the-middle (MITM); brute force; dictionary; rainbow table; spoofing; non-compliant systems; zombie.
Social engineering is the act of manipulating users into revealing confidential information or performing other actions that are detrimental to users. Almost everyone gets e-mails nowadays from unknown entities making false claims or asking for personal information (or money!); this is one example of social engineering. Here are the social engineering techniques you should know for the exam.
Phishing
Phishing is the attempt at fraudulently obtaining private information. A phisher usually masquerades as someone else, perhaps another entity. Phishing is usually done by electronic communication/phone. Little information about the target is necessary. A phisher may target thousands of individuals without much concern as to their backgrounds. An example of phishing would be an e-mail that requests verification of private information. The e-mail will probably lead to a malicious website that is designed to lure individuals into a false sense of security to fraudulently obtain information. The website will often look like a legitimate website. A common phishing technique is to pose as a vendor (such as an online retailer or domain registrar) and send individuals e-mail confirmations of orders that they supposedly placed.
Specific groups of people might be targeted with more streamlined phishing campaigns; this is known as spear phishing. A campaign can even target specific individuals. This is common when targeting senior executives of corporations, a concept known as whaling.
As you can imagine, several different types of social engineering are often lumped into what is referred to as phishing, but actual phishing for private information is normally limited to e-mail and websites. To defend against this, a phishing filter or add-on should be installed and enabled on the web browser. Also, individuals should be trained to realize that reputable institutions and businesses will not call or e-mail requesting private information. If individuals are not sure whether they’re being targeted, they should hang up the phone or simply delete the e-mail. A quick way to find out if an e-mail is phishing for information is to hover over a link (but don’t click it!). You will see a URL domain name that is far different from the institution that the phisher is claiming to be—probably a URL located in a distant country.
Shoulder Surfing
Shoulder surfing is when a person uses direct observation to find out a target’s password, PIN, or other such authentication information. The simple resolution for this is for the user to physically shield the screen, keypad, or other authentication requesting devices. A technical method is to use a screen filter. A more aggressive approach is to courteously ask the assumed shoulder surfer to move along. Also, private information should never be left on a desk or out in the open. In fact, many organizations will have a “clean desk policy” that states this explicitly. Computers should be locked or logged off when the user is not in the immediate area. Shoulder surfing and the following several sections are examples of no-tech hacking.
ExamAlert
Use a screen filter to protect against shoulder surfing.
Piggybacking/Tailgating
Piggybacking is when an unauthorized person tags along with an authorized person to gain entry to a restricted area—usually with the person’s consent. Tailgating is essentially the same, yet with one difference: It is usually without the authorized person’s consent. Both of these can be defeated through the use of mantraps. A mantrap is a small space that can usually fit only one person. It has two sets of interlocking doors; the first set must be closed before the other will open, creating somewhat of a waiting room where people are identified (and cannot escape).
Multifactor authentication is often used in conjunction with a mantrap. Multifactor authentication is when two or more types of authentication are used when dealing with user access control (for example, using a proximity card and PIN at the first door and then using a biometric scan at the second). A mantrap is an example of a preventive security control. Turnstiles, double entry doors, and employing security guards are other less expensive solutions to the problem of piggybacking and tailgating and help address confidentiality in general.
Dumpster Diving
Dumpster diving is when a person scavenges for private information in garbage and recycling containers. Any sensitive documents should be stored in a safe place as long as possible. When they are no longer necessary, they should be shredded. (Some organizations incinerate their documents.) Information might be found not only on paper, but also on hard drives or removable media. Proper recycling and/or destruction of hard drives is covered later in the book. Another way to deter a person from attempting dumpster diving is to use security cameras and good lighting in the area where the dumpsters are stored; some organizations will keep their dumpsters indoors in a warehouse or similar area.
Impersonation
Impersonation is to present oneself as another person, imitating that other person’s characteristics. By impersonating the appropriate personnel or third-party entities, a person hopes to obtain records about an organization, its data, and its personnel. IT people and employees should always be on the lookout for impersonators and always ask for identification. If there is any doubt, the issue should be escalated to your supervisor and/or a call should be made to the authorities. Impersonation is often a key element in what is known as pretexting—the inventing of a scenario in the hopes that a key person will reveal confidential information.
Note
This objective covers more than just social engineering, but the following techniques are sometimes used by attackers and malicious insiders in addition to social engineering, and are therefore somewhat related.
Additional Attacks and Security Vulnerabilities
Because there are so many types of threats and vulnerabilities in today’s computers and networks, there are many types of attacks as well. Let’s briefly describe a couple more types of attacks and common vulnerabilities that a typical organization might have to face.
Network-based Attacks
A spoofing attack is when an attacker masquerades as another person by falsifying information. This can be done as a social engineering attack, such as in the previously mentioned phishing method, or it can be performed as a more technical attack, such as the man-in-the-middle (MITM) attack. This is when an attacker intercepts all data between a client and a server. It is a type of active interception. If successful, all communications are diverted to the MITM computer. The attacking computer can at this point modify the data, insert code, and send it to the receiving computer. This type of eavesdropping is only successful when the attacker can properly impersonate each endpoint.
Then there are attacks that exploit vulnerabilities that haven’t even been discovered yet or have been discovered but have not been disclosed through the proper channels so that security administrators can be aware of them. These are known as zero-day attacks. An attacker will exploit a vulnerability in an operating system or a network security device in such a way that makes it almost impossible to defend against. Because of this, zero-day attacks are a severe threat. Actually, most vulnerabilities are discovered through zero-day attacks, and the first group of systems that are attacked have very little defense. But once the attack is detected, the development of a solution is not far behind (it could be days or even hours); the vulnerability (and attack) becomes known and is no longer zero-day.
Most of the attacks and malware we have described so far can be initiated by zombies: computers that distribute the malware or participate in an attack without the knowledge of the owner. These zombies (or robots or bots) can be grouped together by a central attacker to form a botnet. This is done to perpetuate large-scale attacks against particular servers. The distributed denial-of-service (DDoS) is an example of an attack committed by a botnet; it is designed to bring down a server or website.
ExamAlert
In a DDoS attack, multiple systems are used to attack a server, website, or network.
Password Cracking
One way that attackers attempt to gain access to systems is by way of password cracking. This is usually done with the aid of password-cracking software. Two common methods of password cracking are the dictionary attack and the brute-force attack.
A dictionary attack uses a prearranged list of likely words, trying each of them one at a time. It can be used for cracking passwords, passphrases, and keys. It works best with weak passwords and when targeting multiple systems. The power of the dictionary attack depends on the strength of the dictionary used by the password-cracking program.
A brute-force attack is when every possible password instance is attempted. This is often a last resort because of the amount of CPU resources it might require. It works best on shorter passwords but can theoretically break any password, if given enough time and CPU power.
A cryptanalysis attack uses a considerable set of precalculated encrypted passwords located in a lookup table. These tables are known as rainbow tables, and the type of password attack is also known as precomputation, where all words in the dictionary (or a specific set of possible passwords) are hashed and stored. This is done in an attempt to recover passwords quicker. This attack can be defeated by implementing salting, which is the randomization of the hashing process. In usually incorporates key stretching, which is adding bits of information to the password to make it stronger.
Once again, a complex and long password is the best way to prevent these types of attacks from succeeding. But a system and its network should also be protected with the Internet security appliances mentioned previously.
ExamAlert
Know the differences between dictionary and brute-force attacks, as well as rainbow tables.
Security Best Practices
Most organizations have policies regarding security best practices. The biggest vulnerability to an organization is the violation of those best practices (namely, non-compliant systems). For example, an organization might have rules stating that all systems must be updated at particular intervals: operating systems, anti-malware applications, and so on. If a single computer fails to be updated, it is no longer in compliance with policy. This one computer could be used by a hacker or malicious insider to cause all kinds of harm, even on systems that are updated, simply because the nonupdated system is behind the firewall (on the LAN) with the rest of the computers. When updating systems, double-check that everything has indeed been updated. Use scanning software to find all systems on the network, and review network documentation to make sure no systems have “fallen through the cracks.”
Note
The previous section on “Additional Attacks” was a bit of a catch-all. Remember, the CompTIA A+ is not a security exam, but it does require that you know some of the basics about these concepts.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following describes an attempt to guess a password by using a combination of letters and numbers?
![]() A. Brute-force
A. Brute-force
![]() B. Social engineering
B. Social engineering
![]() C. Dictionary
C. Dictionary
![]() D. Zero-day
D. Zero-day
2. A user clicked a link that appeared to be from his bank. The link led the person to a page where it requested he change his password to access his bank account. It turns out that the webpage was fraudulent. What is this an example of?
![]() A. Impersonation
A. Impersonation
![]() B. Dumpster diving
B. Dumpster diving
![]() C. Phishing
C. Phishing
![]() D. Shoulder surfing
D. Shoulder surfing
3. Several hundred infected computers simultaneously attacked your organization’s server, rendering it useless to legitimate users. What kind of attack is this an example of?
![]() A. Botnet
A. Botnet
![]() B. MITM
B. MITM
![]() C. Tailgating
C. Tailgating
![]() D. DDoS
D. DDoS
![]() E. Rainbow table
E. Rainbow table
Cram Quiz Answers
1. A. Brute-force attacks use a combination of letters, numbers, and symbols to guess passwords, PINs, and passcodes; as opposed to dictionary attacks which uses a list of words. Social engineering is an attempt to manipulate people into providing confidential information. A zero-day attack is one that occurs that has not been seen or documented before—the most difficult to prepare against.
2. C. This is an example of phishing. Phishers will use e-mail to trick a person into divulging confidential information. While it could be said that the website that was accessed is impersonating the actual banking website, that would be more of a spoof; true impersonation is when a person mimics another person. Dumpster diving is when a person hunts through garbage or recycling to find confidential information. Shoulder surfing is when a person attempts to get information by sight, for example, looking over a person’s shoulder as that person types in a password.
3. D. A distributed denial of service (DDoS) attack is one where many computers (zombies) work together in an attempt to bring down a server or router. While it makes use of a botnet, not all botnets are necessarily bad, nor is the botnet the attack. A man-in-the-middle (MITM) attack is a type of spoof, where a person uses a computer to intercept and either use or change data that is captured. Tailgating is a type of social engineering attack where a person attempts to enter a secure area by following another person in without that person’s knowledge. A rainbow table is set of precalculated encrypted passwords located in a lookup table.
Now, some of things we talked about in this chapter may sound far-fetched, but they are real, and need to be proactively secured against. Continue!