Chapter 26. Microsoft Operating System Features and Tools, Part 1
This chapter covers a portion of the following A+ 220-1002 exam objective:
• 1.5 – Given a scenario, use Microsoft operating system features and tools.
Now let’s move into the graphical side of things. The Windows GUI is popular because users are familiar with it, and for many people its usage is intuitive; meaning it comes naturally. However, there are a lot of utilities, tools and features for an administrator to know. In fact, there are so many utilities that I split this objective into two chapters. In this chapter we’ll be covering some Administrative Tools, the System Configuration utility (MSConfig), and the Task Manager. This is important stuff, so let’s not waste any time.
1.5 – Given a scenario, use Microsoft operating system features and tools.
ExamAlert
This portion of Objective 1.5 concentrates on: administrative tools (such as Device Manager, Services, and the Event Viewer); MSConfig; and the Task Manager.
Administrative Tools
The administrator (that’s you) of a computer or network can access Administrative Tools from the Control Panel, and in Windows 10 by going to Start > Windows Administrative Tools, and in Windows 7 by going to Start > All Programs > Administrative Tools. Of course, you can also use the search tool. In addition, to get to the Administrative Tools directly, go to Run and type control admintools. You will find that different versions of Windows have different navigation paths to the same program. That’s why I recommend getting in the habit of using the Run prompt and typing the executable name of the program or tool you want to access. It works the same way across different Windows platforms, and in the long run will save you time.
Note
For a table of the Run commands that we cover in this book, see this link:
https://dprocomputer.com/blog/?p=3010
Some of the administrative tools are covered very briefly here, but most of those will be covered in more depth as we progress through the book. Either way, there are a lot of tools. One look and you’ll see, it’s a lot to know, so this is a big section. Let’s take them one at a time.
Computer Management
There are a lot of tools here used to configure advanced options for the computer. One example is Computer Management, which you will use quite often. It has many utilities loaded into one nice, little console window. Figure 26.1 shows an example of Computer Management.
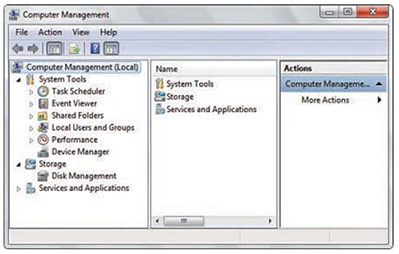
Figure 26.1 The Computer Management window
Note this is a three-pane window. The left pane has all the modules that you might work on, such as the Event Viewer, Device Manager, and Disk Management. The middle pane shows the details of whatever you click in the left pane. The right pane provides additional actions, which are also available on the Menu bar. There are a few other ways to open this window, including:
• In all versions of Windows: Access the Run prompt and type compmgmt.msc. The extension .msc defines the file type as a Microsoft Management Console Snap-in Control file, also known as Microsoft Console.
• In Windows 10 and 8: Right-click Start and then click Computer Management.
• In Windows 7: Click Start, right-click Computer, and then select Manage.
ExamAlert
Know how to access the Computer Management console window.
The MMC
Computer Management and other console windows can be grouped into one master console window known as the Microsoft Management Console (MMC) window. MMC acts as a shell for these other console windows. You can also use it to control remote computers in addition to the local computer. And you can control what particular users see by changing the Console Mode. Finally, part of the beauty of MMC is that it saves everything you added and remembers the last place you worked. To create an MMC window, open the Run prompt and type MMC. By default, the MMC window is empty.
Note
You will learn quickly that administrative functions should be carried out only by users who have administrative privileges. Even if you have administrative privileges, a pop-up User Account Control (UAC) window displays every time you try to access tools such as the MMC. Simply click Yes or Continue to open the program. If users don’t have administrative capabilities, they will be blocked altogether or when the UAC window pops up, they won’t be able to continue.
To add consoles (known as snap-ins), do the following:
1. On the Menu bar, click File and then click Add/Remove Snap-in. The Add/Remove Snap-ins window should appear.
2. Select the components you want from the left by highlighting them one at a time and clicking the Add button. You need to select the local computer or a remote computer. Click OK when finished. These snap-ins should now be shown inside of the Console Root. Figure 26.2 shows an example MMC.
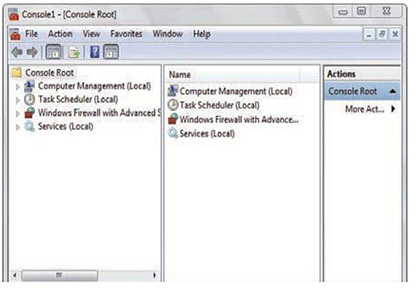
Figure 26.2 The MMC
3. Save the MMC. By default, this window prompts you to save to the Administrative Tools folder of the user who is currently logged on.
Device Manager
A computer probably has a dozen or more devices that all need love and attention. Taking care of a computer means managing these devices. The primary tool with which a technician does this is Device Manager.
There are a few ways to open Device Manager, for example:
• Open it from the Control Panel (in icons mode). You can get to it from a lot of locations in the Control Panel by the way.
• Open Computer Management, expand System Tools, and then select Device Manager. (Don’t forget, you can also open Computer Management as a snap-in within an MMC.)
• Open the Run prompt and type devmgmt.msc. (as always, my favorite.)
When Device Manager opens, you will notice that there are categories for each type of device. By expanding any one of these categories, you will see the specific devices that reside in your computer. Figure 26.3 shows Device Manager.

Figure 26.3 Device Manager
By right-clicking a specific device, you can update its driver; enable or disable it; uninstall it altogether; check for any hardware changes; or access additional properties, such as the driver details and resources used by the device. Figure 26.3 shows the resulting menu when right-clicking an Intel network adapter. These are the standard options, but your options might be more or less, depending on the device you have right-clicked.
ExamAlert
Know how to access the properties of a device, install drivers, and enable/disable devices in Device Manager.
Some drivers are installed/updated through .exe files that are downloaded from the manufacturer’s website. Others are installed from within Device Manager. Device Manager can search for drivers automatically, or you can manually install the driver by browsing for the correct file (often, it’s a file with an .inf extension). Windows attempts to install drivers automatically when it recognizes that a device has been added to the system. Usually, however, it is recommended that you use the driver disc that came with the device or that you download the latest version of the driver from the manufacturer’s website, especially when dealing with video, audio, and hard drive controller drivers.
Local Users and Groups
This utility can be accessed from the Administrative Tools list, and also from within Computer Management > System Tools. You can access it directly by going to Run, and typing lusrmgr.msc.
While you can add users within the Control Panel (or in Settings in Windows 10), this is where you go if you want to take more control of user account management. From here, you can add users, change passwords, group those users together, or take advantage of the built-in Windows groups such as Backup Operators, and Performance Monitor Users.
Local Security Policy
This is where you make the rules! —or configure the rules as put forth by your organization. You can access this from Run by typing secpol.msc. Here you can configure the policies for passwords, account lockout, encryption keys, software restriction, and much, much more. I usually add this as a snap-in to my MMC. The content within the LSP is a subset of the Local Group Policy Editor content which can be accessed from Run > gpedit.msc. We’ll be revisiting both of these in the security section of this book.
Performance Monitor
There are several tools you can use to track the performance of a Windows-based computer. The Performance Monitor is an extensive program that can track how much your devices are utilized; for example, what percentage of the processor is used or how much RAM is currently being accessed. It uses real-time ActiveX graphs to track usage, and can log the information for later viewing. It can be accessed from Run > perfmon.exe. Figure 26.4 shows an example.

Figure 26.4 Performance Monitor in Windows
By working with Performance Monitor, you can track the usage of any device in the computer (known as objects) and you can track it using a variety of measurements (known as counters). By default, this screen tracks only the CPU. By clicking the + sign toward the top of the window, you can add devices to track—and in myriad ways. In Figure 26.4, I added the default counters for memory and the network adapter card. The highest spikes are from the network adapter; at the time of this monitor, it is sending and receiving a lot of data over the Internet. The second highest levels are from the processor, which is running about seven real-time applications simultaneously.
Information can be viewed in different formats, such as line charts and histograms, and can also be viewed and saved in Report view. They can be exported as well. However, any objects that are added in this program are not saved when you close the window. But you can configure the program so that it saves your additions; enter the MMC. From an MMC, a user in Windows can add the Performance Monitor. You can also use the System Monitor Control snap-in, which effectively is the Performance Monitor; it is one of the ActiveX Controls that can be added to the MMC. In addition, you can add Performance Logs and Alerts to log your findings and alert you to any changes or tripped thresholds. The MMC saves its contents and remembers the last place you were working in, which works great if you will be analyzing the same things day in and day out.
The Performance Monitor (and similar Windows applications) can tell you a lot about the functionality of your computer. When troubleshooting why a certain piece of hardware isn’t living up to its reputation, it can be invaluable.
Note
Other tools that can be used to track resource usage include the Resource Monitor (Run > resmon.exe) and the Performance tab of the Task Manager, though these are not as thorough as the Performance Monitor, nor do they have the ability to save the tracked resource usage.
Services
The Services console window is where you go to start, stop, and restart services—such as the Print Spooler—as well as configure their startup type. For example, if the Windows Firewall service was interfering with another application, you could stop the service from here, and see if that fixes the problem (at least temporarily). We’ll be covering this more during the Windows troubleshooting section of the book. You can access it directly from Run > services.msc, and it is also available within Computer Management.
Task Scheduler
The Task Scheduler can run particular programs, send e-mails, or display messages at a scheduled time (or times) designated by the user. You can open it from Administrative Tools, by going to Run and typing taskschd.msc, or by using the search option and typing schedule. Aside from basic scheduling, you can specify certain conditions and triggers that cause a task to run, and you can tell the scheduler which actions to take when the task starts. Plus, there are a slew of built-in preprogrammed tasks in the Task Scheduler Library—from memory diagnostics to registry backups. Instead of re-creating the wheel, consider using one of these tasks to help automate the process. Some of these built-in tasks are enabled by default. Try creating some tasks yourself, such as memory diagnostic, registry backup, and time synchronization.
Print Management
This utility allows you to install, configure and troubleshoot multiple printers, drivers, ports, print servers, and more, all from a single window. It’s a must for technicians that deal with company printers, and can be added to the MMC (for local and remote systems), and can be accessed directly from Run > printmanagement.msc.
Windows Memory Diagnostics
In Chapter 10, “RAM and Storage,” we talked about several ways to troubleshoot RAM. One way is to use Windows Memory Diagnostics. You might need to check your memory while within Windows, or perhaps Windows won’t boot, and you want to check the memory from bootup. Because of this, there are a couple of other ways to open this tool: by accessing Run and typing mdsched, or by booting to the Windows Recovery Environment (Windows RE), which we will cover in Chapter 36.
If you do this from within Windows, a pop-up window asks you if you want to restart the computer immediately and run the check or wait until the next time the computer is restarted. The Windows RE (Startup Settings) method starts the check immediately. The test checks if there are any physical issues with the RAM and attempts to identify which memory module is causing the problem. When done, it restarts the computer automatically. If an error is found, it displays after you log back on. You can also view errors in the System log of the Event Viewer. To find results quickly, right-click the System log, click Find, and enter MemoryDiagnostics-Results. If there are errors with a particular stick of memory, try removing it, cleaning it and the RAM slot, and reseating it. Run the test again; if you get the same results, replace the RAM.
Windows Defender Firewall with Advanced Security
The Windows Defender Firewall with Advanced Security is part of the built-in firewall designed to block intrusion to the operating system. The main difference between this and the basic Windows Defender Firewall within the Control Panel is the ability to create rules for incoming and outgoing traffic. You can open the basic firewall directly from Run > firewall.cpl, and the Windows Defender Firewall with Advanced Security directly from Run > wf.msc. We’ll be discussing both in more depth in the security section of this book.
Event Viewer
Applications are a boon and a bane to mankind. They serve a purpose, but sometimes they are prone to failure. The operating system itself can cause you grief as well by underperforming, locking up, or causing other intermittent issues. One good tool for analyzing applications and the system is Event Viewer.
Event Viewer tells a technician a lot about the status of the operating system and programs. It notifies of any informational events or audits, warns about possible issues, and displays errors as they occur. Aside from being within Administrative Tools, it can be accessed from the System Tools node in the Computer Management console window, or by typing eventvwr.msc in the Run or Search prompts. Try opening it on your system!
Information, auditing entries, warnings, and errors are stored in several log files within the Windows Logs folder. Of those, there are three main log files that you should know for the exam:
• System: The System log contains information, warnings, and errors about hardware, device drivers, system files, and so on. This log deals primarily with the operating system.
• Application: The Application log contains events about programs that are built into Windows, such as the Command Prompt or File/Windows Explorer, and might contain information about applications that have been loaded after the operating system was installed.
• Security: The Security log holds information that was gathered for auditing and security purposes; for example, it might log who logged on to the computer or who tried to gain access to a particular file.
An event can be viewed by double-clicking it. Events are organized into four categories:
• Information: Indicated by an “i” in a circle. This tells you basic information about a service starting or an application that ran successfully. The log files are usually chock-full of these as part of the normal operation of the system.
• Warning: Indicated by an exclamation point “!” within a yellow triangle. This might be a message telling you an installation did not complete or a service timed out. You should check for these now and again and investigate them if nothing else is pressing.
• Error: Indicated by an exclamation point “!” in a red circle. This means that something failed or has been corrupted, a service failed to start, and so on. Errors should be investigated right away.
• Audit Success: Indicated by a gold colored key; these entries are located within the Security log file. They track what a user attempts to accomplish within the operating system. For example, if auditing was turned on for a specific folder and a person attempted to access that folder, a security event would be written to the log, especially if the person was denied access. Auditing entries are maintained by organizations so that they can trace what happened to deleted or modified data.
You can find more information about a specific error code by either typing the code number for the event or typing the description into Microsoft Help and Support: https://support.microsoft.com. Sometimes you can find out information about these types of services just by running a search, but it is best to go to the source: Microsoft. You never know when an error can occur, so the Event Viewer logs should be reviewed regularly. Entire logs can be erased by right-clicking the log file (for example, System) and selecting Clear Log. The system asks if you want to save the log for future viewing. By right-clicking a log and selecting Properties, you can modify the maximum size of the log and disable logging altogether.
ExamAlert
Be able to describe the System, Application, and Security log files as well as the information, warning, error, and audit success events.
Component Services
Component Services is a snap-in you can add to the MMC. It allows you to configure and administer three types of components: the Component Object Model (COM), COM+ Applications, and the Distributed Transaction Coordinator (DTC).
COM is a software interface used to allow interprocess communications and dynamic object creation by using different programming languages. The term COM includes the following technologies: ActiveX controls (such as the real-time charts found in Task Manager), Object Linking and Embedding (OLE databases), COM+ (an extension to COM, providing better memory and processor management), and DCOM (programming as it relates to networked computers).
The Microsoft Distributed Transaction Coordinator (MSDTC) is a relatively newer component of Windows that uses a transaction manager to coordinate information between databases, file systems, and other resources. It works in conjunction with COM and .NET architectures.
For more information on Component Services administration, visit http://technet.microsoft.com/en-us/library/cc731901.aspx.
If certain Dynamic-Link Libraries (DLLs) or ActiveX controls need to be troubleshot (for example, ones that work with Internet Explorer), they can be registered or unregistered within the Windows Registry by manipulating them with the regsvr32 command. For example, to register a sample ActiveX control, you would open the Command Prompt (as an administrator) and type regsvr32 sample.ocx. Unregistering requires the /u parameter. To register a .DLL file, you would type regsvr32 msi.dll, replacing msi with whatever DLL you wish to register or unregister.
Note
More information on regsvr32can be found at:
Data Sources (ODBC)
Open Database Connectivity (ODBC) is an interface used within the C programming language to access database management systems. It is primarily used by Microsoft for its SQL database systems but can also be utilized by Microsoft Access Databases, dBASE, or Excel files. Different applications within Windows and from third-party vendors might make use of one of these technologies and will, therefore, need ODBC. If you want to make configuration changes to ODBC, you can access it by going to Administrative Tools and then clicking ODBC Data Sources. That opens the ODBC Data Source Administrator. From here, you can add or remove Database Source Names (DSNs), which are data structures that describe a connection to a data source. DSNs include the name of the data source, the folder it is located in, the driver used to access the data source, and so on. For example, if you wanted to run a program in Windows 7 that was reliant on a SQL Server database, or if you just wanted to make a connection to a SQL database, you would need to add the Microsoft SQL Server data source to the User DSN list. The name of the SQL Server would be required to complete the connection. For more information on ODBC in Windows, visit https://technet.microsoft.com/en-US/library/ms187039(v=sql.105).aspx.
Note
The previous two sections (COM and ODBC) and REGSVR32 deal with in-depth system configuration and application developing within Windows, going a bit beyond what a PC technician will usually be required to perform. That’s why I put them at the end of the Administrative Tools section. However, they are listed on the CompTIA A+ objectives, so you should at least know what they are and how to access them in Windows.
System Configuration/MSConfig
Msconfig is the commonly used name for the System Configuration tool. It can help to analyze and troubleshoot various things, from operating system startup issues to application and service problems. To open Msconfig in Windows 10 go to Start > Windows Administrative Tools and click System Configuration, or in any version of Windows, open the Run prompt and type msconfig.exe (or simply msconfig). A program similar to Figure 26.5 should display.

Figure 26.5 System Configuration (Msconfig) application
This is an excellent troubleshooting tool that has multiple tabs that do the following:
• General: You can configure the system for diagnostic or selective startup. This helps to troubleshoot devices or services that are failing.
• Boot: You can modify OS bootup settings, such as using Safe boot, logging the boot process, and booting without video. If you have multiple operating systems, you can change the order and choose which to set as default (instead of configuring the BCD file). Also, the advanced options let you choose things such as how much memory you want to use and what port to use if you need to output debugging information.
• Services: This tab lists the services and their current status. You can enable or disable them from here (it requires a computer restart). However, you can’t start or stop them. To do that, you would need to go to the Services section of Computer Management or do it from within the Command Prompt. The beauty of this tab is the speed at which you can enable/disable services compared to other options in Windows.
• Startup: In Windows 10 and 8, the Startup tab still exists but displays “To manage Startup items, use the Startup section of Task Manager” and it provides a link to open Task Manager. In Windows 7 it displays the various applications that start when the computer boots up that can be disabled and enabled.
• Tools: This tab lists a lot of the common utilities you might use in Windows and allows you to launch them from there. As a launching point for programs we have used a lot (Computer Management, System Properties, Task Manager, Command Prompt, and so on), this section of Msconfig can be a real time-saver.
Consider Msconfig as a time-saver when changing boot settings, working with services, and troubleshooting the system. One word of caution: Be sure to reset Msconfig to the regular settings when you finish using it. For example, if a user complains about a system booting to Safe Mode every time or other similar problems in which the user doesn’t have full access to the system, Msconfig might need to be reconfigured to Normal Startup.
ExamAlert
Know the reasons to use Msconfig.
Task Manager
One simple, yet effective, tool to use when analyzing the computer is Task Manager. There are several ways to open Task Manager, including
• Right-click on the taskbar and select Task Manager.
• Press Ctrl+Alt+Del and select Task Manager.
• Open the Run prompt and type taskmgr.
• Press Ctrl+Shift+Esc.
Task Manager gives you the ability to analyze your processor and memory performance in real time; this can be done from the Performance tab, as shown in Figure 26.6. This shows the Performance tab and Processes tab. You can see from the figure that the CPU usage fluctuates and is currently at 10%, but importantly in the figure, the Firefox and Chrome browsers are using the bulk of the memory on that system.

Figure 26.6 Windows Task Manager showing the Performance and Processes tabs
Optimizing the system can be as simple as shutting down programs. In Windows 10 and 8, “Apps” are shut down in the Processes tab. In Windows 7, programs can be shut down in the Applications tab. But sometimes you need to shut down the underlying process. For example, the Processes tab in Figure 26.6 shows all the processes that are running and the amount of CPU and RAM resources they are using individually. A process that is hording resources can be stopped by right-clicking it and then selecting End Task in Windows 10/8, and End Process in Windows 7. (This can also be done in the Details tab of Windows 10/8.) Keep in mind that this shuts down only the process or application temporarily. If it is designated to do so, it will turn back on when the computer is rebooted.
ExamAlert
Understand how to open Task Manager, how to read its Performance tab, and how to end processes and applications.
The Task Manager has several other tabs. For example, the Users tab shows the resources being used by each user. Normally, on a Windows client computer, this will only show the currently logged in user. However, if another user is listed, and that account is using resources, then that user can be signed off from here (just right-click the user, and select sign off). This way, the resources are freed up. For example, if a remote user was connected previously, and chose to disconnect instead of logging off, then it will show that user as “Disconnected”, but it might still be using memory resources because the user left some programs opened before disconnecting. This is common with remote desktop sessions. That’s the difference between disconnecting and logging off when you disconnect, the programs and resources are left open allowing you to reconnect later and continue where you left off; but when you log off, the programs are closed, and the resources are freed up. Try working with the Task Manager on your system and get to know the program, you will be using it often.
Note
The Windows 7 Task Manager has a Networking Tab which shows statistics relating to each of the network adapters present in the computer including percentage of network utilization, and the link speed and state of the network adapter.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following should be typed in the Run prompt to open Device Manager?
![]() A. MMC
A. MMC
![]() B. secpol.msc
B. secpol.msc
![]() C. CMD
C. CMD
![]() D. devmgmt.msc
D. devmgmt.msc
2. Which of the following would you use to track what percentage of resources are being used?
![]() A. devmgmt.msc
A. devmgmt.msc
![]() B. eventvwr.msc
B. eventvwr.msc
![]() C. systempropertiesadvanced.exe
C. systempropertiesadvanced.exe
![]() D. perfmon.exe
D. perfmon.exe
3. Where can a user go to start and stop services in Windows? (Select all that apply.)
![]() A. msconfig
A. msconfig
![]() B. Task Manager
B. Task Manager
![]() C. Computer Management
C. Computer Management
![]() D. Command Prompt
D. Command Prompt
4. Which log file in the Event Viewer contains information concerning auditing?
![]() A. System
A. System
![]() B. Application
B. Application
![]() C. Local users and groups
C. Local users and groups
![]() D. Security
D. Security
5. You are preparing to troubleshoot a system that is having some driver issues. Which of the following tools should you use to configure the system to boot safely?
![]() A. Event Viewer
A. Event Viewer
![]() B. Performance Monitor
B. Performance Monitor
![]() C. Local users and groups
C. Local users and groups
![]() D. System Configuration
D. System Configuration
![]() E. MMC
E. MMC
6. Which tool can run particular programs at a time designated by the user?
![]() A. Services
A. Services
![]() B. Task Scheduler
B. Task Scheduler
![]() C. Event Viewer
C. Event Viewer
![]() D. Windows Memory Diagnostics
D. Windows Memory Diagnostics
Cram Quiz Answers
1. D. Devmgmt.msc is the Microsoft console window known as Device Manager. MMC opens up a new blank Microsoft Management Console. Secpol.msc opens the Local Security Policy window. CMD opens the Command Prompt.
2. D. perfmon.exe opens the Performance Monitor utility which is used to graphically track the resources that are being used on a computer such as CPU, RAM, and so on. You could also use the Task Manager > Performance tab to track resource usage (but without the ability to save the data, as well as the Resource Monitor. Devmgmt.msc opens the Device Manager. Eventvwr.msc opens the Event Viewer. Systempropertiesadvanced.exe (if typed in the Run prompt or Command Prompt) opens the System Properties dialog box to the Advanced tab.
3. B, C, and D. You can start/stop services in the Task Manager > Services tab; Computer Management > Services section; and in the Command Prompt using the net start, net stop,sc start, and sc stop commands. Msconfig is not a correct answer because it lets you enable/disable services, but does not start/stop them.
4. D. The Security log contains information about auditing and other security events. The System log contains information about the OS and system files. The Application log contains information about built-in Windows programs and some third-party programs. Local Users and Groups is the administrative tool used to add people and systems to the local computer.
5. D. Use the System Configuration utility (msconfig) to configure the system to boot safely by going to the Boot tab and check marking the Safe boot option as shown in Figure 26.7. In the figure it is configured as minimal (the default), meaning that the system will boot with a minimal set of drivers and programs; but there are several other options listed there. Make sure you go through the Windows utilities and all the tabs—know what everything does!

Figure 26.7 System Configuration utility displaying the Boot tab
6. B. The Task Scheduler can run particular programs at a scheduled time (or times) designated by the user. The Services console window is where you go to start, stop, and restart services. The Event Viewer is used to find out messages about the system, applications, and security developments. Windows Memory Diagnostics is used to analyze the computer’s RAM for errors.