Wireless security, or to put it more accurately, fears about wireless insecurity, is one of the major topics in the IT industry today. This fear of insecurity is a major obstacle to worldwide wireless market expansion and is taxing the minds of many senior IT personnel. In accordance with many statements by wireless security salespeople heard at major conferences and exhibitions such as the recent 2003 Wireless Event in London, “Wireless insecurities and threats are put on the map by a new advanced technology developed in recent years to provide novel forms of mobile networking.” In reality, the history of radio signal interception and jamming predates modern network sniffing and denial of service (DoS) attacks by more than half a century, going back to the First World War. The first wireless LAN was operational in 1969—four years before the Ethernet’s birth. In fact, this network, the ALOHA packet radio net deployed by the University of Hawaii, gave Bob Metcalfe from Xerox PARC an idea that led to the creation of the CSMA/CD algorithm (which Metcalfe initially called Alto Aloha Network), thus facilitating the emergence of DIX Ethernet and the 802.3 standard.
The increasing use of modern wireless networks with their inherent security problems adds another level of concern for systems administrators and network security professionals, who already are overworked dealing with the more familiar system flaws exploited by wired network crackers. To offer protection against network attacks via wireless, knowledge of radio frequency (RF) fundamentals is essential. The data-link layer of wireless networks is significantly different from the corresponding layer of their wired equivalents, and there are known security issues related to layer 2 protocols on wireless nets. Thus, it is imperative that the professionals responsible for securing such networks be well versed in layer 2 wireless protocol standards and operations. Outlining layer 1 and 2 wireless structure and functionality from a security professional’s viewpoint is the main aim of this chapter. The rest of the chapter deals with the issues of wireless penetration testing and network hardening in different wireless network settings and topologies.
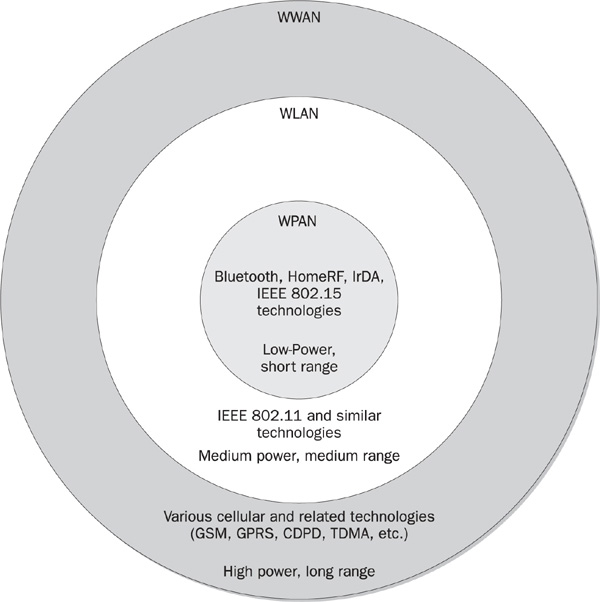
All wireless networks can be divided into high-power and long-range wireless WANs, medium-power and medium-range wireless LANs, and low-power and low-range wireless PANs (see Figure 13-1).
This division is not without exceptions: 802.11b point-to-point links can extend 20–25 miles, efficiently becoming wireless WAN connections; Bluetooth access points can cover a 100-meter radius at 100 mV power output in the absence of significant physical obstructions and interference.
FIGURE 13-1 Overview of modern wireless networks
NOTE The wireless network range limitation depends on the transmitter characteristics and is best checked in the manual coming with your particular client card or access point. 802.11b/g WLAN cards usually have 15–23 dBi of transmission power; 20 dBi is the current “unofficial standard.” The receiving sensitivity lies in range –80 - 90 dBm. Without using external antennas and amplifiers, this gives us the distance range of 100 m–1 km, depending on whether it is an indoors or outdoors network, present obstacles, building walls material, interference, and other factors. 802.11a WLANs have shorter range, since the free space path loss (explained later in the chapter) grows with increasing frequency.
Wireless WAN security is strongly dependent on the link type as well as the settings and hardware supplied by the WAN link provider. All the site’s systems administrator can do to improve the security of such a link is to treat it as a connection to a large insecure public network (it probably is) and ensure proper network separation and gateway security. Additionally, appropriate authentication and data encryption should be implemented in agreement with the link provider. On the contrary, wireless LANs and PANs are usually in a control domain of the enterprise/organization network managers and administrators, and it is their responsibility to ensure a reasonable level of security on such networks. The focus of this chapter is thus on protecting wireless local and personal area networks from external attackers and internal malcontents.
It is an accepted fact in IT security that in order to defend something against attacks, you have to know well what you defend. Unfortunately, this is not the norm in wireless networking, because the majority of network/IT security professionals lack essential knowledge of radio technology, as this knowledge is not typically included in computer science degree courses or common IT certification preparation materials. At the same time, RF experts who switch to the IT field may not be familiar with networking protocols, in particular complex security-related protocols such as IPSec.
NOTE A good way to get a solid knowledge of wireless networking basics is to prepare for and pass the vendor-independent CWNA (Certified Wireless Network Administrator, www.cwne.com/cwna/index.html) examination or other qualifications provided by Planet3 Wireless. To pass the exam, you will have to possess some hands-on wireless networking experience.
The security benefits of knowing RF fundamentals include these things:
• Proper network design Security must be taken into account at the earliest stage of network planning and design. This applies to wireless networks design even more than to its wired siblings. Badly designed wireless networks are unfortunately quite common and easy to spot; they possess low resistance to DoS attacks and tend to slow down to a standstill if network traffic overhead is increased by VPN deployment. Remember that despite the latest developments in wireless networking (for example, the 802.11a and g standards), wireless LANs and PANs still have lower throughput and higher latency than their wired counterparts.
• The “need to access” principle The coverage zone of your wireless LAN should be able to provide user access where it is needed and not anywhere else. The LAN must be installed and designed in such a way as to encompass your premises’ territory and minimize outside signal leakage as much as possible. This will ensure that the potential attackers have less opportunity to discover your network, less traffic to collect and eavesdrop on, and a lower bandwidth to abuse, even if they are successful at circumventing your security measures and manage to associate with the network. It also means that the attacker will have to stay close to your offices, which makes triangulating and/or physical and CCTV spotting of wireless crackers much more likely to succeed.
• Distinguishing security violations from other reasons for network malfunctioning and avoiding accidental signal pickup Is it radio interference, or has someone launched a DoS attack? Are these SYN TCP packets coming because the sending host cannot receive SYN-ACK properly, or is a “packet kiddie” trying to synflood your servers? Why are there so many fragmented packets on the network? Is a cracker running nmap -ffff / hping -f, or was it necessary to tweak your wireless LAN MTU value due to the frequent retransmits when large packets are sent? The majority of problems on wireless networks can be traced to layer 1 connectivity issues. Some of these problems can be caused by neighboring wireless LANs. You shouldn’t transmit on the same frequency as your neighbors or one close to it for at least two reasons: interference and their accidentally tapping into your data. If you run on a frequency range close to a neighbor, they could legitimately receive your information by accident. If they run a WEP cracking tool to evaluate their own LAN security, they may crack your WEP key by accident. Even if it is deliberate, how do you prove it?
• FCC regulations compliance You don’t want to get in trouble with the Federal Communications Commission in the U.S. or its equivalents abroad. Since wireless LAN/PAN devices operate in unlicensed bands, the only way these wireless networks can break the regulations is by using inappropriately high transmission power. Apart from creating possible legal problems, very high transmission power goes against the “need to access” principle (see the earlier point).
The majority of issues pertaining to wireless network layer 1 security can be solved by tuning the transmitters’ output power, choosing the right frequency, selecting the correct antennas, and positioning them in the most appropriate way to provide a quality link where needed, while limiting your network’s “fuzzy” borders. Proper implementation of these measures requires knowledge of RF behavior, transmitter power estimation and calculations, and antenna concepts.
A radio frequency signal is a high-frequency alternating current (AC) passed along the conductor and radiated into the air via an antenna. The emitted waves propagate away from the antenna in a straight line and form RF beams or lobes, which are dependent on antenna horizontal and vertical beam width values. There are three generic types of antennas, which can be further divided on subtypes:
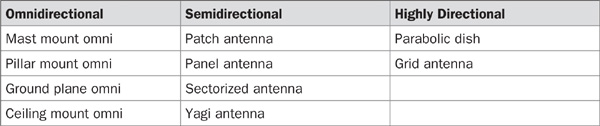
TIP Familiarize your security guards with the appearance of various wireless equipment types, such as antennas and PCMCIA cards. This is a part of a general vigilance and incident response practice. The guards should not normally chase people with wireless client cards around, but if something strange (new MAC addresses not on the access list, a sudden bandwidth consumption increase, a wireless IDS alarm triggered) takes place on the network, the guards should be told to look out for misplaced wireless equipment, users connecting at inappropriate times or just looking out of place, e.g., teenagers or complete strangers or users of equipment (antennas, laptops) not handed to the employees by this particular company. Something like a typical 802.11 antenna sticking out of an apartment block window across the road should also sound an alert, and it makes sense to check if an employee really lives there. Another common suspicious case is someone in a car with a laptop and car-mounted antenna. Small ground plane omnidirectionals with magnetic mounts are commonly sold as parts of “wardriver kits” and are very popular among wardrivers.
Antennas are wireless network designers’, administrators’, and consultants’ best friends. They can also be their worst enemy in the hands of a skillful attacker, increasing her range, the amount of data captured, and the connection speed, should the attacker manage to associate with the target network.
Examples of antenna irradiation patterns are given in Figure 13-2. When choosing necessary antennas, you need to consider antenna irradiation patterns. Get it right, and your coverage is exactly where you need it. Get it wrong, and there are dead areas where no one can connect, or worse, you exceed the normal boundaries of your environment and broadcast the presence of your network to those who should not know about its existence.
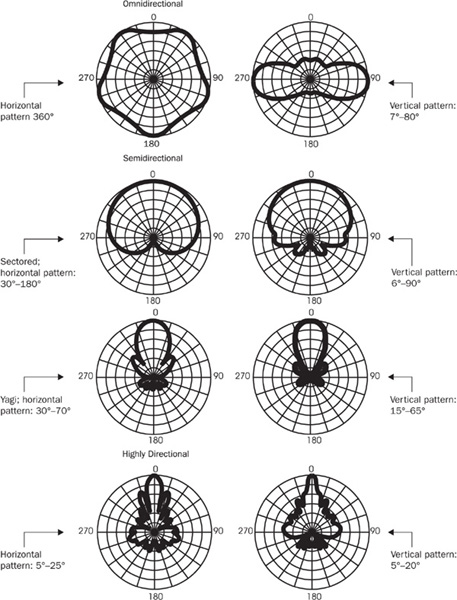
FIGURE 13-2 Examples of antenna irradiation patterns supplied with quick antenna type–specific beam width reference values
When planning the network coverage, remember that the irradiation happens in two planes: horizontal and vertical. Try to envision the coverage zone in three dimensions: for example, an omnidirectional beam forms a doughnut-shaped coverage zone with the antenna going vertically through the center of the “doughnut” hole. Sectorized, patch, and panel antennas form a “bubble” typically spreading 60–120 degrees. Yagis form a more narrow “extended bubble” with side and back lobes. Highly directional antennas irradiate a narrowing cone beam, which can reach as far as the visible horizon. Horizontal and vertical planes of semi- and highly directional antennas are often similar in shape but have different beam widths; consult the manufacturer’s description of the antenna irradiation pattern before selecting an appropriate antenna for your site.
NOTE The irradiation patterns shown in Figure 13-2 are taken from the manufacturers’ descriptions of representative antenna types. Traditionally, the descriptions of antenna beams are presented as drawn schemes for the sake of clarity. Here, this tradition is broken on purpose—the reality is different. An attacker can be positioned behind the Yagi or even a directional dish and still be able to discover the network and eavesdrop on passing traffic.
As you can see from the patterns shown in Figure 13-2, the omnidirectional antennas are typically used in point-to-multipoint (hub-and-spoke) wireless network topologies, often together with a variety of semidirectionals.
TIPS Here are some tips for choosing antennas for wireless networks:
Use omnidirectional antennas only when they are really needed. In many cases, a sectored or panel antenna with the same gain can be used instead, thus decreasing the perimeter and detectability of your LAN; be creative.
When deploying a wireless network inside a tall building, use ground plane omnis to make your LAN less “visible” from the lower floors and streets. The ground plane reflects the downward signal, thus cutting the bottom of the omni irradiation “doughnut.”
Position your indoor omnis in the center of a corporate building. If deploying a wireless LAN through a long corridor linking multiple offices, consider using two panel antennas on the opposite ends rather than an array of omnis along the corridor.
Take into account antenna polarization. If the majority of client device antennas are positioned horizontally (such as built-in PCMCIA wireless card antennas), position your omni- or semidirectional antenna horizontally as well. CF wireless card and built-in microchip Bluetooth antennas have vertical polarization. The wardrivers’ favorite, the magnetic mount omni, is always positioned vertically using the car as a ground plane. If your access point’s antennas have horizontal polarization, the possibility of wardrivers picking up your signal with the magnetic mount omni is decreased.
Yagis are frequently deployed in medium-range point-to-point bridging links, while highly directionals are used when long-range point-to-point connectivity is required. Highly directional antennas are sometimes used to blast through obstacles such as thick walls. Please note that crackers can also use highly directional dishes to blast through the thick wall of a corporate building, or even through a house that lies in the way to the targeted network. They can also be used to reach targeted networks 20–25 miles away from the top of a hill or a tall building, which makes tracing such a cracker a hard task. On the other hand, at least three highly directional antennas are necessary to triangulate transmitting attackers in order to find their physical position.
TIP If you are an IT professional seriously interested in wireless security, consider getting a narrow beam width (8 degrees or less) high-gain directional dish/grid antenna alongside other wireless LAN/PAN testing equipment.
One way of controlling your wireless signal spread is, as we just described, correct antenna positioning. Another method is adjusting the transmitter power output to suit your networking needs and not the crackers’. To do this, understanding the concept of gain is essential.
Gain is one of the fundamental RF terms, which has already been referred to several times. Gain describes an increase in RF signal amplitude, as shown in Figure 13-3.
There are two ways to achieve gain. Focusing the beam with an antenna increases the signal amplitude: more narrow beam width means higher gain. Contrary to popular belief, omnidirectional antennas can possess significant gain reached by decreasing the vertical beam width (squeezing the coverage “doughnut” into a coverage “pancake”). Alternatively, external DC power fed into the RF cable (so-called “phantom voltage”) can be injected by the means of an amplifier to increase gain. While the antenna’s direction and position influence where the signal will spread, gain affects how far it will spread by increasing the transmitting power of your wireless devices.
FIGURE 13-3 Radio frequency signal gain is an increase of the signal’s amplitude.
The transmitting power output is estimated at two points of a wireless system. The first point is the intentional radiator (IR), which includes the transmitter and all cabling and connectors but excludes the antenna. The second point is the power actually irradiated by the antenna, or equivalent isotropically radiated power (EIRP). Both IR and EIRP output are legally regulated by the FCC (see Part 47 CFR, Chapter 1, Section 15.247) or ETSI in Europe. To measure the power of irradiated energy (and the receiving sensitivity of your wireless device), watts (more often milliwatts [mW]) or decibels are used. Power gain and loss (the opposite of gain; decrease in signal amplitude) are estimated in decibels or, to be more precise, dBm. The “m” in dBm signifies the reference to 1 mW: 1 mW = 0 dBm. Decibels have a logarithmic relationship with watts: Pdbm = 10 log pmW. Thus, every 3 dB would double or halve the power, and every 10 dB would increase or decrease the power by an order of magnitude. The receiving sensitivity of your wireless devices would be affected in the same way. Antenna gain is estimated in dBi (“i” stands for “isotropic”), which is used in the same manner as dBm in RF power calculations.
TIP If you deal with wireless networking, it is essential to familiarize yourself with RF power calculations. To make life easier, there are many RF power calculators including online tools such as those found at these addresses:
www.zytrax.com/tech/wireless/calc.htm
www.ecommwireless.com/calculations.html
www.csgnetwork.com/communicateconverters.html
http://rf.rfglobalnet.com/software_modeling/software/14/local/dbcalculator.htm?GoButton=Go+Now!
www.vwlowen.demon.co.uk/java/games.htm
www.satcomresources.com/index.cfm?do=tools&action=eirp
As you immerse yourself more and more in wireless technology, you will find the collection of tools at these sites very useful.
TIP Security is about control. Try to get wireless access points, bridges, and even client devices (for example, Cisco Aironet PCMCIA 802.11b cards) with regulated power output. This will make controlling the signal spread area much easier to achieve. Alternatively, you can use an amplifier or attenuator with regulated power output. Attenuators are employed to bring the power output back to legally accepted levels. For Bluetooth devices, the most powerful class 1 (20 dBm) transmitters must possess power controls allowing you to decrease the emission at least down to 4 dBm.
The best way to find how high your EIRP should be to provide a quality link without leaving large areas accessible for crackers is to conduct a site survey with a tool capable of measuring the signal-to-noise ratio (SNR, estimated in dB as signal strength minus RF noise floor) and pinging remote hosts. Such a tool could be a wireless-enabled laptop or PDA loaded with necessary software (for example, wavemon), or a specialized wireless site survey device, such as the products offered by Berkeley Varitronics Systems at www.bvsystems.com/Products/WLAN/WLAN.htm.
TIP It is said that 22 dB SNR or more is appropriate for a decent wireless link on 802.11 LANs. The Bluetooth specification defines the so-called Golden Receive Power Range: an incoming signal power should lie in the range between –56 dBm and the receiver sensitivity value + 6 dBm.
You can estimate EIRP and loss mathematically before running the actual site survey, taking into account the events depicted in Figure 13-4.
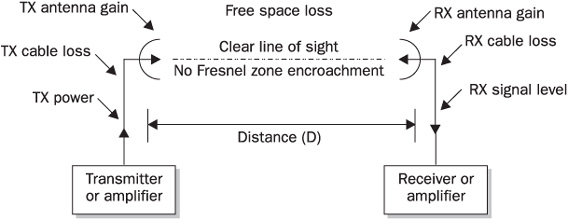
FIGURE 13-4 Wireless link power gain and loss
Free space path loss is the biggest cause of energy loss on a wireless network. It happens due to the radio wave front broadening/transmitted signal dispersion (think of a force decreasing when it is applied to a larger surface area). Free space path loss is calculated as 36.56 + 20 log10 (frequency in GHz) +20 log10 (distance in miles). The Fresnel zone in Figure 13-4 refers to a set of specific areas around the line of sight between two wireless hosts. You can try to envision it as a set of elliptical spheres surrounding a straight line between two wireless transmitters, building a somewhat rugby ball–shaped zone along this line. The Fresnel zone is essential for wireless link integrity, since any objects obstructing this zone by more than 20 percent introduce RF interference and can cause signal degradation or even complete loss. At its widest point, the radius of the Fresnel zone can be estimated as
43.3 × • (link distance in miles/(4 × signal frequency in GHz))
Free space path loss and Fresnel zone online calculators are available at the web sites already mentioned when referring to RF power output calculations. In the real world, the power loss between hosts on a wireless network is difficult to predict, due to the likely objects in the Fresnel zone (for example, trees or office walls) and the interaction of radio waves with these objects and other entities in the whole area of coverage. Such interactions can include signal reflection, refraction, and scattering (see Figure 13-5).
Apart from weakening the signal, these interactions can leak out your network traffic to unpredicted areas, making discovery of the network more likely and giving potential crackers the opportunity to eavesdrop on network traffic where no one expects the traffic’s (and the attackers’) presence.
FIGURE 13-5 Electromagnetic wave-object interactions
NOTE Any experienced “wardriver” knows how a dozen of new wireless LANs may “pop up” on a network discovery tool interface when a road crossing is passed in a large city center. Radio waves flow along the streets, getting reflected from the houses on the sides, sneak through narrow gaps between houses, and bend around their corners. A lonely reflected beacon frame is an “animal” often seen in dense urban areas. It can give a cracker (or just a curious individual) an indication of some rather “interesting” network to find and investigate. The interest can be caused by the network ESSID, the access point vendor OUI, or other information it may carry.
Wave-object interactions are strongly dependent on the wavelength/frequency. When the dimensions of an object are very large compared to the wavelength, the reflection will occur. Otherwise, wave scattering is likely. Modern wireless networks operate in the middle ISM (Industrial/Scientific/Medical; 2.4–2.5 GHz, or 12.5–12.0 cm wavelength) band or the UNII (Unlicensed National Information Infrastructure, 5.15–5.35 and 5.725–5.825 GHz, or 5.8–5.6 and 5.24–5.15 cm) band. Because of the FCC power specifications, only the 2.4–2.4835 GHz range is actually used for wireless networking in the ISM band. Original 802.11, 802.11b, and 802.11g wireless LANs and Bluetooth PANs operate in the middle ISM band, whereas the UNII band is used by 802.11a networks. FCC rules specify a maximum 4 watt EIRP for point-to-multipoint 2.4–2.5 GHz links. However, the Bluetooth Special Interest Group (SIG) restricts maximal Bluetooth emissions to 100 mW. Point-to-point 2.4–2.5 GHz links have a variable EIRP limit: the accepted power output increases with the gain of the antenna, but for every 3 dBi above the initial 6 dBi gain, the IR power must be reduced by 1 dB. The IR limit for both point-to-point and point-to-multipoint links on the middle ISM band is 1 ![]() . The regulations for UNII frequencies are a bit more complex, since there are three different bands in the UNII spectrum. The lower UNII band (5.15–5.25 GHz) is reserved for indoor operations and limited by FCC to a maximum 50 mW EIRP. The middle UNII band (5.25–5.35 GHz) can be used for both indoor and short-range outdoor links; users are allowed to emit 250 mW (FCC). The upper UNII band (5.725–5.825 GHz) is limited to 1 W EIRP and used for outdoor links. Interestingly, the IEEE has imposed further limits on the UNII EIRP, decreasing the FCC-defined emission limits by 20 percent. Thus, the IEEE-defined maximum lower UNII band output is 40 mW; the middle UNII band output is 200 mW; and the upper UNII band output is 800 mW. If the IEEE-imposed EIRP limit is exceeded but EIRP stays in the FCC-defined range, the law is not broken, but the network would be considered to be noncompliant by IEEE standards.
. The regulations for UNII frequencies are a bit more complex, since there are three different bands in the UNII spectrum. The lower UNII band (5.15–5.25 GHz) is reserved for indoor operations and limited by FCC to a maximum 50 mW EIRP. The middle UNII band (5.25–5.35 GHz) can be used for both indoor and short-range outdoor links; users are allowed to emit 250 mW (FCC). The upper UNII band (5.725–5.825 GHz) is limited to 1 W EIRP and used for outdoor links. Interestingly, the IEEE has imposed further limits on the UNII EIRP, decreasing the FCC-defined emission limits by 20 percent. Thus, the IEEE-defined maximum lower UNII band output is 40 mW; the middle UNII band output is 200 mW; and the upper UNII band output is 800 mW. If the IEEE-imposed EIRP limit is exceeded but EIRP stays in the FCC-defined range, the law is not broken, but the network would be considered to be noncompliant by IEEE standards.
While you may wonder what the relationship is between legal limitations on acceptable wireless power output and wireless security, the answer is simple: you don’t want to be a major source of interference in your area and join the same side of the law as the crackers. Besides, crackers are not limited by the FCC—if one is going to break the law anyway, why care about FCC rules and regulations? This will be an important point when reviewing layer 1 DoS (jamming) and layer 1 man-in-the-middle attacks on wireless networks. While a wireless systems administrator cannot “outpower” crackers exceeding the legal power limits, other measures such as a wireless IDS capable of detecting layer 1 anomalies like sudden RF power surges or signal quality failures on the monitored network can alleviate the problem.
Before discussing the issues of interference, jamming, and safe wireless networks coexistence, it is important to grasp the basic concepts of spread spectrum communications. Spread spectrum refers to wide-frequency low-power transmission, as opposed to narrowband transmission, which uses just enough spectrum to carry the signal and has a very large SNR (see Figure 13-6).
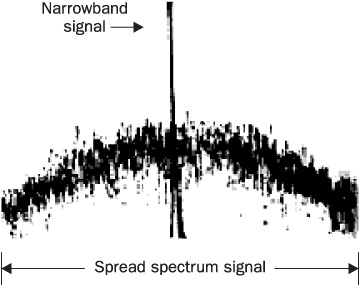
FIGURE 13-6 Spread spectrum versus narrowband transmission
All 802.11 and 802.15 IEEE standards–defined wireless networks employ spread spectrum band technology. This technology was originally developed during World War II, with security being the primary development aim. Anyone sweeping across the frequency range with a wideband scanner who doesn’t know how the data is carried by the spread spectrum signal and which particular frequencies are used will perceive such a signal as white noise. Using spread spectrum technology in military communications is a good example of “security through obscurity” that actually works and is based on very specific equipment compatibility. In everyday commercial and hobbyist wireless nets, however, this obscurity is not possible. The devices used must be highly compatible, interoperable, and standard-compliant (in fact, interoperability is the main aim of WECA “WiFi” certification for wireless hardware devices, which many confuse with the IEEE 802.11b data-link layer protocol standard). Besides, when the link between communicating devices is established, a variety of parameters such as communication channels have to be agreed upon, and such agreement is done via unencrypted frames sent by both parties. Anyone running a wireless sniffer can determine the characteristics of a wireless link after capturing a few management frames off the air. Thus, the only security advantage brought to civil wireless networks by implementing spread spectrum technology is the heightened resistance of these networks to interference and jamming as compared to narrowband transmission.
Two ways are commonly implemented of using spread spectrum:
• Frequency hopping spread spectrum (FHSS)
• Direct sequence spread spectrum (DSSS)
In FHSS, a pseudorandom sequence of frequency changes (hops) is followed by all hosts participating in a wireless network (see Figure 13-7).
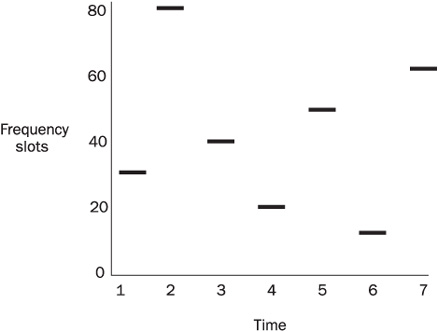
FIGURE 13-7 FHSS frequency hopping
The carrier remains at given frequency for a dwell time period, then hops to another frequency (spending a hop time to do it); the sequence is repeated when the list of frequencies to hop through is exhausted. FHSS was the first spread spectrum implementation technology proposed. It is used by legacy 1–2 Mbps 802.11 FHSS networks, HomeRF (now a legacy wireless LAN after Intel dropped HomeRF support), and most importantly, 802.15 PANs (Bluetooth). Bluetooth hops 1600 times per second (~625µs dwell time) and must hop through at least 75 MHz of bandwidth in the middle ISM band. As such, Bluetooth is very resistant to radio interference unless the interfering signal covers the whole middle ISM band. At the same time, Bluetooth devices (in particular Class 3 transmitters) introduce wideband interference capable of disrupting 802.11, 802.11b, and 802.11g LANs. Thus, a Bluetooth-enabled phone, PDA, or laptop can be an efficient (unintentional or intentional) wideband DoS/jamming tool against other middle–ISM band wireless networks. As to interference issues arising from using multiple Bluetooth PANs in the same area, it is theoretically possible to keep 26 Bluetooth PANs in the same area due to the different frequency hopping sequences on these networks. In practice, it is not recommended to exceed 15 PANs per area, but the times are yet to come when widespread Bluetooth use will create such density of PANs.
NOTE Check your country’s frequency table in order to see which devices can introduce interference
or be used for jamming of wireless LANs. Frequency allocation tables for the U.S.A. are
available at
www.ntia.doc.gov/osmhome/allochrt.html.
Frequency allocation tables for different European countries can be found at
www.radioregs.co.uk/frequency_allocation.htm.
Devices that use the middle ISM band include cordless phones, baby monitors, microwave ovens,
and certain long-range point-to-point wireless bridges that do not fall under 802.11 standards,
such as Orinoco Lynx or MR2400 T1/E1 radios. In general, you will find less interference or
possible jamming problems using UNII bands.
DSSS combines a meaningful data signal with a high-rate pseudorandom “noise” data bit sequence, designated as processing gain or chipping code (see Figure 13-8).
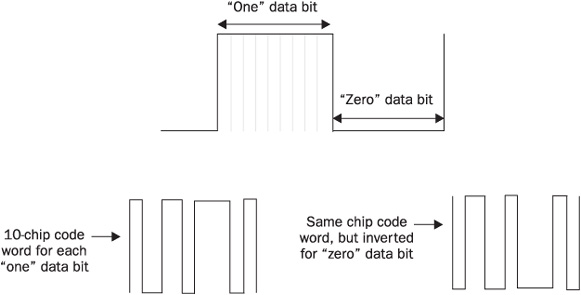
FIGURE 13-8 DSSS data “hiding” and transmission
Legacy 802.11 networks as well as 802.11b-, a-, and g-compliant LANs use DSSS. As compared to FHSS networks (with a maximum 5 MHz–wide carrier frequency), DSSS networks use wider channels (802.11b/g: 22 MHz, 802.11a: 20 MHz), which allow higher data transmission rates. On the other hand, since the transmission on a DSSS network goes through a single 20–22 MHz channel and not the whole ISM/UNII band range or 75 MHz defined by the FCC for FHSS networks, DSSS networks are more vulnerable to interference and jamming. An 802.11b or g LAN would suffer from coallocation with a Bluetooth PAN to a larger extent than the PAN would be negatively affected by the 802.11b/g LAN.
UNII band DSSS channels are split by 5 MHz between the channel “margins;” thus, they do not overlap. On the contrary, middle ISM band DSSS channels are split by the 5 MHz distance between the middle of each channel; thus, severe channel overlapping takes place. The 802.11b/g channel width is 22 MHz, so you need at least five channels ![]() between two non-overlapping channels, or so the theory goes. In reality, even these channels would interfere with each other for a variety of reasons. In the U.S., there are 11 802.11b/g channels to use, and thus the maximum number of coallocated access points is three, taking channels 1, 6, and 11, as the following illustration of the 802.11b/g frequency channels allocation shows.
between two non-overlapping channels, or so the theory goes. In reality, even these channels would interfere with each other for a variety of reasons. In the U.S., there are 11 802.11b/g channels to use, and thus the maximum number of coallocated access points is three, taking channels 1, 6, and 11, as the following illustration of the 802.11b/g frequency channels allocation shows.
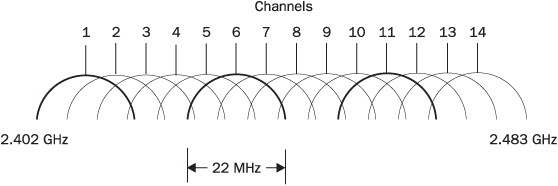
In Europe, 13 channels are allocated for 802.11b/g use, making access point coallocation more flexible (however, only the channels from 10 to 13 are used in France, and 10 to 11 in Spain). All 14 channels can be used in Japan. Channel allocation has high relevance to the much-discussed issue of rogue access points. There are different definitions of a “rogue access point” and thus different ways of dealing with the problem:
• Access points/bridges that belong to neighboring LANs and interfere with your LAN by operating on the same or overlapping channels.
Solution: Be a good neighbor and reach agreement with other users on the channels used so that they do not overlap. Ensure that your data is encrypted and an authentication mechanism is at place. Advise your neighbors to do the same if their network appears to be insecure.
Note that interference created by access points operating on close channels (such as 6 and 7) is actually higher than interference created by two access points operating on the same channel. Nevertheless, two or more access points operating on the same channel do produce significant signal degradation. Unfortunately, many network administrators who do not understand the basics of RF tend to think that all access points belonging to the same network or organization must use the same channel—in my experience as senior network security analyst for Arhont LTD, these cases are seen on a nearly daily basis.
• Access points, bridges, USB adapters, and other wireless devices installed by users without permission from enterprise IT management.
Solution: Have a strictly defined ban on unauthorized wireless devices in your corporate security policy and be sure that all employees are aware of the policy contents. Detect wireless devices in the area by using wireless sniffers such as Kismet (GPL, Linux and BSD), dstumbler (GPL, BSD), Sniffer Wireless, AiroPeek, or LinkFerret (commercial, Windows), or specific wireless tools/appliances (IBM Wireless Security Auditor, Berkeley Varitronics 802.11 analysis devices, Network Chemistry Neutrino, WildPackets RFGRabber or Red-M Sensors). Remove discovered unwanted devices and check if the traffic that originated from such devices produced any alerts in logs.
• Access points or other wireless devices installed by intruders to provide a back channel into the corporate LAN, effectively bypassing egress filtering on the company firewall.
Solution: This is a physical security breach and should be treated as such. Apart from finding/removing the device and analyzing logs (as in the preceding point), treat the rogue device as serious evidence. Handle it with care to preserve attackers’ fingerprints, place it into a sealed bag, and label the bag with a note showing the time of discovery as well as the credentials of the person who sealed it (see Chapter 29 to find more about incident response procedures). Investigate if someone has seen the potential intruder and check the information provided by CCTV.
• Outside wireless access points/bridges employed by crackers to launch man-in-the-middle attacks.
This is a “red alert” situation and indicates skill and determination on the part of the attacker. The access point can be installed in the attacker’s car and plugged into the car accumulator battery, or the cracker could be using it from a neighboring flat or hotel room. Alternatively (and more comfortably for an attacker), a PCMCIA card can be set to act as an access point using HostAP drivers for Prism II chipset cards (http://hostap.epitest.fi/links.html) or experimental HermesAP drivers for Hermes/Orinoco cards (www.hunz.org/hermesap.html) under Linux or employing HostAP mode implemented with ifconfig/wiconfig/anconfig in various BSD flavors. A cracker of this type is likely to be very familiar with *nix and networking and possess a collection of custom packet generation, traffic capture, and connection hijacking software, along with vulnerability finding tools and exploit code on the laptop or PDA acting as a rogue access point. An attacker going after the public hot spot may try to imitate the hot spot user authentication interface using Shmoo Group Airsnarf or similar utilities in order to capture login names and passwords of unsuspecting users. In the forthcoming book, Wi-Foo: The Secrets of Wireless Hacking (Addison-Wesley, 2003), members of the Arhont LTD wireless security team discuss such attacks and how to defend your network against them (on a How-To level).
Solution: Above all, such attacks indicate that the assaulted network was wide open or data encryption and user authentication mechanisms were bypassed. Deploy your wireless network wisely, implementing security safeguards described later in the chapter. If the attack still takes place, consider bringing down the wireless network and physically locating the attacker. To achieve the latter aim, contact a specialized wireless security firm capable of attacker triangulation.
The design of data-link layer protocols and associated security features for wireless communications was determined by peculiarities of physical layer operations, as well as the expected wireless network topology and size. Unfortunately, the reality rarely meets the designer’s expectations. Security for infrared links relies on the limited spread of the IR signal, which cannot penetrate walls and requires direct line of sight to communicate. Thus, no security features are implemented on layer 2 of IR links, and hacking IR networks was considered to be both improbable and impossible. Wireless LANs were initially developed for limited-size networks and short-to-medium point-to-point bridging links. Now we can see wireless LANs spanning large corporations for whom the original security features implemented by 802.11a/b standards (WEP and WEP-based or “closed” authentication) are clearly insufficient. On the contrary, Bluetooth is a relatively late specification (introduced in 1999) that has well-thought-out security safeguards. No practically implemented specific attack against Bluetooth protocols exists, even though Bluetooth “warphoning” tools are currently under development. However, Bluetooth devices are user-end products, usually operated by nontechnical customers who may not be aware of the built-in security features and are likely to have them turned off by accident.
We will briefly review layer 2 operations of commonly used wireless networks such as 802.11 LANs and Bluetooth PANs. Despite a common use of the term “wireless Ethernet” and “ethX,” wireless interface designation under Linux (when Cisco Aironet or Orinoco drivers are used), the data-link layer on 802.11a, b, and g networks is quite different from Ethernet frames, as Figure 13-9 demonstrates.
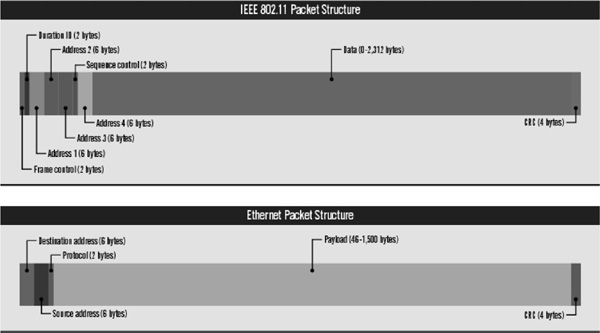
FIGURE 13-9 Comparison between 802.11 and 802.3 frames
The mode of operation of wireless LANs is also dissimilar to that of Ethernet. Because a radio transceiver can only transmit or receive at a given time on a given frequency, all 802.11-compliant networks are half-duplex. While an access point is a translational bridge in relation to the wired network it may be connected to, for wireless network clients it acts as a hub, making packet sniffing an easy task. Since detecting collisions on a wireless network is not possible, the CSMA/CA (Carrier Sense Media Access/Collision Avoidance) algorithm is used on wireless LANs instead of the Ethernet’s CSMA/CD. CSMA/CA is based on receiving a positive ACK for every successfully transmitted frame and retransmitting data if the ACK frame is not received. On wired networks, by plugging the cable in, you are associated with the network. On wireless nets, this is not possible, and exchange of association request/response frames followed by exchanging authentication request/response frames is required. Before requesting association, wireless hosts have to discover each other. Such discovery is done by means of passive scanning (listening for beacon frames sent by access points or ad hoc wireless hosts on all channels) or active scanning (sending probe request frames and receiving back probe responses). If a wireless host loses connectivity to the network, exchange of reassociation, request, and response frames takes place. Finally, a deauthentication frame can be sent to an undesirable host.
Bluetooth wireless PANs can function in circuit-switching (voice communications) and packet-switching (TCP/IP) modes, which can be used simultaneously. In packet-switched mode, connection is asynchronous, with a maximum speed of 721 Kbps. In the circuit-switching mode, a synchronous flow of 64 Kbps is established. The Bluetooth stack is more complicated than its 802.11 counterparts, spanning all the OSI model layers (see Figure 13-10).
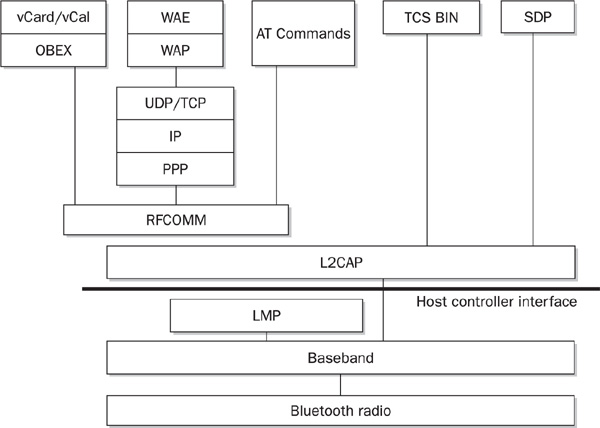
FIGURE 13-10 Bluetooth protocol stack
LMP (the Link Manager Protocol) is responsible for setting up the link between two Bluetooth devices. It includes deciding and controlling the packet size, as well as providing security services such as authentication and encryption using link and encryption keys. L2CAP (the Logical Link Control and Adaptation Protocol) is responsible for controlling the upper-layer protocols. RFCOMM is a cable replacement protocol that interfaces with the core Bluetooth protocols. SDP (the Service Discovery Protocol) is present so that Bluetooth-enabled devices can gather information about device types, services, and service specifications to set up the connection between devices. Finally, there are a variety of application-layer protocols such as TCS BINARY and AT Commands; these are telephony control protocols that allow modem and fax services over Bluetooth. There are 15 types of Bluetooth management frames, which are not reviewed here due to the limitations of the chapter. A good source of information on Bluetooth functionality is Bluetooth: Operation and Use by Robert Morrow (McGraw-Hill Professional, 2002).
The main problem with layer 2 wireless protocols is that in both 802.11 and 802.15 standards, the management frames are neither encrypted nor authenticated. Anyone can log, analyze, and transmit them without necessarily being associated with the target network. While intercepting management frames is not the same as intercepting sensitive data on the network, they still can provide a wealth of information, including network ESSIDs, wireless hosts’ MAC addresses, DSSS LAN channels in use, FHCC frequency hop patterns, and so on. Every Bluetooth device has a unique ID transmitted in clear text in the management frames. Thus, eavesdropping on these frames can be helpful in tracking such a device and its user. This is hard to prevent, short of turning the Bluetooth device off or using a Bluetooth “TEMPEST bag” (www.mobilecloak.com/bluetooth/bluetooth.html).
TIP Never use a meaningful ESSID. Using a company or organization name as an ESSID attracts attackers’ attention and helps them to locate your network physically. There are people who use various service/host passwords and WEP keys as ESSIDs—unfortunately, this is not a joke. Don’t leave a default ESSID value, either. Crackers assume that LANs with default ESSIDs have other default settings as well and consider these to be easy prey. In the majority of cases, this assumption is correct. In addition, default ESSIDs (the most common one these days appears to be “linksys”) help attackers to identify the access point manufacturer (so does the MAC address in captured management frames). Some access points have known security flaws/misconfigurations in default settings (e.g., default SNMP communities containing usernames and passwords). Crackers could be well aware of such flaws and look for the particular access point brands to exploit them.
Unfortunately, the information presented by management frames is only a tiny fraction of the problem. By sending deauthenticate and disassociate frames, the attacker can easily knock wireless hosts offline. Even worse, the attacker can insert his machine as a rogue access point by spoofing the real access point’s MAC and IP addresses, providing a different channel to associate, and then sending a disassociate frame to the target host(s). All these tasks can be performed by using Abaddon’s/xx25’s AirJack driver/tool suite for Prism chipset 802.11b client cards (http://802.11ninja.net/airjack/) already mentioned in relation to man-in-the-middle attacks, or the WNET custom wireless frames generation suite for OpenBSD from Dachb0den Labs (www.dachb0den.com/). Currently, the author is not aware of any similar tools to attack Bluetooth PANs, but no doubt they will appear in the near future as the technology becomes more available.
Which layer 2 countermeasures against data snooping, DoS, and identity spoofing attacks are implemented by wireless LAN and PAN standards, and can they be bypassed?
Data encryption and client authentication for 802.11a, 802.11b, and currently released 802.11g devices can be handled using the Wired Equivalent Privacy standard, or WEP (see Figure 13-11). WEP encrypts the payload and CRC of each frame using symmetric streaming cipher RC4 (www.rsasecurity.com/rsalabs/faq/3-6-3.html).
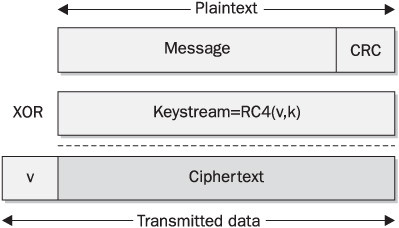
FIGURE 13-11 An overview of WEP
The initial WEP shared key length was 64 bits to comply with U.S. export regulations, but nowadays the majority of wireless hosts use 128-bit keys. WEP can be used to authenticate wireless hosts if the shared key authentication method is enabled. Shared key authentication occurs when the access point sends a challenge nonce to the authenticating client. The client responds by encrypting the nonce and sending it back to the access point. The access point decrypts the nonce with its WEP key and compares it with the initial value to make a decision on host authentication.
NOTE The default authentication method on 802.11 networks is open system authentication. It is a null authentication method enabling any host to join the wireless network as long as both the channel and the ESSID are correct. The ESSID value of “ANY” will make the authenticating host join a network with that network’s ESSID. This feature can usually be disabled at the access point, preventing “ANY” hosts from joining. Disable it. Also, many access points (including Linux and BSD HostAP modes) support “mixed authentication mode,” where shared key authentication is used where possible; otherwise, open key authentication applies. While it appears to be sensible to use shared key authentication only, you will soon find out that shared key authentication does not provide a significant security advantage and in fact may help the attackers to obtain the WEP key.
Unfortunately, as you are probably aware, a variety of security flaws in WEP are now well known and exploited by the underground. The problems with WEP can be split into two categories:
All symmetric cipher implementations suffer key distribution problems, and WEP is no exception. In its original design, WEP was supposed to protect limited-size LANs. Wireless networks of today can involve thousands of hosts, making manual distribution and change of WEP keys a serious problem.
WEP provides device-based, not user-based, authentication. A lost/stolen 802.11-enabled laptop or PDA opens network access for anyone taking possession of the device.
All users on the LAN have the same WEP key. Sniffing a wireless LAN is as easy as sniffing a shared Ethernet, and besides, slightly more advanced attackers can hijack connections and spoof ARP requests using well-known tools such as Hunt, Dsniff, and Ettercap. These attacks can be launched against the hosts on a connected wired network (remember that an access point is a bridge, not a router) as well as against the wireless hosts. Remember that internal malcontents present as much threat as external crackers, if not more. Employees on the wireless network sharing the same WEP key belong to the same data domain, even if the network is split on different IP subnets.
NOTE Capture using RFMON mode on a wireless LAN associated with “wireless sniffing” is different from using the promiscuous mode on Ethernet. An attacker does not have to be associated/authenticated with the network under surveillance. Thus, tools like L0pht’s AntiSniff would not discover a wireless network eavesdropper. In fact, there isn’t a known way to find out if your wireless LAN has been sniffed. The majority of PCMCIA/CF wireless cards do not actively scan when in raw frames capturing mode; thus, detecting eavesdroppers in the area by listening for probe request frames is not possible (Cisco Aironet cards do continue active scanning when in raw frame capturing mode, but since they have regulated power output, the attacker can easily decrease the IR to 1 mW, restricting the area over which probe requests are spread).
A WEP key consists of the actual shared key and a 24-bit initialization vector (IV) which is transmitted over the network unencrypted. In modern cryptographic terms, 24 bits is a very small number. Eventually, the same IV will be used for different data packets and key streams will become similar. After collecting enough frames with the same IV, an attacker can determine the shared secret. Of course, it makes sense to look for all repeating IVs, rather than a particular IV value, in the wireless LAN traffic. These repeated IVs are often called “interesting” or “weak.”
Common nonstandard wireless LAN safeguards include closed system ESSIDs, MAC address filtering, and protocol filtering.
Closed-system ESSID is a feature of many higher-end wireless access points and bridges. It refers to the removal of ESSID from the beacon frames and/or probe response frames, thus requiring the client hosts to have a correct ESSID in order to associate. This turns ESSID (basically, a network name) into a form of shared authentication password. However, closed-system ESSIDs can be found in management frames other than beacons and probe responses. Just as in the case of shared key authentication mode, wireless hosts can be forced to deassociate in order to capture the ESSID in the management frames’ underlying reassociation process. By using essid_jack from the AirJack suite or custom deassociation/deauthentication frames crafted using WNET, attackers can easily circumvent closed-system ESSID security. Kismet is capable of seamless closed-system ESSID detection by parsing all management frames on the monitored network for the ESSID value.
Unlike closed-system ESSIDs, MAC filtering is a common feature that practically every modern access point supports. Obviously, it does not provide data confidentiality and is easily bypassed (again, a cracker can force the target host to deassociate without waiting for the host to go offline so that its MAC address can be assumed). Nevertheless, MAC filtering may stop “script kiddie”–type attackers from associating with the network.
Finally, protocol filtering is less common than closed systems and MAC address filtering; it is useful only in specific situations and when it is sufficiently selective. For example, when all that the wireless hosts need is web and mail traffic, all other protocols can be filtered and HTTPS and S/MIME used to provide a sufficient degree of data confidentiality. Alternatively, SSH port forwarding can be used. Protocol filtering combined with secure layer 6 protocols can provide a good security solution for wireless LANs built for handheld users with low–CPU power devices limited to a specific task (barcode scanning, browsing the corporate web sites for updates).
As compared to the 802.11 networks of today, Bluetooth PANs may appear to be more secure. Bluetooth has a well-thought-out security mechanism covering both data authentication and confidentiality. This mechanism relies on four entities: two 128-bit shared keys (one for encryption and one for authentication), a 128-bit random number generated for every transaction, and a 48-bit IEEE public address (BD_ADDR) unique to each Bluetooth device. Setting up a secure Bluetooth communication channel involves five steps:
1. An initialization key is generated by each device using the random number, BD_ADDR, and shared PIN.
2. Authentication keys (sometimes called a “link key”) are generated by both ends.
3. The authentication keys are exchanged using the initialization key, which is then discarded.
4. Mutual authentication via a challenge-response scheme takes place.
5. Encryption keys are generated from authentication keys, BD_ADDR, and a 128-bit random number.
Streaming cipher E0 is used to encrypt data on Bluetooth PANs. A modification of the SAFER+ cipher is used to generate the authentication keys. Three Bluetooth security modes are known: insecure mode 1, service-level security mode 2, and link-level enforced security mode 3. Mode 3 is the most secure and should be used where possible.
We have already discussed the defense issues related to physical and RF security of wireless networks. In this section, we outline data-link layer countermeasures against the possible abuse of your wireless LAN. These countermeasures include
• Secure replacements for WEP
• Proper wireless user authentication
• Intrusion detection and anomaly tracking on wireless LANs
Of course, the security of wireless networks can (and should) also be provided using higher-layer safeguards such as various IPSec modes or SSL-based secure protocols. The reader is referred to the corresponding chapters of this book to learn more about these network defense technologies.
Since the vulnerabilities of WEP have become well known and are routinely exploited by crackers, the main hope for a wireless security community lies with 802.11i standard development. The “i” IEEE task group is expected to produce a new unified wireless security standard by the end of this year (even though the author has doubts that the group will be able to implement what they claim by that time). In the meantime, parts of the future 802.11i and accompanying 802.1x standards are implemented by many wireless equipment and software manufacturers (e.g., Orinoco in its AP-2000 access point, or Belkin in its 54g Wireless Router) in order to mitigate the known 802.11 problems before 802.11i arrives.
The 802.11i architecture can be split on two “layers:” encryption protocols and 802.11x port-based access control protocols. TKIP (the Temporal Key Integrity Protocol) and CCMP (the Counter Mode with CBC-MAC Protocol) are 802.11i encryption protocols designed to replace WEP on 802.11 LANs. TKIP is “an upgrade to WEP” that addresses all known WEP insecurities. It uses 48-bit IVs to avoid IV reuse (estimated 100 years key reuse time) and does per-packet key mixing of the IVs in order to introduce additional key confusion (reducing relationship of the statistical composition between the ciphertext and the key value). It also implements a one-way hash message integrity code (MIC or Michael) checksum instead of the insecure CRC-32 used for WEP integrity check vector (ICV) computation. TKIP is not mandatory for 802.11i implementations, is backward compatible with WEP, and does not require hardware upgrade. Together with 802.1x, TKIP is the basis for the first version of WPA (WiFi Protected Access) certification by the WiFi Alliance (www.wifialliance.com/OpenSection/protected_access.asp) currently supported by many wireless vendors.
By contrast, CCMP has to be supported by default when 802.11i eventually rolls out. CCMP uses the Advanced Encryption Standard (AES, Rijndael) cipher in a counter mode with cipher block chaining and message authenticating code (CBC-MAC). The AES key size defined by the 802.11i standard is 128 bit. Like TKIP, CCMP implements 48-bit IV (called “packet number,” or PN) and MIC. Since hardware implementation of AES is planned to reduce the impact of encryption on network speed/throughput, a major 802.11 hardware change is expected when 802.11i-supporting products hit the market. The second version of WiFi Alliance WPA certification is expected to be released after 802.11i is finalized and to incorporate the majority of security features developed by the “i” task force.
The 802.1x standard was originally designed to implement layer 2 user authentication on wired networks. On wireless networks, 802.1x can also be used for the dynamic distribution of WEP keys. Since there are no physical ports on wireless LANs, an association between the wireless client and the access point is assumed to be a network access port. In terms of 802.1x, the wireless client is defined as a “supplicant” (or “peer”), and the access point, as an “authenticator” (in a manner similar to an Ethernet switch on wired LANs). Finally, there is a need for an authentication server on the wired network segment to which an access point is connected. This service is usually provided by a RADIUS server supplied with some form of user database, such as native RADIUS, LDAP, NDS, or Active Directory. High-end wireless gateways can implement the authentication server, as well as the authenticator functionality. Figure 13-12 gives an overview of the 802.1x and TKIP implementation on a pre-802.11i secure wireless LAN. TKIP replaces WEP and repels AirSnort/dwepcrack–using attackers, while the traditional open, shared, or mixed 802.11 authentication is replaced by 802.1x/RADIUS, which also provides TKIP (or even old WEP key) rotation. Such a network would be quite secure against contemporary wireless crackers, although it would still be susceptible to layer 1, layer 2, and 802.1x-specific DoS attacks and WEP injection network probing.
FIGURE 13-12 An overview of 802.1x/TKIP functionality
Unfortunately, until the 802.11i standard is finally approved, support of both TKIP and 802.1x as a temporary wireless security solution is provided only on the initiative of manufacturers and may include proprietary features, adding to incompatibility issues. Thus, if you plan to rely on TKIP and 802.1x for your wireless LAN security, it is highly recommended that you use the equipment from a single vendor. This may not be an acceptable solution for public access networks (users bring their own wireless clients, which are likely to be lower-end products with limited security features) or for large corporate networks that are built using a vast variety of wireless equipment, including legacy devices/firmware. In these cases, deployment of higher-layer security protocols (IPSec, SSH, HTTPS, S/MIME) should be considered.
NOTE The 802.1x protocol can be used to distribute “traditional” WEP keys. The problem with such mitigation of the WEP cracking threat lies in predicting the amount of traffic flowing through the wireless network per unit of time in order to determine how often the keys must be redistributed. This prediction is hard to make and would involve many days of attempting to crack the WEP with a variety of tools mentioned earlier at different traffic loads. On the other hand, there is no guarantee that a sudden burst of traffic would not give a potential cracker the opportunity to collect just enough “interesting packets” to get the key before it is changed. Thus, the dynamic distribution of WEP keys may significantly improve your wireless network security, but it is not 100 percent reliable and may require more labor for realistic implementation than expected.
User authentication in 802.1x relies on the layer 2 Extensible Authentication Protocol (EAP, RFC 2284). EAP is an advanced replacement of CHAP under PPP, designed to run over local area networks (EAP over LAN [EAPOL] describes how EAP frames are encapsulated within Ethernet, Token Ring, or FDDI frames). EAP frame exchange between the supplicant, authenticator, and authentication server is summarized in Figure 13-13.
FIGURE 13-13 EAP authentication process
There are multiple EAP types, adding to compatibility problems in 802.1x implementations. These are the most commonly implemented EAP types:
• EAP-MD5 is the base level of EAP support by 802.1x devices. It is the first EAP type that duplicates CHAP operations. Since EAP-MD5 does not provide server authentication, it is vulnerable to “rogue authenticator/authentication server” type of attacks. When choosing 802.1x solutions/products for your wireless network, take care that the authentication is mutual in order to reduce the risk of man-in-the-middle attacks.
• EAP-TLS (Transport Layer Security) provides mutual certificate-based authentication. It is built on the SSLv3 protocol and requires deployed certificate authority. Windows XP supports EAP-TLS natively, while Windows 2000 supports it since the development of Service Pack 2 if the Microsoft 802.1x Authentication Client is installed. Detailed instructions on implementing 802.1x with EAP-TLS on Windows XP/2000 are available at www.microsoft.com/WindowsXP/pro/techinfo/deployment/wireless/80211corp.doc. On Open Source Unix-like operating systems, 802.1x with EAP-TLS can be deployed with Xsupplicant from Open1x Project (www.open1x.org/). Adam Sulmicki has provided a detailed How-To on using Xsupplicant with the FreeRADIUS server. The How-To can be found at www.missl.cs.umd.edu/wireless/eaptls/.
• EAP-LEAP (Lightweight EAP or EAP-Cisco Wireless) is a Cisco-proprietary EAP type, implemented on Cisco Aironet access points and wireless clients. A wealth of information on configuring EAP-LEAP is provided by Cisco at www.cisco.com/warp/public/707/accessregistrar_leap.html. EAP-LEAP is commonly provided, and its support in the latest versions of FreeRADIUS indicates that the method has became more than a single-vendor proprietary protocol. Unfortunately, EAP-LEAP uses modified MS-CHAPv2 with insecure MD4 hashing and weak DES key selection for challenge/response procedures. Thus it is susceptible to optimized dictionary attacks as implemented by Joshua Wright’s Asleap-imp LEAP attack tool. Take care that you choose really strong passwords when using EAP-LEAP and rotate the passwords on a regular basis.
• Other, less frequently encountered types of EAP include PEAP (Protected EAP, an IETF draft standard) and EAP-TTLS (Tunneled Transport Layer Security EAP developed by Certicom and Funk Software). EAP-TTLS supports multiple legacy authentication methods, including PAP, CHAP, MS-CHAP, MS-CHAPv2, and EAP-MD5. To use these methods in a secure manner, EAP-TTLS creates an encrypted TLS tunnel inside of which the less secure legacy authentication protocol operates. EAP-PEAP is similar to EAP-TTLS but does not support less secure authentication methods such as PAP and CHAP. Instead, it employs PEAP-MS-CHAPv2 and PEAP-EAP-TLS inside of the secure TLS tunnel. Both EAP-TTLS and EAP-PEAP require server-side certificate only, and a copy of the server certificate is commonly distributed to clients with the supplicant software. EAP-PEAP is currently actively promoted by Microsoft, Cisco, and RSA Security and implemented by the Cisco Wireless Security Suite. Both EAP-TTLS and EAP-PEAP are supported by the Funk Software Odyssey 802.1x authentication suite and Steel-Belted Radius.
NOTE Proprietary solutions are currently on the market that implement per-session and per-packet WEP key generation and are not linked to 802.1x key distribution. Per-session WEP key generation significantly improves wireless network security, but a lucky cracker may still stumble upon a long and traffic-intensive session and get the key. Per-packet key generation is theoretically uncrackable but very resource-consuming: would the typical PDA 206 MHz StrongARM CPU be able to handle generating/employing a new key with every packet sent? There are also frequent cases of manufacturers expanding the size of a WEP key beyond 104 bits (232-bit WEP is the most common example). However, it is the IV, not the actual shared secret size, that is the main problem with WEP, and increasing the size of the shared secret does not significantly enhance the network security. A simple recommendation: if you run AirSnort and see “interesting packets” on your wireless network, do not consider your WEP implementation secure.
Bottom line: while there are interesting developments in the field of WEP-related threat mitigation, until 802.11i is finally approved and has been widely implemented, compatibility, pricing, and other issues may well force network administrators and managers to seek their wireless security answers on OSI layers above the data link (e.g., IPSec deployment).
The preceding points notwithstanding, intrusion detection on wireless networks should always cover the data-link layer. The principles of intrusion detection are outlined in the Chapter 14. Here we will briefly cover wireless-specific IDS issues. Many applications claim to be wireless IDS systems but detect new MAC addresses on a LAN only as long as these addresses are not permitted by an ACL. Such functionality is implemented in firmware of some access points as well. Of course, anyone able to bypass MAC-based ACL will bypass MAC-based “IDS.” A true wireless IDS is a dedicated 802.11 (or 802.15) protocol analyzer supplied with an attack signature database or knowledge base and inference engine, as well as an appropriate report/alarm interface. Some suspicious events to look for on a wireless LAN include
• Probe requests (a good indication of someone using NetStumbler, MiniStumbler, or dstumbler in active scanning mode)
• Beacon frames from unsolicited access points or ad hoc wireless clients
• Floods of deassociate/deauthenticate frames (man-in-the-middle attack?)
• Associated but not authenticated hosts (attempts to guess the shared key?)
• Frequent reassociation frames on networks without enabled roaming, and frequent packet retransmits (“hidden node,” bad link, or possible DoS attack?)
• Multiple incorrect ESSIDs on closed networks (ESSID brute-forcing?)
• Suspicious ESSIDs such as “AirJack” (or plain old “31337”)
• Frames with unsolicited and duplicated MAC addresses
• Randomly changing MAC addresses (crackers using Wellenreiter or FakeAP)
• Frames transmitted on other 802.11b/g channels within the five-channel range, or frames with different ESSIDs transmitted on the same channel (misconfigured and probably unsolicited host, interference, DoS?)
• Hosts not using implemented cryptographic solutions (should not be there)
• Multiple EAP authentication requests/responses (brute-forcing EAP-LEAP?)
• Malformed/oversized EAP frames and various EAP frame floods (802.1x DoS attack?)
• 802.11 frame sequence numbers that don’t match the established sequence cycle (man-in-the-middle attacks, MAC spoofing on LAN?)
• ARP spoofing and other attacks originating from wireless LANs
The types of IDS software capable of performing these tasks are rather limited; they include WiSentry (www.wimetrics.com/products.php) and Network Associates’ Sniffer Wireless Expert system (www.networkassociates.com/us/products/sniffer/wireless/sniffer_wireless.htm). On the Open Source side of the fence, Kismet (while being the wireless crackers’ favorite) enables stateful packet inspection, discovery of Netstumbler users (labeled as “N” on a Kismet console), and deassociating/deauthenticating frame floods. The client/server structure of Kismet is a great advantage, since it allows you to deploy multiple monitors across the network perimeter with a centralized IDS server collecting the information from such monitors. A more specialized Open Source wireless IDS program is WIDZ, available from www.loud-fat-bloke.co.uk/tools.html. The current WIDZ version runs using HostAP Prism II drivers and is capable of discovering and logging AirJack man-in-the-middle attacks, netstumbling probes, null probes, and layer 2 floods. Wireless network monitors can be old inexpensive wireless-enabled PCs, laptops, or even PDAs, running the network monitoring software. Alternatively, a few wireless security companies, such as Red-M, Network Chemistry, and WildPackets offer remote wireless IDS sensors that send captured 802.11 packets as a UDP stream to an analyzing monitor host. The WSP100 Network Chemistry Neutrino sensor is supported by Kismet; see the kismet.conf file for the sensor configuration details. The Red-M sensor has an additional capability of detecting the presence of Bluetooth traffic in the monitored area. The WildPackets sensor is integrated with the WildPackets AiroPeek protocol analyser (www.wildpackets.com/products/airopeek_nx), as one would expect.
On the high corporate end, there are very efficient hardware wireless IDS/monitoring solutions, including AirDefense Guard and ActiveDefense from Airdefense (www.airdefense.net/products/index.html) and Isomair Wireless Sentry from the UK-based firm Isomair (www.isomair.com/products.html). These devices, when connected to a specialized, centralized monitoring/analysis server can be dispatched across the whole wireless network perimeter and provide constant 24×7 network monitoring, with automatic wireless-specific attacks detection, logging, and intruder isolation from the monitored LAN.
The final point to be made about wireless network hardening is related to the position of the wireless network in the overall network design topology. Due to the peculiarities of wireless networking, described earlier in this chapter, under “Radio Frequency Security Basics,” wireless networks should never be directly connected to the wired LAN. Instead, they must be treated as an insecure public network connection or, in the most lax security approach, as a DMZ. Plugging an access point directly into the LAN switch (not to mention hub) is asking for trouble (even though implemented 802.1x authentication can alleviate the problem). A secure wireless gateway with stateful or proxy firewalling capability must separate the wireless network from the wired LAN. If the wireless net includes multiple access points across the area and roaming user access, the access points on their “wired side” must be put on the same VLAN, securely separated from the rest of the wired network. Higher-end specialized wireless gateways combine access point, firewalling, authentication, VPN concentrator, and user roaming support capabilities. Such gateways include the Bluesocket WG family (www.bluesocket.com/solutions/index.html) for 802.11 and Bluetooth network access, Colubris wireless LAN routers and public access controllers (www.colubris.com/en/products/), AiroPoint 3600 Security Server (www.leappoint.com/airopoint.htm), AirFortress gateways, clients, and access control servers (www.fortresstech.com/products/), and EliteConnect WLAN Secure Server (www.smc.com/). Alternatively, a secure gateway can be designed from scratch by using hardened Open Source systems such as the NSA SElinux or OpenBSD, HostAP drivers/functionality, and a variety of Unix security tools (FreeRADIUS, FreeS/WAN, iptables, ipf, free wireless IDS software tools already mentioned, signal strength monitoring tools such as Wavemon [www.wavemage.com/projects.html], and so forth). Security of the gateway protecting your wireless network or even the security of an access point per se should never be underestimated. The majority of security problems with wireless gateways, access points, and bridges stem from insecure device management implementations, including using telnet, TFTP, default SNMP communities, and default passwords, as well as allowing gateway/access point remote administration from the wireless side of the network. Ensure that the devices’ security is properly audited and use wireless-specific IDS features in concert with more traditional intrusion-detection systems working above the data-link layer.
To summarize, wireless security is a multilayered time- and resource-consuming process, which is nevertheless absolutely essential because wireless networks are a highly prized target for attackers looking for anonymous free Internet access and backchannel entry into otherwise securely separated networks. Wireless security encompasses wireless-specific security policy (many tips in this chapter are helpful in constructing one), radio frequency security, layer 2 specific wireless protocol security issues and solutions, higher-layer VPN and device management security, and above all, correct wireless network design with security in mind. Good luck.