Traffic IQ Pro is proprietary software by the company Karalon (http://www.karalon.com). This tool tests inline security devices such as firewall and IPS. It runs on Windows only, and requires two network cards to take advantage of all its features.
Traffic IQ Pro provides more than a graphical interface. It comes with exploits and attacks captures ready to replay, a complete packet with editor the ability to know whether packets reached their destination, and a reporting system to test several packet captures.
Traffic IQ Pro uses the concept of internal and external machines. Each physical network card is associated with a virtual machine. The requests are sent from the internal machine to the external machine; replies go from the external machine to the internal machine.
Tip
You can use the same IP address for both the internal and the external machine, but the packets will not go out on the wire. This is useful to make a packet capture of the attack files with Ethereal/Wireshark (see Ethereal/Wireshark), since there is no export function in Traffic IQ Pro.
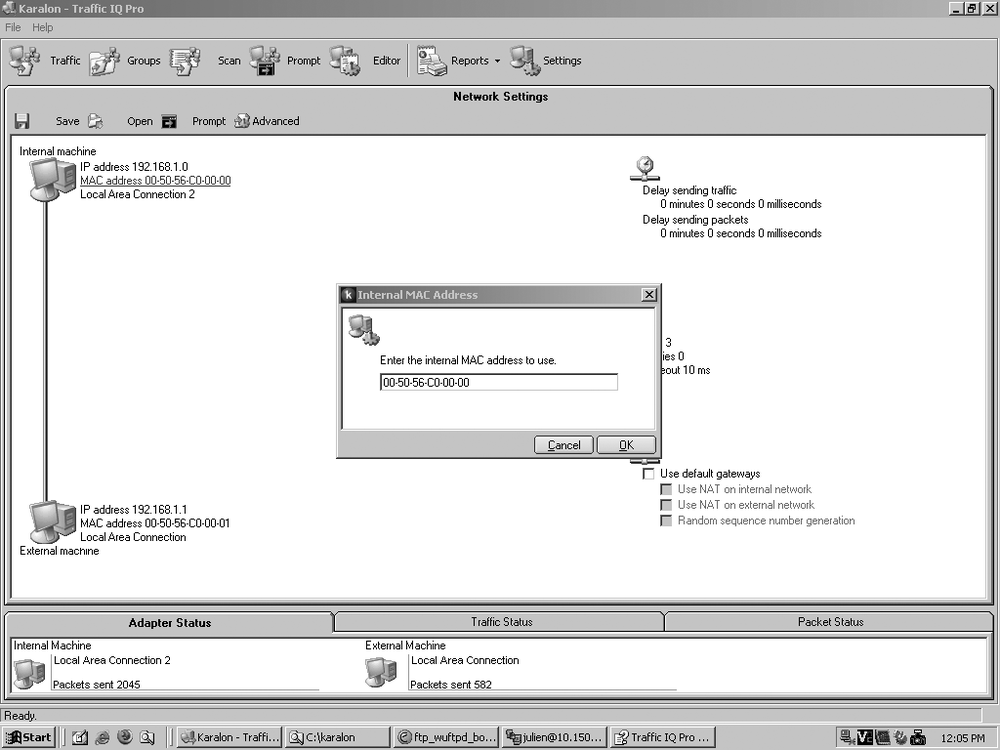
Each machine has a MAC address and an IP address that you can change. The IP address of each machine is redefined when you replay traffic. If the interfaces are not connected directly to an inline device, but to an actual network, you can define default gateways with their IP addresses and MAC addresses. See Figure 17-2.
Tip
The MAC addresses for the virtual machines should be different from the physical card addresses. If you need to put the same MAC address as the physical Ethernet card, you need to disable the IP stack for this card.
Do not forget to change the TTL, timeout, and retries number. These values are used when replaying traffic:
- TTL
Put the Time To Live to
0to use the default TTL from the traffic file.- Retry
The number of times a packet should be resent before giving up.
- Timeout
The default timeout before resending a packet.
If the device to test is directly connected to the Windows PC that hosts Traffic IQ Pro, you can leave the TTL at 0. But if your PC is part of a real network and you need to traverse several network devices, you should set it to a high value to make sure all packets live long enough to reach their destination.
A test is defined as failed when one packet does not reach its destination; e.g., when a request sent from the internal machine does not reach the external machine. The timeout defines how much delay is accepted, and the retries specifies how many times the packet should be sent before the test is deemed to have failed. If the device is not stressed, the retry number should be set to 0, and the timeout can be left at 10 ms. If you are stressing the device while replaying traffic files, you should allow one to three retries at least.
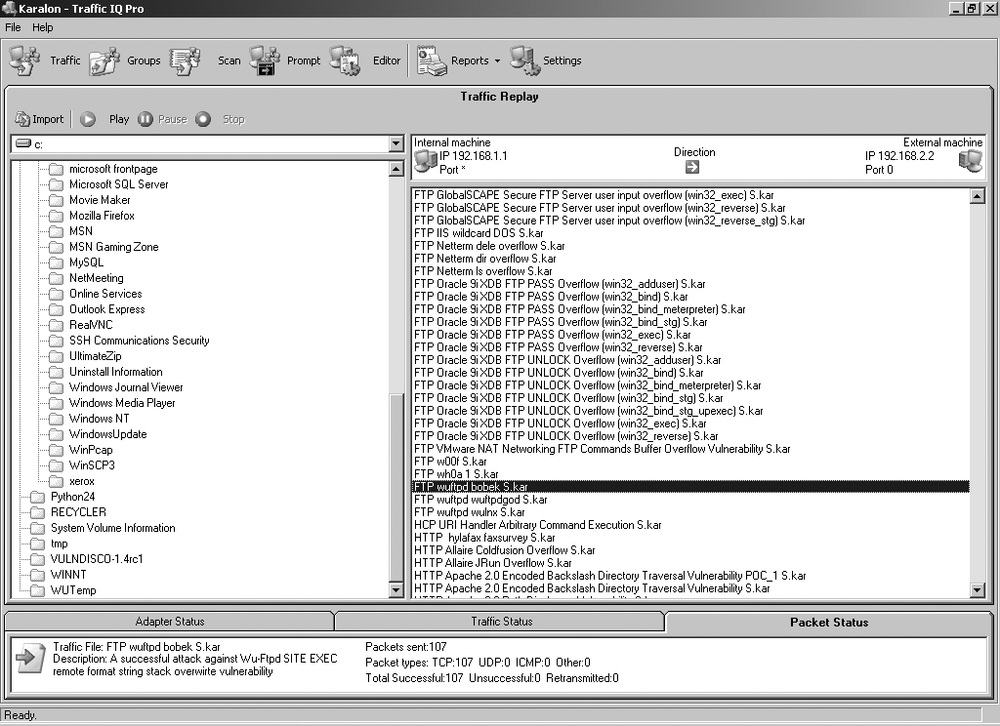
Traffic IQ Pro comes with traffic to replay. Several updates a year are released by Karalon with additional traffic. There are two types of traffic files:
- Attacks
Used to test an IPS or the advanced detection mechanisms of a firewall, as shown in Figure 17-3.
- Clean traffic
Useful to test whether a firewall can detect protocols on nonstandard ports.
The TTL, retries number, timeout, and MAC addresses defined in the setup are kept when replaying a traffic file. But the IP addresses, port numbers, and direction are chosen in the Traffic Window and can be changed easily for each run.
I usually keep the same IP addresses for all my tests. You can add some randomness by using the wildcard * in the IP address; e.g., 192.168.1.* or *.*.*.*.
The destination port number is usually set to 0 to replay the traffic file on the default server port. However, you can change it to a different value to verify that the IPS can detect attacks on nonstandard ports. The source port is usually *, a random number.
The results of each test are displayed in the bottom pane and include information on the number of packets sent, the number of packets retransmitted, the type of packets (UDP, TCP, ICMP, Other), and the packets blocked.
The traffic files can be displayed as a flat list in alphabetical order in the Traffic view, or by categories in the Group view. The traffic file structure is custom to Karalon. These files have a .kar extension. It is not possible to directly replay a tcpdump format file—you have to import it first. This is explained in later in this chapter in the section "Import Custom Packet Captures".
Traffic files are a great value from Karalon, but their quality can be irregular. They have attacks generated by good tools such as Nessus (see Nessus) and Metasploit (Chapter 7), so you do not have to set up and configure these tools. But the backdoor group contains several very old backdoors that do not work on a modern computer (e.g., Subseven) and very obscure Trojans that were probably never seen in the wild, while some other exploits are simply incorrect and do not work. In September 2006, they released a lot of exploits from FunBrowser that crashed Internet Explorer, but without possible code execution. This is the kind of thing that typically should not be covered by IPS vendors.
Tip
Some traffic files do not actually contain the attack described. For example, the traffic file "HTTP IE MHTML File Multiple Property NULL Dereference S.kar" released in the September 2006 update is incorrect. The attack should be in the HTML sent back by the HTTP server. But the writer of this file probably went back to the FunBrowser exploit a first time and then a second time. He must have done the packet capture the second time because the web page was all ready in case the server answered "304 Not Modified" and did not send back the HTML page containing the exploit.
Attacks are a good start to verify the coverage of an IPS. But we are aware that the security devices vendors probably possess Traffic IQ Pro too, so a good coverage of the Traffic IQ Pro attacks does not necessarily translate to a good coverage in general. If the IPS catches most of the Spyware/Malware group, you can be sure the vendor is using Traffic IQ Pro extensively. To my knowledge, Karalon does not release zero-day exploits, so all attacks are well known when Karalon releases them in an update; thus, it is not possible to test the response time of the vendor's security team.
The most valuables attacks are, I believe, in the Metasploit group as well as the attacks against Microsoft products in the Exchange, Internet Explorer, HTTP, and RPC groups.
Tip
Some attacks exist as Successful exploit (S) and Unsuccessful (U). An IPS should detect both of them; it cannot wait to see whether the attack is successful to block the traffic, as this would be too late to block it.
Also, most of the Metasploit exploits exist with different shellcode. The shellcode is executed after the vulnerability is exploited. The IPS should detect the attack against the vulnerability, not the shellcode used. All the traffic files seeking the same vulnerability should be detected the same way by the IPS.
Most attacks are described in a help file. There is no direct link between the traffic file and the corresponding entry in the help file, making it inconvenient to go back and forth from the attack file to its description.
Traffic IQ Pro contains clean traffic: DHCP, DNS, HTTP, SMTP, IMAP, and so on. I find it useful to test firewalls. For example, you can run all these traffic files on port 80, usually open to give access to the Web, to see whether the firewall lets only the real HTTP traffic go through.
These files can also be used to verify how the IPS works. If you run SSH on port 80, will it parse it as HTTP and trigger a lot of false positives, or will it process it as SSH? Can it block non-HTTP traffic on port 80? Peer-to-peer traffic such as BitTorrent and chat traffic such as Skype are seen on all ports and can trigger several false positives on IPSes that are not able to distinguish between several protocols running on the same port.
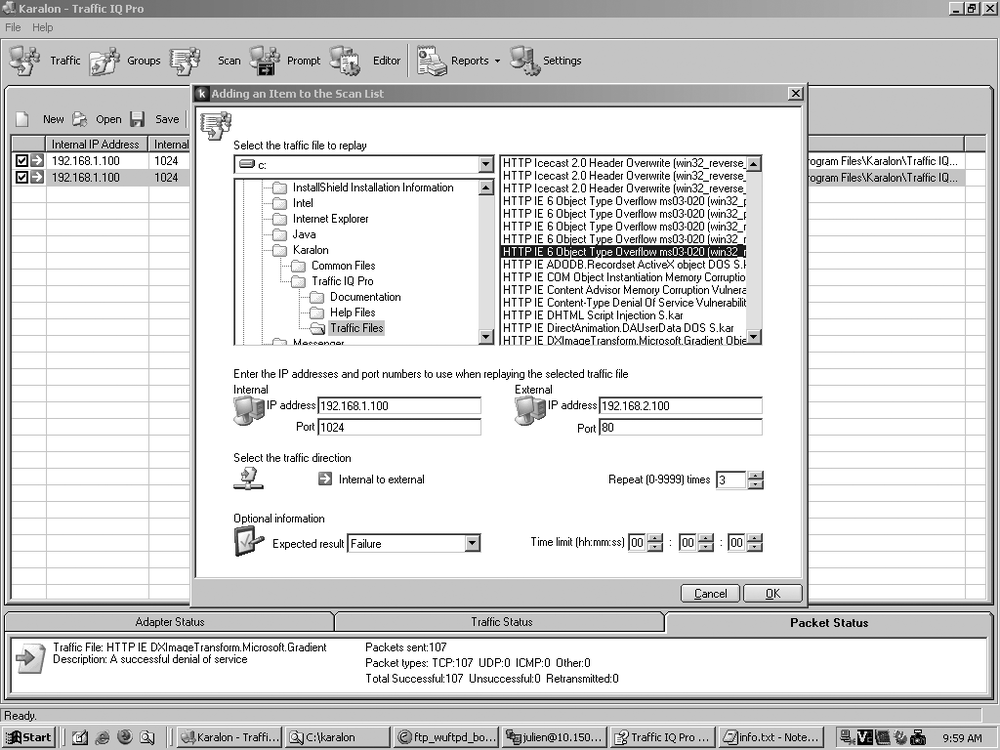
To run a set of tests, use the Scan feature, as shown in Figure 17-4. For each test, you can define the IP addresses and ports, the number of times to repeat the test, and whether all packets are expected to go through.
It is convenient to test a couple of traffic files in a row. You can select several tests by holding the Ctrl key or consecutive files with the Shift key.
Tip
If all or most of your tests have the same values (random source port, default destination port, same IP addresses, and same expected result), do not make the changes for each file you select. Rather, use the default value, then right-click on the list of tests and choose Select All. Right-click again on the selection, and then from the pop-up menu, select Actions → Change Values and choose what values to change. This will save you a lot of time. Remember to save your traffic scan.
You can get a report of the scan by clicking on report. It is automatically saved. The report is cumulative; all traffic files replayed are added to the report until you clear it. It is better to clean the report before starting the scan.
You can also import your own packet capture into Traffic IQ Pro. The software can handle packet captures in the libpcap format, captures by tcpdump (see "tcpdump"), or Ethereal/Wireshark (see Using Wireshark and Ethereal/Wireshark). The imported traffic keeps the same name as the original file, but with the .kar extension. Then you can do all the neat traffic modifications available on the regular traffic files, such as changing the destination port.
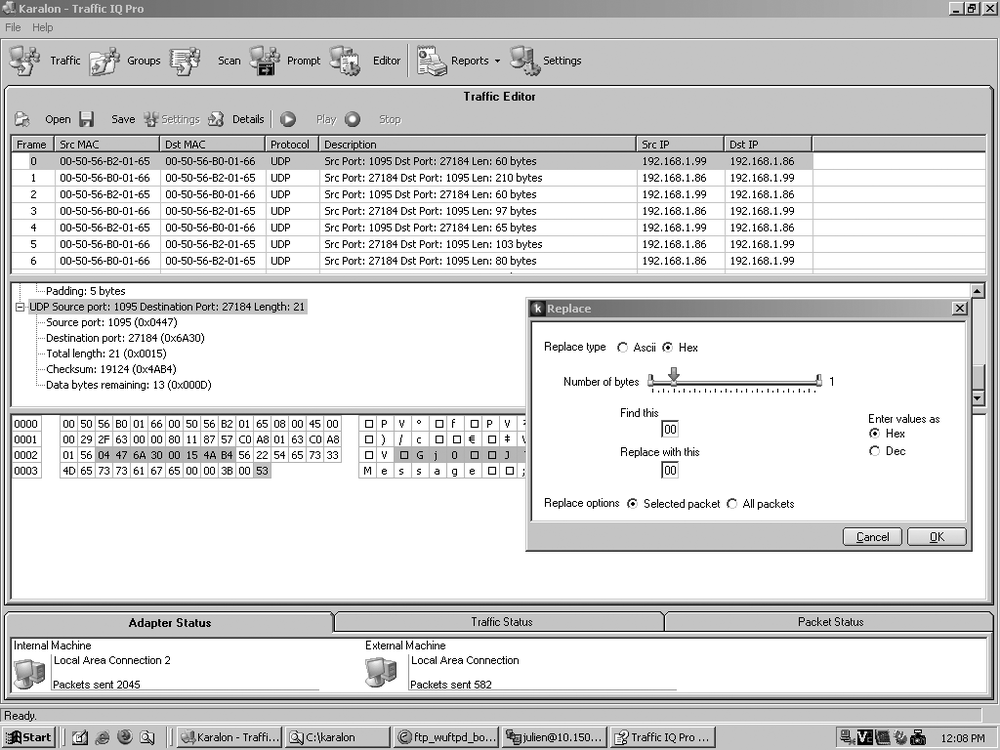
Traffic IQ Pro offers some packet-editing capabilities, as shown in Figure 17-5, but it is not as powerful as Netdude (see pcap Utilities: tcpflow and Netdude). You can do modifications on layers 2 to 7. Unlike Netdude, you do not need to fix the checksums after editing the packets. The checksums are always recalculated every time Traffic IQ Pro sends a packet. Note that you can only edit existing bytes; it is not possible to add extra data to the packets.
Tip
Layer 2 contains the source and destination MAC addresses. It does not make sense to edit them. Change the general setup instead to override the MAC addresses.
Traffic IQ Pro is a good tool for replaying traffic. It is easy to use and allows interesting packet modifications, such as changing the port number. But when it comes to attack files, you cannot fully trust the software. If an IPS does not catch a malicious traffic file, some work on your side is needed to determine whether:
It actually makes sense to detect this type of traffic–for example, crashing Internet Explorer without being able to execute malicious code is not interesting.
The exploit is actually contained in the traffic files.
The exploit is correct. One of the WMF exploits, for example, does not contain the correct offset that triggers the vulnerability.
Karalon also sells Traffic IQ Basic, a light version of Traffic IQ Pro but many times cheaper. This version cannot import custom packet captures, does not contain all the traffic files of the Pro version, nor is it possible to change the source and destination port number. All settings, such as the MAC addresses of the network cards, are configured by modifying an .ini text file—they are not available through the GUI. For a company that needs such a tool for demonstrations, it might make sense to buy one license of Traffic IQ Pro to generate the traffic files, and multiple licenses for Traffic IQ Basic to replay these files at different locations.